Designing Trusted Operating Systems Operating Systems
... Chapter 5 – Designing Trusted Operating Systems ...
... Chapter 5 – Designing Trusted Operating Systems ...
Web server software
... Also called safeguards, protections, and controls Types of countermeasures ...
... Also called safeguards, protections, and controls Types of countermeasures ...
Operating System - Linux - Home Pages of People@DU
... terminated Different from BIOS which is hardware dependent. Kernel is software dependent ...
... terminated Different from BIOS which is hardware dependent. Kernel is software dependent ...
Network Security Analysis Prepared By: cowave Communication
... Regularly make security updates to protect from ...
... Regularly make security updates to protect from ...
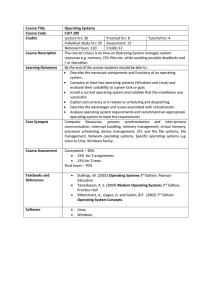
Course Title Operating Systems Course Code CUIT 109 Credits
... Credits 12 The course’s focus is on how an Operating System manages system resources e.g. memory, CPU files etc, while avoiding possible deadlocks and / or starvation. By the end of the course students should be able to : Describe the necessary components and functions of an operating system. Co ...
... Credits 12 The course’s focus is on how an Operating System manages system resources e.g. memory, CPU files etc, while avoiding possible deadlocks and / or starvation. By the end of the course students should be able to : Describe the necessary components and functions of an operating system. Co ...
Orange Book Summary - UMBC Center for Information Security and
... Protected operating system and system operations mode. Periodic integrity checking of TCB. Tested security mechanisms with no obvious bypasses. Documentation for User Security. Documentation for Systems Administration Security. Documentation for Security Testing. TCB design documentation. Typically ...
... Protected operating system and system operations mode. Periodic integrity checking of TCB. Tested security mechanisms with no obvious bypasses. Documentation for User Security. Documentation for Systems Administration Security. Documentation for Security Testing. TCB design documentation. Typically ...
Final Year Project Electronic & Computer Engineering
... What is a Live CD Purpose of a Live CD for this Project Progress with the creation of custom CD Problems Solutions ...
... What is a Live CD Purpose of a Live CD for this Project Progress with the creation of custom CD Problems Solutions ...
CS111—Operating System Principles
... then available for 80386-class machines, led to a resolve to implement a complete, full featured, POSIX-compliant, UNIX-like kernel, one that would draw from the best of BSD and System V while avoiding their worst flaws. Linux developed this kernel up to version 0.02 by himself, at which point it wa ...
... then available for 80386-class machines, led to a resolve to implement a complete, full featured, POSIX-compliant, UNIX-like kernel, one that would draw from the best of BSD and System V while avoiding their worst flaws. Linux developed this kernel up to version 0.02 by himself, at which point it wa ...
Curriculum Vitae
... ASM, C++ 3D Puzzle Solver – SDL & OpenGL – Linux & Windows C++ Gphoto ’s driver for the Kodak EZ200 camera (reverse engineer of the protocol) C++ Simple image viewer with lots of small features – SDL & OpenGL – Linux C++ Implementation of Ukkonen ‘s algorithm to build suffix tree in linear time – Li ...
... ASM, C++ 3D Puzzle Solver – SDL & OpenGL – Linux & Windows C++ Gphoto ’s driver for the Kodak EZ200 camera (reverse engineer of the protocol) C++ Simple image viewer with lots of small features – SDL & OpenGL – Linux C++ Implementation of Ukkonen ‘s algorithm to build suffix tree in linear time – Li ...
Mgt 20600: IT Management
... as part of PC blades – Fit into a chassis that can be centrally managed – Several users can share a single blade – Simplifies PC management ...
... as part of PC blades – Fit into a chassis that can be centrally managed – Several users can share a single blade – Simplifies PC management ...
CSNB334 Advanced Operating Systems Course Introduction
... The theory part of this course focuses on design issues of the Linux operating system. The course uses the theoretical knowledge learned in the prerequisite course CSNB224/CCSB234 Operating System Concepts. The practical part of the course ◦ Will take you on the programming tasks of writing code ...
... The theory part of this course focuses on design issues of the Linux operating system. The course uses the theoretical knowledge learned in the prerequisite course CSNB224/CCSB234 Operating System Concepts. The practical part of the course ◦ Will take you on the programming tasks of writing code ...
