Chapter 05
... The level of trust a system provides. Address hardware software and firmware. Trusted Path: communication channel. Trusted Shell: can’t bust out of it. Processes have their own execution domain. Memory and I/O protection. ...
... The level of trust a system provides. Address hardware software and firmware. Trusted Path: communication channel. Trusted Shell: can’t bust out of it. Processes have their own execution domain. Memory and I/O protection. ...
SANDS CORP CYBER JOB
... Proof of authorization/eligibility to work in the United States Associate’s degree in Information Systems or equivalent in relevant discipline preferred. Minimum of three years hands on experience configuring and working with Information Technology Systems is preferred. Excellent problem solving ski ...
... Proof of authorization/eligibility to work in the United States Associate’s degree in Information Systems or equivalent in relevant discipline preferred. Minimum of three years hands on experience configuring and working with Information Technology Systems is preferred. Excellent problem solving ski ...
Chapter 4
... - Microsoft Windows (and DOS) - Macintosh OSX - Unix/Linux - Android - Apple iOS many forensics labs will need to have hardware and software to deal with these there may be the occasion to locate hardware/software for an older OS • example OS9 - unix-like OS for 8-bit Motorola 6809 based micros ...
... - Microsoft Windows (and DOS) - Macintosh OSX - Unix/Linux - Android - Apple iOS many forensics labs will need to have hardware and software to deal with these there may be the occasion to locate hardware/software for an older OS • example OS9 - unix-like OS for 8-bit Motorola 6809 based micros ...
Chapter 4
... - Microsoft Windows (and DOS) - Macintosh OSX - Unix/Linux - Android - Apple iOS many forensics labs will need to have hardware and software to deal with these there may be the occasion to locate hardware/software for an older OS • example OS9 - unix-like OS for 8-bit Motorola 6809 based micros ...
... - Microsoft Windows (and DOS) - Macintosh OSX - Unix/Linux - Android - Apple iOS many forensics labs will need to have hardware and software to deal with these there may be the occasion to locate hardware/software for an older OS • example OS9 - unix-like OS for 8-bit Motorola 6809 based micros ...
NETWORK OPERATING SYSTEMS
... Or you can say “System Libraries” are special functions or programs using which application programs or system utilities accesses Kernel's features. These libraries implements most of the functionalities of the operating system and do not requires kernel module's code access rights. Because a kernel ...
... Or you can say “System Libraries” are special functions or programs using which application programs or system utilities accesses Kernel's features. These libraries implements most of the functionalities of the operating system and do not requires kernel module's code access rights. Because a kernel ...
2.4 The service and functions provided by an operating system can
... has several advantages. The system is easier to debug and modify because changes affect only limited sections of the system rather than touching all sections of the operating system. Information is kept only where it is needed and is accessible only within a defined and restricted area, so any bugs ...
... has several advantages. The system is easier to debug and modify because changes affect only limited sections of the system rather than touching all sections of the operating system. Information is kept only where it is needed and is accessible only within a defined and restricted area, so any bugs ...
William Stallings, Cryptography and Network Security 3/e
... hence is secured to withstand this may support 2 or more net connections may be trusted to enforce trusted separation between network connections • runs circuit / application level gateways • or provides externally accessible services ...
... hence is secured to withstand this may support 2 or more net connections may be trusted to enforce trusted separation between network connections • runs circuit / application level gateways • or provides externally accessible services ...
ISA_673-android_presentation_(1) - eee
... • Build Batterymine into Android kernel • Modify code for most-used drivers • Attribute device usage to process where possible • Attribute to “Idle” otherwise. • Pros: Simple, allows for iterative development • Cons: – Requires intimate knowledge of driver code – Hardware dependent – Process ID not ...
... • Build Batterymine into Android kernel • Modify code for most-used drivers • Attribute device usage to process where possible • Attribute to “Idle” otherwise. • Pros: Simple, allows for iterative development • Cons: – Requires intimate knowledge of driver code – Hardware dependent – Process ID not ...
