Document
... 8.3 and higher allows for OLE automation of Transformer Model Read SQL database and create User Views for each class ...
... 8.3 and higher allows for OLE automation of Transformer Model Read SQL database and create User Views for each class ...
Sample Paper Round 1
... 18. Which of the following operations cannot be performed on a lathe a. ...
... 18. Which of the following operations cannot be performed on a lathe a. ...
POWERSHRED® 125Ci/125i
... defects in material and workmanship and provides service and support for 2 years from the date of purchase by the original consumer. Fellowes warrants the cutting blades of the machine to be free from defects in material and workmanship for the lifetime of the shredder.If any part is found to be def ...
... defects in material and workmanship and provides service and support for 2 years from the date of purchase by the original consumer. Fellowes warrants the cutting blades of the machine to be free from defects in material and workmanship for the lifetime of the shredder.If any part is found to be def ...
Importance of SETA programs
... Designed to modify any employee behavior that endangers the security of sensitive information ...
... Designed to modify any employee behavior that endangers the security of sensitive information ...
426_Fall10_lect01 - Purdue Computer Science
... • Defense is almost always harder than attack. • In which ways information security is more difficult than physical security? ...
... • Defense is almost always harder than attack. • In which ways information security is more difficult than physical security? ...
Information Security Incident Management
... •Information Security Policies: - It is a management statement that information security is important - It provide direction by establishing a set of clearlyarticulated business rules to help people make decision when using or managing information assets - It is uniquely tailored to your organizatio ...
... •Information Security Policies: - It is a management statement that information security is important - It provide direction by establishing a set of clearlyarticulated business rules to help people make decision when using or managing information assets - It is uniquely tailored to your organizatio ...
View degree planner as PDF
... The BSc/LLB requires 34 papers to complete. This template is intended as a model only. The order in which papers are taken can be adapted to suit students’ individual requirements. All 100, 200 and 300 Level compulsory law papers are worth 20 points. Students who wish to enroll in both LAWS305 and L ...
... The BSc/LLB requires 34 papers to complete. This template is intended as a model only. The order in which papers are taken can be adapted to suit students’ individual requirements. All 100, 200 and 300 Level compulsory law papers are worth 20 points. Students who wish to enroll in both LAWS305 and L ...
Distributed System Concepts and Architectures
... Kernel authenticates the client and then invokes the object server Implemented via Interprocess Communication at transport layer Supported by secure host-to-host communications at the network layer and node to node communication at the link layer Secure distributed system consists of communicating s ...
... Kernel authenticates the client and then invokes the object server Implemented via Interprocess Communication at transport layer Supported by secure host-to-host communications at the network layer and node to node communication at the link layer Secure distributed system consists of communicating s ...
Next State FAQ`s - Next State Print
... Large areas of dark colours appear very differently on screen than when they are printed onto a white background textile so they will not always provide the result that you see on a screen. Breaking up large solid areas of dark print will provide more impact and contrast in the print. Because digita ...
... Large areas of dark colours appear very differently on screen than when they are printed onto a white background textile so they will not always provide the result that you see on a screen. Breaking up large solid areas of dark print will provide more impact and contrast in the print. Because digita ...
01 Computer security overview
... Curious or dishonest individuals — for personal gain Friends and family Hackers, crackers, script kiddies — for challenge and reputation Companies — for business intelligence and marketing Organized criminals — for money Governments and security agencies — NSA, SVR, GCHQ, DGSE, etc. Military SIGINT ...
... Curious or dishonest individuals — for personal gain Friends and family Hackers, crackers, script kiddies — for challenge and reputation Companies — for business intelligence and marketing Organized criminals — for money Governments and security agencies — NSA, SVR, GCHQ, DGSE, etc. Military SIGINT ...
Finding Petroleum - Oracle
... This document is for informational purposes. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon solely in making purchasing decisions. The development, release, and timing of any features or functionality described in this document remains at the so ...
... This document is for informational purposes. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon solely in making purchasing decisions. The development, release, and timing of any features or functionality described in this document remains at the so ...
Orange Book Summary - UMBC Center for Information Security and
... Full auditing of security events (i.e. date/time, event, user, success/failure, terminal ID) Protected system mode of operation. Added protection for authorisation and audit data. Documentation as C1 plus information on examining audit information. This is one of the most common certifications. Exam ...
