Slides 2 - USC Upstate: Faculty
... – Convenience: system calls are more difficult to work with than the API » Most programming languages provide a system call interface. The application programmers need to know nothing about how the system call is implemented or what it does during execution. (figure 2.3) ...
... – Convenience: system calls are more difficult to work with than the API » Most programming languages provide a system call interface. The application programmers need to know nothing about how the system call is implemented or what it does during execution. (figure 2.3) ...
BUILDING INTO A MULTILEVEL FILE TRUST
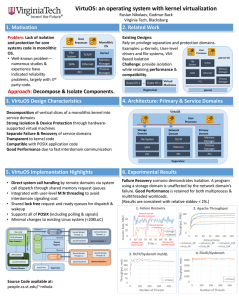
... provide the usual range of capabilities: memory management services, process management, UO device management, and file system services. The purpose of this paper is to examine how one of these services, a multilevel file system, can be designed to utilize the trust that has been achieved in the sec ...
... provide the usual range of capabilities: memory management services, process management, UO device management, and file system services. The purpose of this paper is to examine how one of these services, a multilevel file system, can be designed to utilize the trust that has been achieved in the sec ...
operating system
... The OS maintains additional information about running programs (location in memory, stack pointer, program counter). When a program is run, the operating system converts it into a process. It is the process, rather than the simple program, that the processor executes. ...
... The OS maintains additional information about running programs (location in memory, stack pointer, program counter). When a program is run, the operating system converts it into a process. It is the process, rather than the simple program, that the processor executes. ...
Operating Systems
... Anti-virus: Utility to protect from malicious programs called viruses System Clean-up: Deletes old system files to clear storage space Disk De-frag: Re-arranges files on a hard drive to improve access times ...
... Anti-virus: Utility to protect from malicious programs called viruses System Clean-up: Deletes old system files to clear storage space Disk De-frag: Re-arranges files on a hard drive to improve access times ...
Cindy - Anatomy of a Window
... Memory management deals with temporary storage or use of applications and data The OS controls where applications and data are stored in memory ...
... Memory management deals with temporary storage or use of applications and data The OS controls where applications and data are stored in memory ...
Information System Security
... systems and the information transfers of an organization • intended to counter security attacks • make use of one or more security mechanisms to provide the service • replicate functions normally associated with physical documents • eg have signatures, dates; need protection from disclosure, tamperi ...
... systems and the information transfers of an organization • intended to counter security attacks • make use of one or more security mechanisms to provide the service • replicate functions normally associated with physical documents • eg have signatures, dates; need protection from disclosure, tamperi ...
Operating System
... This course introduces the fundamentals of operating systems. Topics include interprocess communication, process scheduling, deadlock, memory management, virtual memory, and file system. Formal principles are illustrated with examples and case studies of one or more contemporary operating system. ...
... This course introduces the fundamentals of operating systems. Topics include interprocess communication, process scheduling, deadlock, memory management, virtual memory, and file system. Formal principles are illustrated with examples and case studies of one or more contemporary operating system. ...
Operating Systems
... – Developments Leading to Modern Operating Systems – Microsoft Windows Overview – UNIX Systems – Linux ...
... – Developments Leading to Modern Operating Systems – Microsoft Windows Overview – UNIX Systems – Linux ...
Chapter 1 Study Outline
... If systems are properly configured and the file permissions set appropriately, file access controls can restrict legitimate users from accessing files they should not have access to. ...
... If systems are properly configured and the file permissions set appropriately, file access controls can restrict legitimate users from accessing files they should not have access to. ...
BUS 352 Week 4 Discussion 2 (Security components)
... partners, virtual private networks (VPN), and dial-up connections. The types of devices found in the perimeter include VPN clients and VPN servers, remote access servers (RAS) and RAS clients, border routers, firewalls, network intrusion detection systems (NIDS), and proxy servers. To allow partners ...
... partners, virtual private networks (VPN), and dial-up connections. The types of devices found in the perimeter include VPN clients and VPN servers, remote access servers (RAS) and RAS clients, border routers, firewalls, network intrusion detection systems (NIDS), and proxy servers. To allow partners ...
Chapter 13
... Reference Monitor • The part of the security kernel that deals with access control – Mediates access of subjects to objects – Tamper-resistant – Analyzable (small, simple, etc.) ...
