* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download CS5038: The Electronic Society - Homepages | The University of
Multilevel security wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Wireless security wikipedia , lookup
Unix security wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Distributed firewall wikipedia , lookup
Mobile security wikipedia , lookup
Airport security wikipedia , lookup
Security printing wikipedia , lookup
Information security wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Computer security wikipedia , lookup
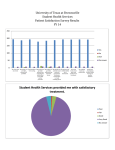
CS5038: The Electronic Society Security 2: Concepts of Security Outline • Types of security: physical, information, hybrid • Concepts of information security – Declarative – Operational • Applicability of concepts to physical and hybrid security. • Management issues. • Security Economics: What’s it worth? • Policy, compliance, and trust Physical Security • Primarily about access control – Ensuring that people are kept within specified zones of buildings, countries, etc.; for example, library access, immigration, clubs • Also about integrity – Ensuring that necessary properties of specified zones are maintained; for example, no sharp objects in the aircraft cabin, no landside liquids airside Information Security • Concerned with • Classically conceived as being about the following three declarative components: – Confidentiality: about secrecy, who’s allowed – Integrity: about soundness, accuracy – Availability: about accessibility (to those allowed) Hybrid Security • Some hybrid attacks: – Steal computer with unencrypted hard-drive – Server room/fire alarm – Engine management system firmware (have been hacked via wireless connections). Declarative and Operational Concepts • Declarative concepts express what we want to achieve: – – – – Confidentiality Integrity Availability Investment • Operational concepts are the mechanisms used to achieve these things: – – – – Access control Authentication Education/training Policies, regulation Investments in (Information) Security • Organizations have limited resources (time, money, etc.) to invest in security • Priorities expressed in terms of the declarative confidentiality, integrity, and availability • Invest in policies, processes, and technologies − i.e., operational entities − to address these priorities Example Types of Organizations, 1: Government Security Agency • Top priority is usually confidentiality – State secrets to protect – Gathered intelligence to protect • High concern for integrity – Important to base actions on uncorrupted information • Limited concern for availability – Often would be prepared to disconnect systems to protect I and A, but not always Example Types of Organizations, 2: Online Retailer • Very high concern for availability – Loss of website or back-end for an hour costs a lot of money – Loss for a week might mean the business fails • Some concern for confidentiality – Credibility may depend on never having has a credit card compromised – Compare Amazon and eBay • Limited concern for integrity – An online retailer might, for example, indicate how many copies of a book are in stock – The actual number doesn’t need to be accurate, just need to give a reliable indication of whether any given order can be fulfilled Example Types of Organizations, 3: Academic Medical Research Organization • Very high concern for integrity – Critical that experiments and conclusions based on accurate data • Some concern for availability – Some experiments will be time-critical • Limited concern for confidentiality – Data all anonymized anyway – May be part of mission to make it widely available Exercise • Think about some more organizations and what their security priorities might be • For example – Banks – Schools, Colleges, and Universities – Environmental charities – Oil & Gas companies • To what extent is the level of financial constraint significant? Applicability of Concepts • In fact, information security concepts are applicable to physical security. • Consider airport security/customs/immigration: – Boarding card check is access control (confidentiality, in effect) – Security scanners are about integrity • Think about other examples Security Management • For large organizations, security is a management as well as a technological problem. Involves various things • Asset management (investment, capital (IT infrastructure)), physical sec., HR • Formulation of policy, choice of controls, operational IT security of network • Risk assessment and risk analysis (inc. threats) • Compliance with regulations (e.g. PCI standards) • Must have a management system for all of the above. – Must comply with standards (e.g. ISO27001) – Deming cycle, Plan-Do-Check-Act Management and Economic Decisions • How to value security and decide what investments to make? • Management accountancy model: – – – – – – – – E.g., return-on-investment (ROI) Do we expect returns to grow linearly with inv.? What are good metrics? High impact, low probability events (long tail) Rapidly changing threat environment Intelligent opponents Need to protect against threats that don’t emerge Pressure to save on balance sheet, right now. Sophisticated