William Stallings, Cryptography and Network Security 5/e
... breaches in your company = L Estimated Money loss per year due to uncontrolled system administrator/programmers paranoidism = D ...
... breaches in your company = L Estimated Money loss per year due to uncontrolled system administrator/programmers paranoidism = D ...
Maslow Theory * Bhaw and Binta
... different stages include; Self- actualization, esteem, love and belonging, safety and lastly physiological. Maslow does not only apply to any business but also can apply to your day to day routine, your life with your friends and also in an organization such as your school. Self-actualization: Self- ...
... different stages include; Self- actualization, esteem, love and belonging, safety and lastly physiological. Maslow does not only apply to any business but also can apply to your day to day routine, your life with your friends and also in an organization such as your school. Self-actualization: Self- ...
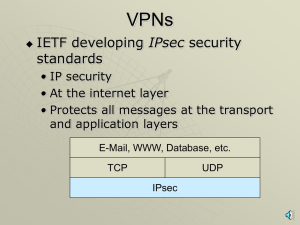
VPNs, PKIs, ISSs, SSLs with narration
... SSL ISS Process • Two sides negotiate security parameters • Webserver authenticates itself • Browser may authenticate itself but rarely does • Browser selects a symmetric session key, sends to webserver • Adds a digital signature and encrypts all messages with the symmetric key ...
... SSL ISS Process • Two sides negotiate security parameters • Webserver authenticates itself • Browser may authenticate itself but rarely does • Browser selects a symmetric session key, sends to webserver • Adds a digital signature and encrypts all messages with the symmetric key ...
Introduction to IT Security - Virginia Alliance for Secure Computing
... Working Definitions of Security IT Security Principles Three Aspects of Security Types of Security Services Types of Security Threats Goals of Security Types of Security Attacks Model for Network Security Model for Network Access Security ...
... Working Definitions of Security IT Security Principles Three Aspects of Security Types of Security Services Types of Security Threats Goals of Security Types of Security Attacks Model for Network Security Model for Network Access Security ...
Operating System Security Chapter 9 Operating System Security
... • Software bugs are a common security threat – Caused by sloppy programming – Provide opportunities to attackers by leaving system in an unexpected state, sometimes with high privilege levels – Best defense is to have well trained programmers and follow establish software development methods ...
... • Software bugs are a common security threat – Caused by sloppy programming – Provide opportunities to attackers by leaving system in an unexpected state, sometimes with high privilege levels – Best defense is to have well trained programmers and follow establish software development methods ...
A Fine Display of Innovation
... guarantee that the person who holds them is more of a genius than the person who doesn't. Bill Gates, for example, didn't stick around Harvard long enough to pick up his degree, but his status as a university dropout didn't hold him back. Another fine example of ingenuity has just been displayed by ...
... guarantee that the person who holds them is more of a genius than the person who doesn't. Bill Gates, for example, didn't stick around Harvard long enough to pick up his degree, but his status as a university dropout didn't hold him back. Another fine example of ingenuity has just been displayed by ...
Are Clouds Secure?
... are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor ...
... are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor ...
Interactive comment on “A step-by
... precludes, a priori, any possible exchange with the bottom. Certainly benthic exchange should be included until that point, later in the paper, where that component is argued to be small. Other systems may have a large benthic contribution. (2) I am not one of those who believes that its is both cor ...
... precludes, a priori, any possible exchange with the bottom. Certainly benthic exchange should be included until that point, later in the paper, where that component is argued to be small. Other systems may have a large benthic contribution. (2) I am not one of those who believes that its is both cor ...
Introduction - Computer Science
... – Traditionally provided by physical and administrative mechanisms – Many daily activities have been shifted from physical world to cyber space • Use of computers ...
... – Traditionally provided by physical and administrative mechanisms – Many daily activities have been shifted from physical world to cyber space • Use of computers ...
Information System Security
... systems and the information transfers of an organization • intended to counter security attacks • make use of one or more security mechanisms to provide the service • replicate functions normally associated with physical documents • eg have signatures, dates; need protection from disclosure, tamperi ...
... systems and the information transfers of an organization • intended to counter security attacks • make use of one or more security mechanisms to provide the service • replicate functions normally associated with physical documents • eg have signatures, dates; need protection from disclosure, tamperi ...
FOI Memo 5492 Nr 3
... The Robert S. Strauss Center for International Security and Law, CCAPS (Climate Change and African Political Stability), University of Texas at Austin As its website says so succinctly, “CCAPS is funded by the U.S. Department of Defense’s Minerva Initiative, a universitybased, social science researc ...
... The Robert S. Strauss Center for International Security and Law, CCAPS (Climate Change and African Political Stability), University of Texas at Austin As its website says so succinctly, “CCAPS is funded by the U.S. Department of Defense’s Minerva Initiative, a universitybased, social science researc ...
Protection
... and complex systems Networks, cloud computing, big data and other high-tech application and development are facing complex network environment ...
... and complex systems Networks, cloud computing, big data and other high-tech application and development are facing complex network environment ...
Rimini Street Technology Solution Brief-Oracle Security-LT
... But vendor-supplied security updates typically address very narrow and specific potential vulnerabilities that are only in the vendor’s portion of your technology stack. These vulnerabilities may indeed address a potential issue — but they do not, and cannot, guarantee the overall security of your ER ...
