PowerPoint
... If secure programming is hard, let’s build tools that make it easier to get security right An approach: enforce defensive coding ...
... If secure programming is hard, let’s build tools that make it easier to get security right An approach: enforce defensive coding ...
Course objectives: 1. To learn the fundamentals of Operating
... directories, File sharing, Record blocking, secondary storage management, File System Security, UNIX file Management. Case Study: Linux system, Design Principles, kernel modules, process management, scheduling, memory management, file system, input and output, inter process communication, network st ...
... directories, File sharing, Record blocking, secondary storage management, File System Security, UNIX file Management. Case Study: Linux system, Design Principles, kernel modules, process management, scheduling, memory management, file system, input and output, inter process communication, network st ...
Slides - CSE
... – The set of labels are defined by trusted administrators – The set of labels are immutable – Protection state, labeling state, and transition state can only be modified by trusted administrators through trusted programs ...
... – The set of labels are defined by trusted administrators – The set of labels are immutable – Protection state, labeling state, and transition state can only be modified by trusted administrators through trusted programs ...
download
... – Replicate functions normally associated with physical documents • eg. have signatures, dates; need protection from disclosure, tampering, or destruction; be notarized or witnessed; be recorded or licensed ...
... – Replicate functions normally associated with physical documents • eg. have signatures, dates; need protection from disclosure, tampering, or destruction; be notarized or witnessed; be recorded or licensed ...
#9305 - Changing The Default Operating System with LILO
... #9305 - Changing The Default Operating System with LILO This document will describe how to change the default bootup operating system. After installing Corel® LINUX® onto its own partition, Linux is the default OS. By default, Corel LINUX will configure LILO (LInux LOader) to be the default OS that ...
... #9305 - Changing The Default Operating System with LILO This document will describe how to change the default bootup operating system. After installing Corel® LINUX® onto its own partition, Linux is the default OS. By default, Corel LINUX will configure LILO (LInux LOader) to be the default OS that ...
Firewall
... potentially exposed to "hostile" elements hence is secured to withstand this may support 2 or more net connections may be trusted to enforce trusted separation between network connections • runs circuit / application level gateways • or provides externally accessible services ...
... potentially exposed to "hostile" elements hence is secured to withstand this may support 2 or more net connections may be trusted to enforce trusted separation between network connections • runs circuit / application level gateways • or provides externally accessible services ...
JAWAHARLAL NEHRU TECHNOLOGICAL UNIVERSITY
... To make the students understand the basic operating system concepts such as processes, threads, scheduling, synchronization, deadlocks, memory management, file and I/O subsystems and protection. To get acquaintance with the class of abstractions afford by general purpose operating systems that a ...
... To make the students understand the basic operating system concepts such as processes, threads, scheduling, synchronization, deadlocks, memory management, file and I/O subsystems and protection. To get acquaintance with the class of abstractions afford by general purpose operating systems that a ...
Chapter 2 Operating System Overview
... memory space than what is available in reality – By storing some of the information on the file system ...
... memory space than what is available in reality – By storing some of the information on the file system ...
Architecting High-Security Systems for Multilateral
... The multilevel-capable workstation allows concurrent access to multiple, completely separated networks from within a single computer. Network traffic originating from the workstation is transparently encrypted and integrity protected employing strong cryptographic algorithms. Each network is accesse ...
... The multilevel-capable workstation allows concurrent access to multiple, completely separated networks from within a single computer. Network traffic originating from the workstation is transparently encrypted and integrity protected employing strong cryptographic algorithms. Each network is accesse ...
Federal Bio
... Hacking course, where he has taught students in both federal agencies and private industry, both in the United States and abroad. Mr. Crane is a contributing author of multiple books, including “SPECIAL OPS: Host and Network Security for Microsoft, UNIX and Oracle”. He is also an adjunct professor i ...
... Hacking course, where he has taught students in both federal agencies and private industry, both in the United States and abroad. Mr. Crane is a contributing author of multiple books, including “SPECIAL OPS: Host and Network Security for Microsoft, UNIX and Oracle”. He is also an adjunct professor i ...
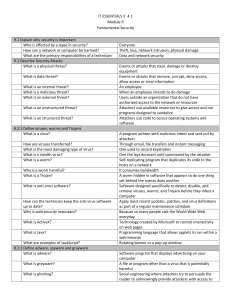
IT ESSENTIALS V. 4.1 Module 9 Fundamental Security 9.1 Explain
... When unsuccessful attempts have been made to access the system; user can no longer access the system Allows remote users to safely access resources as if their computer is physically attached to the local network encryption Data being transported on a network A program that runs on a computer to all ...
... When unsuccessful attempts have been made to access the system; user can no longer access the system Allows remote users to safely access resources as if their computer is physically attached to the local network encryption Data being transported on a network A program that runs on a computer to all ...