Overview and History
... Linux kernel is original, but full system incorporates existing UNIX software uses many tools developed as part of Berkeley’s BSD operating system, MIT’s X Window System, and the Free Software Foundation's GNU project Linux kernel is distributed under the GNU General Public License (GPL): free t ...
... Linux kernel is original, but full system incorporates existing UNIX software uses many tools developed as part of Berkeley’s BSD operating system, MIT’s X Window System, and the Free Software Foundation's GNU project Linux kernel is distributed under the GNU General Public License (GPL): free t ...
ppt
... • OS is itself an object of access control “Users must not be able to modify the operating system” • Users should be able to use the OS • Users should not be able to misuse the OS ...
... • OS is itself an object of access control “Users must not be able to modify the operating system” • Users should be able to use the OS • Users should not be able to misuse the OS ...
This Article argues that intellectual property law stifles critical
... This Article argues that intellectual property law stifles critical research on software security vulnerabilities. Researchers who discover flaws often face legal threats based on IP claims if they reveal findings to anyone other than the software’s vendor. Externalities and network effects cause ve ...
... This Article argues that intellectual property law stifles critical research on software security vulnerabilities. Researchers who discover flaws often face legal threats based on IP claims if they reveal findings to anyone other than the software’s vendor. Externalities and network effects cause ve ...
Module Operating Systems (Server)
... This module is a balance between theoretical and practical aspects of modern operating systems. The module aims to - further develop the students’ knowledge of operating systems by covering the theory of how modern, multi-user, network operating systems function; in particular the issues of concurre ...
... This module is a balance between theoretical and practical aspects of modern operating systems. The module aims to - further develop the students’ knowledge of operating systems by covering the theory of how modern, multi-user, network operating systems function; in particular the issues of concurre ...
Operating Systems Course Outline
... Operating Systems Course Outline Rationale: Operating systems are central to computing activities. An operating system is a program that acts as an intermediary between a user of a computer and the computer hardware. Two primary aims of an operating systems are to manage resources (e.g. CPU time, me ...
... Operating Systems Course Outline Rationale: Operating systems are central to computing activities. An operating system is a program that acts as an intermediary between a user of a computer and the computer hardware. Two primary aims of an operating systems are to manage resources (e.g. CPU time, me ...
COMP 3410
... 1. Explain the objectives and functions of modern operating systems. 2. Describe how computing resources are used by application software and managed by system software. 3. Describe reasons for using interrupts, dispatching, and context switching to support concurrency in an operating system. 4. Eva ...
... 1. Explain the objectives and functions of modern operating systems. 2. Describe how computing resources are used by application software and managed by system software. 3. Describe reasons for using interrupts, dispatching, and context switching to support concurrency in an operating system. 4. Eva ...
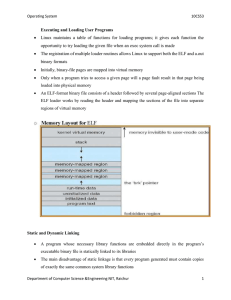
Operating System 10CS53 Executing and Loading User Programs
... o The pluggable authentication modules (PAM) system is available under Linux o PAM is based on a shared library that can be used by any system component that needs to authenticate users o Access control under UNIX systems, including Linux, is performed through the use of unique numeric identifiers ( ...
... o The pluggable authentication modules (PAM) system is available under Linux o PAM is based on a shared library that can be used by any system component that needs to authenticate users o Access control under UNIX systems, including Linux, is performed through the use of unique numeric identifiers ( ...
Computer Science 9616b, Fall 2016 Project Description Your project
... researching a topic and writing a survey/summary of the ideas ...
... researching a topic and writing a survey/summary of the ideas ...
