NSS Labs 2015 Enterprise Endpoint Testing
... F-Secure Client Security Premium 11.60 build 284 G DATA Security Client v13.1.0.224 Kaspersky Endpoint Security v10.2.2.10535 McAfee Endpoint Protection v8.0 Panda Endpoint Security v7.20.0 Sophos Endpoint Security v10.3 Symantec Endpoint Security v12.1.4112.4156 Trend Micro Endpoint Security v11.0. ...
... F-Secure Client Security Premium 11.60 build 284 G DATA Security Client v13.1.0.224 Kaspersky Endpoint Security v10.2.2.10535 McAfee Endpoint Protection v8.0 Panda Endpoint Security v7.20.0 Sophos Endpoint Security v10.3 Symantec Endpoint Security v12.1.4112.4156 Trend Micro Endpoint Security v11.0. ...
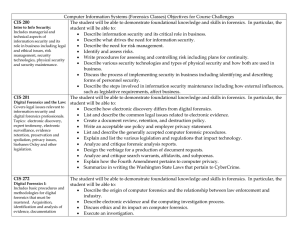
Computer Information Systems (Forensics Classes) Objectives for
... • Describe the function and layout of master boot records, the NTFS Master File Table, and partition tables including how partitions can be hidden and restored. • Identify and describe the Windows registry keys that would be examined relevant to a computer forensics investigation. • Demonstrate the ...
... • Describe the function and layout of master boot records, the NTFS Master File Table, and partition tables including how partitions can be hidden and restored. • Identify and describe the Windows registry keys that would be examined relevant to a computer forensics investigation. • Demonstrate the ...
Capability-Based Optimization in Mediators
... A capability based query optimizer first considers what queries it can ask at the sources that will help answer the query. The bindings may make some more queries at the sources.The process is repeated until We have asked enough queries at the sources to resolve all the conditions of the mediator ...
... A capability based query optimizer first considers what queries it can ask at the sources that will help answer the query. The bindings may make some more queries at the sources.The process is repeated until We have asked enough queries at the sources to resolve all the conditions of the mediator ...
PRINTING PDF FILES CONTAINING EAST ASIAN CHARACTERS
... One peculiarity of some versions of Acrobat and Reader is that the printing menu, by default, is set to enlarge (or shrink) the PDF page size to fit the printer driver's default paper size. This can be quite handy under some circumstances, but like so many instances of letting a computer do the thin ...
... One peculiarity of some versions of Acrobat and Reader is that the printing menu, by default, is set to enlarge (or shrink) the PDF page size to fit the printer driver's default paper size. This can be quite handy under some circumstances, but like so many instances of letting a computer do the thin ...
security - Binus Repository
... • Reduce the potential liability from misuse of corporate information and assets • Eliminate costly and archaic investigation/auditing procedures • Increase information systems’ reliability and availability by conducting investigations while systems are online. ...
... • Reduce the potential liability from misuse of corporate information and assets • Eliminate costly and archaic investigation/auditing procedures • Increase information systems’ reliability and availability by conducting investigations while systems are online. ...
DBT Specific Clinical Training Document
... 3D DIGITAL BREAST TOMOSYNTHESIS TRAINING GUIDELINES MQSA DOES NOT require that the 8-hour DBT training be in the form of CE credits. The technologist must have 8 hours of initial new-modality training in DBT, either including or supplemented by training in the unique features of the specific manufac ...
... 3D DIGITAL BREAST TOMOSYNTHESIS TRAINING GUIDELINES MQSA DOES NOT require that the 8-hour DBT training be in the form of CE credits. The technologist must have 8 hours of initial new-modality training in DBT, either including or supplemented by training in the unique features of the specific manufac ...
information Security Blueprint
... • Using the two documents, security team can develop sound strategy the design of good security architecture ...
... • Using the two documents, security team can develop sound strategy the design of good security architecture ...
Matlab Exercises
... Paste your picture into a word file. Do this by clicking on 'Edit' on the menu bar and then choosing 'Copy.' Now return to the word document and click on 'Edit' and then choose 'Paste.' This will paste the picture into the document. Hints: 1. You may find it helpful to cut text from this document an ...
... Paste your picture into a word file. Do this by clicking on 'Edit' on the menu bar and then choosing 'Copy.' Now return to the word document and click on 'Edit' and then choose 'Paste.' This will paste the picture into the document. Hints: 1. You may find it helpful to cut text from this document an ...