Economic Decisions • Use models that account for behaviour of system and environment, and preferences of stakeholders. Find/calculate best choice of control based on preferences over resulting outcomes. • Behaviour: equational models of systems, executable simulations, using probabilities • Preferences: often using a utility function to score how much stakeholder likes choice. Sophisticated Economic Decisions . Various kinds of model. • Micro-economic decisions: model detailed interactions of stakeholder preferences. • Macro-economic model: focus on whole large-scale system via aggregate variables. – E.g., Impulse-response models: how does IT system (and wider business) respond after security shock. Utility Functions • Idea: express, mathematically, how much the manager cares about deviations from targets for C, I, A, and investment, K • Use weights wi − corresponding to the relative importance above − to capture the managers’ preferences: U(C, I, A, K, t) = w1 f1(C – C*) + w2 f2(I – I*) + w3 f3(A – A*) + w4 f4(K – K*) • C = … , I = … , A = … , K = … , all functions of time, t, and of control variables, reflecting configuration under exploration. • Explore equations analytically or experimentally (simulations). Shock and Restore Notes on the Graphs • • The model above comes from Investments and Trade-offs in the Economics of Information Security, David Pym, Christos Ioannidis and Julian Williams, Proc. Financial Cryptography and Data Security 2009, LNCS 5628: 148-162, Springer, 2009. Key points: – Just look at the upper graphs (the lower ones are a technicality) – See how when a shock to confidentiality (i.e., a security breach) hits the system, the characteristics of the system respond – All governed by carefully formulated utility functions of the kind described • • • Targets for all of C, I, and A are 0. When the shock hits, C (blue) is way below target. This causes spend (red) to go way above target, and system availability to go way below target; that is, the system’s operations have to be curtailed and money spent to fix the problem; with these actions taken, all of C, I, and A begin to return to nominal. Notice the difference between the left and right graphs: the left is for the configuration/preferences of a deep-state organization like a government security agency, whereas the right is for something like an online retailer. The graphs show that the agency is much more willing to sacrifice availability than the retailer. Policy, Compliance, and Trust • These things are all inter-related • If an organization has a security policy, how should it be implemented? – Forced compliance? – Employees/students/ … trusted to comply? – What about penalties? • As before, different solutions are appropriate for different environments. • Deep interaction of social and psychological phenomena with technical mechanisms (and management sitting in the middle). Example • Policy: unencrypted laptops may not be taken out of the building • Enforced compliance: search and inspect on exit: – Intrusive, causes resentment – Slow and expensive – Encourages avoidance strategies • Trusted compliance: – Trust employees to comply, but impose very heavy penalty (e.g., fire, prosecute) if found not in compliance USB Sticks Study • Research study part of a project, called ‘Trust Economics’, partly funded by the UK’s Technology Strategy Board. Involved HP Labs, UCL, Aberdeen, Bath, and Newcastle Universities, and Merrill Lynch • City of London investment bank • Policy & implementation for USB stick security • Why is this important? • The bank’s staff all work in several different locations: – The office, inside the firewall – At clients’ offices – At home – In transit • These locations all have different security characteristics: different threats, different levels of protection, different consequences The Problem • USB sticks are used for good, practical reasons: convenient way to move information around the different locations, to work on it, share it, use it for client presentations • But USB sticks expose information to lots of risks: at home, in transit, at the client; for example: – Corruption/theft of data – Loss of stick – Accidental archiving What’s the Solution? • Encryption? It’s the obvious policy solution • How to implement? – Technological enforcement? – Policy enforcement? • What are the barriers? • The major problem, identified by extensive empirical study (structured interviews, etc.) is a social one: – Bankers don’t like being embarrassed in front of clients, , losing face and maybe losing business and they get embarrassed when they forget their passwords • Policies and implementations must take account of these things if they are to be effective • In this case, it was concluded that enforced encryption would be the best option only if the bank’s staff included ‘traitors’ actively trying to leak information • Very often, education and training, backed up with sanctions, works best. Summary • Types of security: physical, information, hybrid • Concepts of information security – Declarative – Operational • Applicability of concepts to physical and hybrid security. • Management issues. • Security Economics: What’s it worth? • Policy, compliance, and trust