Linux - Rock Fort Networks
... system assembled under the model of free and opensource software development and distribution. The defining component of Linux is the Linux kernel,[9] an operating system kernel first released on 5 October 1991 by Linus Thorvaldsen.[10][11] The Free Software Foundation uses the name GNU/Linux, which ...
... system assembled under the model of free and opensource software development and distribution. The defining component of Linux is the Linux kernel,[9] an operating system kernel first released on 5 October 1991 by Linus Thorvaldsen.[10][11] The Free Software Foundation uses the name GNU/Linux, which ...
Operating System Structures
... Microkernel moves as much from the kernel (e.g., file systems) into “user” space ...
... Microkernel moves as much from the kernel (e.g., file systems) into “user” space ...
Networking & Security
... Source-Destination Addresses at packet level). DNS (Recursive Domain Name Look-up is possible is getting a map of IP addresses and the services each IP station is running). Open TCP ports can be spidered. Internet Control Message Protocol (ICMP) message types can be changed. Network can be flooded w ...
... Source-Destination Addresses at packet level). DNS (Recursive Domain Name Look-up is possible is getting a map of IP addresses and the services each IP station is running). Open TCP ports can be spidered. Internet Control Message Protocol (ICMP) message types can be changed. Network can be flooded w ...
Chapter 2
... Management of the computer’s hardware resources – multiprogramming - single CPU runs two or more programs concurrently • time sharing - special form of multiprogramming in which each user is allotted a time slice ...
... Management of the computer’s hardware resources – multiprogramming - single CPU runs two or more programs concurrently • time sharing - special form of multiprogramming in which each user is allotted a time slice ...
An Introduction to Linux Operating System
... The Linux system excel in many area, ranging from end user concerns such as stability, speed, ease of use, to serious concerns such as development and networking. Linux kernel Linux networking Linux file system ...
... The Linux system excel in many area, ranging from end user concerns such as stability, speed, ease of use, to serious concerns such as development and networking. Linux kernel Linux networking Linux file system ...
CSC 386 Operating Systems Concepts
... COURSE NAME: Operating System Concepts COURSE DESCRIPTION: This course is an introduction to operating system principles. Topics include processor management, real and virtual storage management, device management and scheduling, multiprocessing, concurrent programming, and other topics related to o ...
... COURSE NAME: Operating System Concepts COURSE DESCRIPTION: This course is an introduction to operating system principles. Topics include processor management, real and virtual storage management, device management and scheduling, multiprocessing, concurrent programming, and other topics related to o ...
The most important program that runs on a computer
... The most important program that runs on a computer. Every general-purpose computer must have an operating system to run other programs. Operating systems perform basic tasks, such as recognizing input from the keyboard, sending output to the display screen, keeping track of files and directories on ...
... The most important program that runs on a computer. Every general-purpose computer must have an operating system to run other programs. Operating systems perform basic tasks, such as recognizing input from the keyboard, sending output to the display screen, keeping track of files and directories on ...
ppt 2
... • Due to the intrinsic weakness of hardware structure and the uninsured security status of the OS Security solutions like IDS (Intrusion Detection Systems) and firewalls can claim to carry out secure reinforcement • But internal vulnerabilities seriously impair the external effectiveness ...
... • Due to the intrinsic weakness of hardware structure and the uninsured security status of the OS Security solutions like IDS (Intrusion Detection Systems) and firewalls can claim to carry out secure reinforcement • But internal vulnerabilities seriously impair the external effectiveness ...
AutoPod: Unscheduled System Updates with Zero Data Loss
... with file system stacking to provide each pod with its own file system namespace that can be separate from the regular host file system. Pod virtualization support for migration is based on Zap [2]. Pod virtualization is very light weight, imposing on average less than 10% performance hit on microbench ...
... with file system stacking to provide each pod with its own file system namespace that can be separate from the regular host file system. Pod virtualization support for migration is based on Zap [2]. Pod virtualization is very light weight, imposing on average less than 10% performance hit on microbench ...