... But vendor-supplied security updates typically address very narrow and specific potential vulnerabilities that are only in the vendor’s portion of your technology stack. These vulnerabilities may indeed address a potential issue — but they do not, and cannot, guarantee the overall security of your ER ...
Lindsey used all the paper in her box and had 50
... a. Give examples of linear equations in one variable with one solution, infinitely many solutions, or no solutions. Show which of these possibilities is the case by successively transforming the given equation into simpler forms, until an equivalent equation of the form x = a, a = a, or a = b result ...
... a. Give examples of linear equations in one variable with one solution, infinitely many solutions, or no solutions. Show which of these possibilities is the case by successively transforming the given equation into simpler forms, until an equivalent equation of the form x = a, a = a, or a = b result ...
Self-Adaptive Niching Differential Evolution and Its Application
... NCjDE is free from control parameter adjustment. This paper also focuses on the problem of semi-fragile watermarking for two-dimensional (2D) color barcodes in which the appropriate barcode colors and watermark are unknown. Over the last two or three years, paperless verification through the use of 2 ...
... NCjDE is free from control parameter adjustment. This paper also focuses on the problem of semi-fragile watermarking for two-dimensional (2D) color barcodes in which the appropriate barcode colors and watermark are unknown. Over the last two or three years, paperless verification through the use of 2 ...
Sentence 1
... gave us courage and hope and patience, because what we decided was that we had two wars to win. And once we finished the war against the Fascists and then we'll fight against racism. Now what that did was that unified us! That brought us together with a common goal, so we became more focused on how ...
... gave us courage and hope and patience, because what we decided was that we had two wars to win. And once we finished the war against the Fascists and then we'll fight against racism. Now what that did was that unified us! That brought us together with a common goal, so we became more focused on how ...
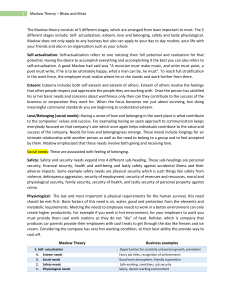
Harvard SEAS Information Security Office Services Overview
... resources notifies user or resource owner and triggers incident response service Inspects network traffic to identify security vulnerabilities in networkconnected systems or devices. monitors, detects and, as necessary, protects High Risk Confidential Information detects and reports on computers tha ...
... resources notifies user or resource owner and triggers incident response service Inspects network traffic to identify security vulnerabilities in networkconnected systems or devices. monitors, detects and, as necessary, protects High Risk Confidential Information detects and reports on computers tha ...
Robust. Reliable. Factory Line. Industrial Security redefined protecting industrial networks
... (QoS) functionalities and helps with intrusion detection and antivirus protection. The mGuard portfolio is complemented by a highly scalable device management software. Innominate products are marketed worldwide under the mGuard brand through system integrators and OEM partners. Further information ...
... (QoS) functionalities and helps with intrusion detection and antivirus protection. The mGuard portfolio is complemented by a highly scalable device management software. Innominate products are marketed worldwide under the mGuard brand through system integrators and OEM partners. Further information ...
Abstracts
... The Dynamics of Liquid Movement Inside the Nozzle During the Bubble Departures for Low Air Volume Flow Rate The main aim of investigation was to analyze the influence of liquid movement inside the nozzle on the dynamics of bubble departure. Dynamics of such process decides about the periodic and ape ...
... The Dynamics of Liquid Movement Inside the Nozzle During the Bubble Departures for Low Air Volume Flow Rate The main aim of investigation was to analyze the influence of liquid movement inside the nozzle on the dynamics of bubble departure. Dynamics of such process decides about the periodic and ape ...
Case Study - Multiscope Document Solutions
... across the firm’s multiple locations without increasing user and support costs. The solution’s extension capabilities allowed the Finkelstein team to create multiple case integration points, custom functionality, custom views and a unique folder structure that weren’t available prior to the installa ...
... across the firm’s multiple locations without increasing user and support costs. The solution’s extension capabilities allowed the Finkelstein team to create multiple case integration points, custom functionality, custom views and a unique folder structure that weren’t available prior to the installa ...
ME Magnetic Moment Etalons 2176 - MAGNET
... The stated dipole moments are approximate values. The exact values for each Magnetic Moment Etalon are determined by calibration. A proprietary calibration certificate, which documents traceability of calibration to national standards, is issued free of charge on purchase. A calibration can alternat ...
... The stated dipole moments are approximate values. The exact values for each Magnetic Moment Etalon are determined by calibration. A proprietary calibration certificate, which documents traceability of calibration to national standards, is issued free of charge on purchase. A calibration can alternat ...
Report on `Embryonic Hopes: Societal and legal dimensions of
... The ‘Embryonic Hopes’ workshop, which was held at King’s College London on 6th June, brought together a number of persons from the wider academic community to discuss the promises and expectations of reproductive medicine and new genetics in the UK and Israel. With the Human Fertilisation and Embryo ...
... The ‘Embryonic Hopes’ workshop, which was held at King’s College London on 6th June, brought together a number of persons from the wider academic community to discuss the promises and expectations of reproductive medicine and new genetics in the UK and Israel. With the Human Fertilisation and Embryo ...