Information security in a youth organisation?
... coordinate all technical and organisational approaches to security of an organisation ...
... coordinate all technical and organisational approaches to security of an organisation ...
ATC-2015 Software Protection and Current Developments in Cyber
... q Top Security Officers are getting hired by the top manufacturers. q Be prepared to see «Security Usta» in your local garage J “This document contains confidential and/or proprietary information of MilSOFT and may not be reproduced, copied, disclosed to other parties or used in anyway in whole ...
... q Top Security Officers are getting hired by the top manufacturers. q Be prepared to see «Security Usta» in your local garage J “This document contains confidential and/or proprietary information of MilSOFT and may not be reproduced, copied, disclosed to other parties or used in anyway in whole ...
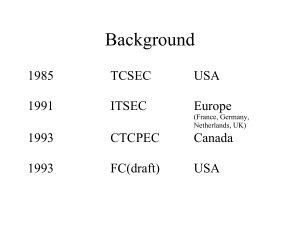
Common Criteria
... components (e.g. an EAL), combined together to satisfy a set of identified security objectives. Evaluation Assurance Level (EAL) — A package consisting of assurance components from Part 3 that represents a point on the CC predefined assurance scale. ...
... components (e.g. an EAL), combined together to satisfy a set of identified security objectives. Evaluation Assurance Level (EAL) — A package consisting of assurance components from Part 3 that represents a point on the CC predefined assurance scale. ...
Manual Instruction of Mug heat transfer machine
... 5. When the temperature reached the specified degree, the machine will reach to stable temperature stage automatically. 6. Take out the finalize mug, put the mug with the picture in the heat mat. Put down the pressure handle. Note: pressure couldn’t be too much or else the mug will be broken! 7. Tur ...
... 5. When the temperature reached the specified degree, the machine will reach to stable temperature stage automatically. 6. Take out the finalize mug, put the mug with the picture in the heat mat. Put down the pressure handle. Note: pressure couldn’t be too much or else the mug will be broken! 7. Tur ...
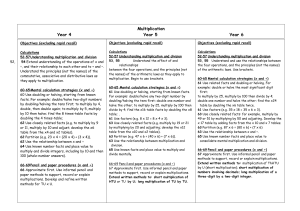
Geometry and Measures
... Multiples , Factors and prime factors Multiply and Divide using known facts Number Patterns Square number and square roots Multiply numbers up to 4 digits by 1 or 2 digit numbers using grid or formal written method. Problem Solving using multiplication. Properties of a square and rectangle - diagona ...
... Multiples , Factors and prime factors Multiply and Divide using known facts Number Patterns Square number and square roots Multiply numbers up to 4 digits by 1 or 2 digit numbers using grid or formal written method. Problem Solving using multiplication. Properties of a square and rectangle - diagona ...
Voice Over IP and Security
... Security Issues (cont) IPsec AH is incompatible with NAT : address behind NAT are masked -> Encapsulating IPsec packet in a new UDP packet. Use SRTP: offers encryption, authentication and periodic refreshment of session keys. Implement strict ACL at gateways. Implement NAT behind firewalls: issues ...
... Security Issues (cont) IPsec AH is incompatible with NAT : address behind NAT are masked -> Encapsulating IPsec packet in a new UDP packet. Use SRTP: offers encryption, authentication and periodic refreshment of session keys. Implement strict ACL at gateways. Implement NAT behind firewalls: issues ...
C4 January 2009
... Information for Candidates A booklet ‘Mathematical Formulae and Statistical Tables’ is provided. Full marks may be obtained for answers to ALL questions. The marks for the parts of questions are shown in round brackets, e.g. (2). There are 7 questions in this question paper. The total mark for this ...
... Information for Candidates A booklet ‘Mathematical Formulae and Statistical Tables’ is provided. Full marks may be obtained for answers to ALL questions. The marks for the parts of questions are shown in round brackets, e.g. (2). There are 7 questions in this question paper. The total mark for this ...
FEARLESS - Cyber Security Research and Education Institute
... Secure Social Networks, Data Mining for Security, Big Data Analytics, Critical Infrastructure Protection, Biometrics, Security Engineering ...
... Secure Social Networks, Data Mining for Security, Big Data Analytics, Critical Infrastructure Protection, Biometrics, Security Engineering ...