... Reference Monitor • The part of the security kernel that deals with access control – Mediates access of subjects to objects – Tamper-resistant – Analyzable (small, simple, etc.) ...
PSWG Closed Door Proposal - Western Electricity Coordinating
... The PSWG has a need for closed sessions as defined in the WECC Board Policy on Closed Sessions for Member Groups (Closed Session Policy). The Closed Session Policy permits closed sessions “to prevent the public disclosure of information identified in Section 7.6.1 of the Bylaws”; including: “to rece ...
... The PSWG has a need for closed sessions as defined in the WECC Board Policy on Closed Sessions for Member Groups (Closed Session Policy). The Closed Session Policy permits closed sessions “to prevent the public disclosure of information identified in Section 7.6.1 of the Bylaws”; including: “to rece ...
Preface
... science. Many people regard the “Communication Theory and Secrecy Systems” paper, by Claude Shannon in 1949, as the foundation of modern cryptology. However, at that time, cryptographic research was mostly restricted to government agencies and the military. That situation gradually changed with the ...
... science. Many people regard the “Communication Theory and Secrecy Systems” paper, by Claude Shannon in 1949, as the foundation of modern cryptology. However, at that time, cryptographic research was mostly restricted to government agencies and the military. That situation gradually changed with the ...
Network and Systems Security
... reduction measures Agree set of Policies and Guidelines that would address specific areas of concern Agree a Network Architecture that would reduce the exposure of Networked systems and provide Inherent containment measures Establish a Computer Incident Response Team to handle incidents in a structu ...
... reduction measures Agree set of Policies and Guidelines that would address specific areas of concern Agree a Network Architecture that would reduce the exposure of Networked systems and provide Inherent containment measures Establish a Computer Incident Response Team to handle incidents in a structu ...
Emsisoft Internet Security
... component to Emsisoft‘s proven dual scanner and realtime protection technology, which means it can protect you from malware and keep you invisible to network intruders. ...
... component to Emsisoft‘s proven dual scanner and realtime protection technology, which means it can protect you from malware and keep you invisible to network intruders. ...
Network Security Overview
... System access is an intruder's ability to gain access to a machine that he is not allowed access to (such as when the intruder does not have an account or password). Entering or accessing systems that you don't have access to usually involves running a hack, script, or tool that exploits a known vul ...
... System access is an intruder's ability to gain access to a machine that he is not allowed access to (such as when the intruder does not have an account or password). Entering or accessing systems that you don't have access to usually involves running a hack, script, or tool that exploits a known vul ...
Assignment C
... the computer’s users who want replace existing, proprietary driven OS to an open-sourced.. SteamOS Debian-based and gaming-focused distribution developed by Valve Corporation and designed around the Steam digital distribution platform. Sunwah Linux A Chinese Linux distribution Symphony OS Includes t ...
... the computer’s users who want replace existing, proprietary driven OS to an open-sourced.. SteamOS Debian-based and gaming-focused distribution developed by Valve Corporation and designed around the Steam digital distribution platform. Sunwah Linux A Chinese Linux distribution Symphony OS Includes t ...
Windows Forensics - University of Washington
... via an unsuspecting or willing person's actions ...
... via an unsuspecting or willing person's actions ...
Tutorail-two-with
... exec call overlays a new process based on a different executable over the calling process. 2.7 What is the purpose of system programs? Answer: System programs can be thought of as bundles of useful system calls. They provide basic functionality to users so that users do not need to write their own p ...
... exec call overlays a new process based on a different executable over the calling process. 2.7 What is the purpose of system programs? Answer: System programs can be thought of as bundles of useful system calls. They provide basic functionality to users so that users do not need to write their own p ...
CL02_Operating_Systems
... time while you are using the system. The / (pronounced “slash”) is the root directory in Linux. Files within the same directory must be given unique ...
... time while you are using the system. The / (pronounced “slash”) is the root directory in Linux. Files within the same directory must be given unique ...
CMP2204 Operating System Technologies
... An operating system defines a software interface of the computer hardware and the architecture with which computer engineers can control and exploit the hardware to provide maximum benefit to the user. It also manages sharing of resources (hardware and software) among the computer’s users (user prog ...
... An operating system defines a software interface of the computer hardware and the architecture with which computer engineers can control and exploit the hardware to provide maximum benefit to the user. It also manages sharing of resources (hardware and software) among the computer’s users (user prog ...