Differentiate PC, server, and handheld device operating system
... OS Normal PC. We make low level security. ...
... OS Normal PC. We make low level security. ...
390aLecture01_12wi
... hierarchical file system; "everything" is a file lots of small programs that work together to solve larger problems security, users, access, and groups human-readable documentation included ...
... hierarchical file system; "everything" is a file lots of small programs that work together to solve larger problems security, users, access, and groups human-readable documentation included ...
Alice and Bob Get Physical: Insights into Physical Layer Security
... Although conventional cryptographic security mechanisms are essential to the overall problem of securing wireless networks, these techniques do not directly leverage the unique properties of the wireless domain to address security threats. The properties of the wireless medium are a powerful source ...
... Although conventional cryptographic security mechanisms are essential to the overall problem of securing wireless networks, these techniques do not directly leverage the unique properties of the wireless domain to address security threats. The properties of the wireless medium are a powerful source ...
390Lecture1
... hierarchical file system; "everything" is a file lots of small programs that work together to solve larger problems security, users, access, and groups human-readable documentation included ...
... hierarchical file system; "everything" is a file lots of small programs that work together to solve larger problems security, users, access, and groups human-readable documentation included ...
Linux Systems Programming I
... develop and code several (six-ten) programs of intermediate difficulty and length in the C++ language, including programs broken into several files; 3. adhere to style and documentation standards in writing programs; 4. use system debuggers to step into and over code, set breakpoints and watch varia ...
... develop and code several (six-ten) programs of intermediate difficulty and length in the C++ language, including programs broken into several files; 3. adhere to style and documentation standards in writing programs; 4. use system debuggers to step into and over code, set breakpoints and watch varia ...
Chapter04
... updates can be distributed locally so that patches can be applied to computers that do not have Internet access Patches can be copied to a CD from the local patch server and installed manually if necessary ...
... updates can be distributed locally so that patches can be applied to computers that do not have Internet access Patches can be copied to a CD from the local patch server and installed manually if necessary ...
PowerPoint Presentation - IF-MAP
... – User identity and role vs. IP address – Simpler, easier to manage ...
... – User identity and role vs. IP address – Simpler, easier to manage ...
Cyber Challenges
... • Perceived high cost with low benefit • A highly interactive environment • More powerful computing devices ...
... • Perceived high cost with low benefit • A highly interactive environment • More powerful computing devices ...
Operating Systems Questions
... 1. Write a definition for an operating system; 2. Describe the main features of an operating system for example: the cost, reliability, ease of use, type of interface and how they can be customised. You need to make sure you’re using different operating systems as examples; 3. Explain what an interr ...
... 1. Write a definition for an operating system; 2. Describe the main features of an operating system for example: the cost, reliability, ease of use, type of interface and how they can be customised. You need to make sure you’re using different operating systems as examples; 3. Explain what an interr ...
Position: Senior IA/Security Specialist, (Computer Network Defense
... Job Description: The Senior IA/Security Specialist (CND) will perform System Administration lifecycle management of Computer Network Defense tools needed to sustain a robust cyber security management program and associated network defenses for NAVAIR networks. Responsibilities: • Conduct system admi ...
... Job Description: The Senior IA/Security Specialist (CND) will perform System Administration lifecycle management of Computer Network Defense tools needed to sustain a robust cyber security management program and associated network defenses for NAVAIR networks. Responsibilities: • Conduct system admi ...
Types of Encryption Algorithms
... Stage 5:Virtual Private Networks Security Problems 1. Contamination of internal database via actions of cooperating companies 2. Service delays/denial for intranet traffic due to Internet/ISP problems 3. Compromise or delay of intranet traffic due to crypto mismanagement 4. Compromise of internal t ...
... Stage 5:Virtual Private Networks Security Problems 1. Contamination of internal database via actions of cooperating companies 2. Service delays/denial for intranet traffic due to Internet/ISP problems 3. Compromise or delay of intranet traffic due to crypto mismanagement 4. Compromise of internal t ...
What is the Linux Kernel?
... Provides for the efficient management of system resources: Linux is almost a freeware First developed for 32-bit x86-based PCs (386 or higher). Three major components: Kernel Shell Environment File structure ...
... Provides for the efficient management of system resources: Linux is almost a freeware First developed for 32-bit x86-based PCs (386 or higher). Three major components: Kernel Shell Environment File structure ...
Click to add title - toostusuudised.ee
... A.13: Secure communications and data transfer A.14: Secure acquisition, development, and support of information systems A.15: Security for suppliers and third parties A.16: Incident management A.17: Business continuity/disaster recovery (to the extent that it affects information security) A.18: Comp ...
... A.13: Secure communications and data transfer A.14: Secure acquisition, development, and support of information systems A.15: Security for suppliers and third parties A.16: Incident management A.17: Business continuity/disaster recovery (to the extent that it affects information security) A.18: Comp ...