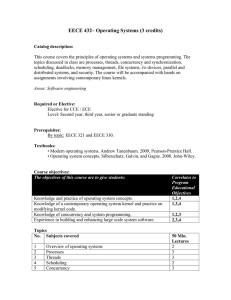
EECE 432– Operating Systems
... Students will work in teams to finish three projects. The first and second project will consist on modifying the kernel of an operating system to customize a specific behavior. The third project is to examine a case study or build a module from scratch where students get exposed and focus on one sp ...
... Students will work in teams to finish three projects. The first and second project will consist on modifying the kernel of an operating system to customize a specific behavior. The third project is to examine a case study or build a module from scratch where students get exposed and focus on one sp ...
Linux Introduction - Personal Web Pages
... Designed to emulate its features Commercial and proprietary work-a-likes Even versions based on the licensed UNIX source code – May be so “Unix-like” they are certified to bear the “UNIX” trademark ...
... Designed to emulate its features Commercial and proprietary work-a-likes Even versions based on the licensed UNIX source code – May be so “Unix-like” they are certified to bear the “UNIX” trademark ...
Operating System Security
... – Cryptographic: hiding data, so that other users cannot understand them ...
... – Cryptographic: hiding data, so that other users cannot understand them ...
Shawn Bracken - CISSP103 Chester StMenlo Park, CA 94025
... 1999 to 2000, Senior Security Research Engineer, Network Associates, Santa Clara, CA. Discovered and documented vulnerabilities in software packages/operating systems Created and examined new methods/concepts of information security Wrote advisories that were released and posted within the sec ...
... 1999 to 2000, Senior Security Research Engineer, Network Associates, Santa Clara, CA. Discovered and documented vulnerabilities in software packages/operating systems Created and examined new methods/concepts of information security Wrote advisories that were released and posted within the sec ...
Systems Security
... A. Objectives: The basic computer infrastructure, ranging from consumer desktops to business servers are under continual attack from a variety of miscreants (or “hackers”) for both fun and monetary gain. The design of computer systems have allowed many vulnerabilities to exist and the attacks exploi ...
... A. Objectives: The basic computer infrastructure, ranging from consumer desktops to business servers are under continual attack from a variety of miscreants (or “hackers”) for both fun and monetary gain. The design of computer systems have allowed many vulnerabilities to exist and the attacks exploi ...
Chapter 2 Operating System Overview
... – Each server runs outside the kernel, protected from other servers ...
... – Each server runs outside the kernel, protected from other servers ...
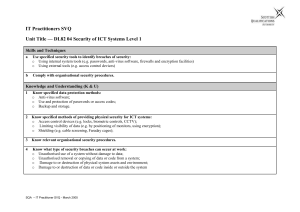
it user svq – level 2
... Know what type of security breaches can occur at work: o Unauthorised use of a system without damage to data; o Unauthorised removal or copying of data or code from a system; o Damage to or destruction of physical system assets and environment; o Damage to or destruction of data or code inside or ou ...
... Know what type of security breaches can occur at work: o Unauthorised use of a system without damage to data; o Unauthorised removal or copying of data or code from a system; o Damage to or destruction of physical system assets and environment; o Damage to or destruction of data or code inside or ou ...
Lecture 15 Designing Trusted Operating Systems Thierry Sans
... but rather a collection of protection mechanisms ...
... but rather a collection of protection mechanisms ...
Answers to Even-Numbered Exercises
... Linux distributions, such as Red Hat Linux, include many utilities. You can also download many utilities from the Internet. Examples of utilities are cp (copies a file), ls (lists information about files), ssh (securely connects to a remote computer), and df (lists information about free space on sy ...
... Linux distributions, such as Red Hat Linux, include many utilities. You can also download many utilities from the Internet. Examples of utilities are cp (copies a file), ls (lists information about files), ssh (securely connects to a remote computer), and df (lists information about free space on sy ...
Answers to Even-numbered Exercises
... distributions, such as Ubuntu Linux, include many utilities. You can also download many utilities from the Internet. Examples of utilities are cp (copies a file), ls (lists information about files), ssh (securely connects to a remote computer), and df (lists information about free space on system de ...
... distributions, such as Ubuntu Linux, include many utilities. You can also download many utilities from the Internet. Examples of utilities are cp (copies a file), ls (lists information about files), ssh (securely connects to a remote computer), and df (lists information about free space on system de ...