* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download chapter13
Wireless security wikipedia , lookup
Information security wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Airport security wikipedia , lookup
Unix security wikipedia , lookup
Cross-site scripting wikipedia , lookup
Cyberattack wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Security-focused operating system wikipedia , lookup
Mobile security wikipedia , lookup
Distributed firewall wikipedia , lookup
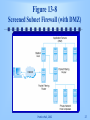
Chapter 13 E-Commerce Security Prentice Hall, 2002 1 Learning Objectives Document the rapid rise in computer and network security attacks Understand the factors contributing to the rise in EC security breaches Explain the basic types of network security attacks Prentice Hall, 2002 2 Learning Objectives (cont.) Discuss the major steps in developing a security risk management system Describe the major types of attacks against EC systems Discuss some of the major technologies for securing EC Prentice Hall, 2002 3 Bringing Down an EC Site: Mere Child’s Play Distributed Denial of Service (DDoS) attacks can inundate a site with so many requests that legitimate traffic is virtually halted Attacker used software to send a flood of data packets to the target computer(s) with the aim of overloading its resources Prentice Hall, 2002 4 Figure 13-1 Using Zombies in a Distributed Denial of Service Attack Source: Scambray et al. (2000) Prentice Hall, 2002 5 Bringing Down an EC Site: Mere Child’s Play (cont.) Distributed Denial of Service (DDoS) attacks Zombie—machine on which the DDoS software is loaded, unknown to the owner Home computers with cable modems or DSL service that are left on all the time Business Web servers located outside the firewall Availability of free tools and scripts make it easy to mount a DDOS attack Prentice Hall, 2002 6 Figure 13-2 Attack Sophistication vs. Intruder Technical Knowledge Source: Special permission to reproduce the CERT ©/CC graphic © 2000 by Carnegie Melon University, in Electronic Commerce 2002 in Allen et al. (2000). Prentice Hall, 2002 7 The Need for Security Data from Computer Security Institute and FBI indicate: Cyber attacks are on the increase Internet connections are increasingly a point of attack The variety of attacks is on the rise The reporting of serious crimes to law enforcement has declined Prentice Hall, 2002 8 Table 13-2 Incidents and Vulnerabilities Reported to CERT Figures from Computer Emergency Response Team (CERT) Prentice Hall, 2002 9 Why Now? Security systems are only as strong as their weakest points Security and ease of use (or implementation) are antithetical to one another Security takes a back seat to market pressures Prentice Hall, 2002 10 Why Now? (cont.) Security of an EC site depends on the security of the Internet as a whole Security vulnerabilities are increasing faster than they can be combated Security compromised by common applications Prentice Hall, 2002 11 Basic Security Issues Issues at a simple marketing site: User’s perspective Company’s perspective Is Web server owned and operated by legitimate company? Web page and form contain some malicious code content? Will Web server distribute the user’s information to another party? Prentice Hall, 2002 Will the user attempt to break into the Web server or alter the site? Will the user try to disrupt the server so it isn’t available to others? 12 Basic Security Issues (cont.) Issues at a simple marketing site: User and company perspective Is network connection free from eavesdropping? Has information sent back and forth between server and browser been altered? Prentice Hall, 2002 13 Basic Security Issues (cont.) Major security issues in EC Authentication Authorization Auditing Confidentiality or privacy Integrity Availability Non-repudiation Prentice Hall, 2002 14 Security Risk Management Required to determine security needs Definitions involved in risk management 4 phases of risk management Assessment Planning Implementation Monitoring Prentice Hall, 2002 Assets—anything of value worth securing Threat—eventuality representing danger to an asset Vulnerability— weakness in a safeguard 15 Security Risk Management (cont.) Assessment phase—evaluation of assets, threats, vulnerabilities Determine organizational objectives Inventory assets Delineate threats Identify vulnerabilities Quantify the value of each risk Prentice Hall, 2002 16 Table 13-3 Security Risks for EC & Other Internet Sites Prentice Hall, 2002 17 Security Risk Management (cont.) Planning phase of risk management— arrive at a set of security policies Define specific policies Establish processes for audit and review Establish an incident response team and contingency plan Prentice Hall, 2002 18 Security Risk Management (cont.) Implementation phase of risk management—choose particular technologies to deal with high priority threats Monitoring phase of risk management— ongoing processes used to determine which measures are successful, unsuccessful and need modification Prentice Hall, 2002 19 Types of Threats and Attacks Nontechnical vs. technical attacks Steps in a hacker’s attack Discover key elements of network Scan for vulnerabilities Hack in and gain administrator privileges Disable auditing & traces from log files Steal files, modify data, steal source code, etc. Install back doors, etc to permit undetectable reentry Return at will to do more damage Prentice Hall, 2002 20 Types of Threats and Attacks (cont.) The players Hackers Crackers Script kiddies Systems and software bugs and misconfigurations Prentice Hall, 2002 21 Types of Threats and Attacks (cont.) Denial-of-service (DoS) attacks IP fragmentation (teardrop, bonk, boink, nestea, and others) DNS spoofing Prentice Hall, 2002 Ping of death Smurf attack SYNFlood Buffer overflows 22 Types of Threats and Attacks (cont.) Input validation attacks Intercepted transmissions Malicious code Viruses Worms Macro viruses and macro worms Trojan horses Malicious mobile code Prentice Hall, 2002 23 Security Technologies Firewalls and access control Firewall—network node that isolates private network from public network Packet-filtering routers Application-level proxies Screened host firewall Prentice Hall, 2002 24 Figure 13-6 Application-Level Proxy (Bastion Gateway Host) Prentice Hall, 2002 25 Figure 13-7 Screened Host Firewall Prentice Hall, 2002 26 Figure 13-8 Screened Subnet Firewall (with DMZ) Prentice Hall, 2002 27 Security Technologies (cont.) Virtual private networks (VPNs)—use public Internet to carry information but remains private Encryption—scramble communications Authentication—ensure information remains untampered with and comes from legitimate source Access control—verify identity of anyone using network Prentice Hall, 2002 28 Security Technologies (cont.) Protocol tunneling—ensure confidentiality and integrity of data transmitted Point-to-point tunneling (PTP) Layer 2 tunneling protocol (L2PT) Intrusion Detection Systems (IDS) Prentice Hall, 2002 29 Managerial Issues Recognize the business consequences of poor security Security through obscurity doesn't work It’s the business that counts, not the technology Security is an on-going, closed-loop process Even for EC sites, internal breaches are more prevalent than external breaches Prentice Hall, 2002 30