... Full auditing of security events (i.e. date/time, event, user, success/failure, terminal ID) Protected system mode of operation. Added protection for authorisation and audit data. Documentation as C1 plus information on examining audit information. This is one of the most common certifications. Exam ...
Orange
... Full auditing of security events (i.e. date/time, event, user, success/failure, terminal ID) ...
... Full auditing of security events (i.e. date/time, event, user, success/failure, terminal ID) ...
Computer security - University of London International Programmes
... This course deals with the more technical means of making a computing system secure. This process starts with defining the proper security requirements, which are usually stated as a security policy. Security models formalise those policies and may serve as a reference to check the correctness of an ...
... This course deals with the more technical means of making a computing system secure. This process starts with defining the proper security requirements, which are usually stated as a security policy. Security models formalise those policies and may serve as a reference to check the correctness of an ...
Paper Reference(s) - Life Learning Cloud
... Full marks may be obtained for answers to ALL questions. The marks for the parts of questions are shown in round brackets, e.g. (2). There are 10 questions in this question paper. The total mark for this paper is 75. There are 36 pages in this question paper. Any blank pages are indicated. ...
... Full marks may be obtained for answers to ALL questions. The marks for the parts of questions are shown in round brackets, e.g. (2). There are 10 questions in this question paper. The total mark for this paper is 75. There are 36 pages in this question paper. Any blank pages are indicated. ...
POWERSHRED® 63Cb - Fellowes Canada Ltd.
... Limited Warranty: Fellowes, Inc. (“Fellowes”) warrants the parts of the machine to be free of defects in material and workmanship and provides service and support for 1 year from the date of purchase by the original consumer. Fellowes warrants the cutting blades of the machine to be free from defect ...
... Limited Warranty: Fellowes, Inc. (“Fellowes”) warrants the parts of the machine to be free of defects in material and workmanship and provides service and support for 1 year from the date of purchase by the original consumer. Fellowes warrants the cutting blades of the machine to be free from defect ...
Paper Reference(s)
... Full marks may be obtained for answers to ALL questions. The marks for individual questions and the parts of questions are shown in round brackets: e.g. (2). There are 9 questions on this paper. The total mark for this paper is 75. Advice to Candidates You must ensure that your answers to parts of q ...
... Full marks may be obtained for answers to ALL questions. The marks for individual questions and the parts of questions are shown in round brackets: e.g. (2). There are 9 questions on this paper. The total mark for this paper is 75. Advice to Candidates You must ensure that your answers to parts of q ...
Cooperative Power
... WH Competencies: Must be able to achieve Quality Results, be Change Oriented, use effective Communication skills, be Customer Driven, foster Innovation, be a Continuous Learner, and display Teamwork behaviors. Accountability: Accountable to the Security Installation Coordinator. Shall secure approva ...
... WH Competencies: Must be able to achieve Quality Results, be Change Oriented, use effective Communication skills, be Customer Driven, foster Innovation, be a Continuous Learner, and display Teamwork behaviors. Accountability: Accountable to the Security Installation Coordinator. Shall secure approva ...
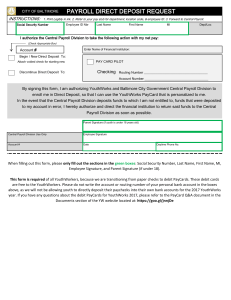
payroll direct deposit request
... When filling out this form, please only fill out the sections in the green boxes: Social Security Number, Last Name, First Name, MI, Employee Signature, and Parent Signature (if under 18). This form is required of all YouthWorkers, because we are transitioning from paper checks to debit PayCards. Th ...
... When filling out this form, please only fill out the sections in the green boxes: Social Security Number, Last Name, First Name, MI, Employee Signature, and Parent Signature (if under 18). This form is required of all YouthWorkers, because we are transitioning from paper checks to debit PayCards. Th ...
Results - SIITME
... We calculated the similarity of the documents to a query test (variable), by applying the Jaccard coefficient and the Euclidean distance. In the case of the Jaccard coefficient (dJ), the similarity is maximum for dJ=1, whereas for the Euclidean distance (dE) the similarity is maximum when the distan ...
... We calculated the similarity of the documents to a query test (variable), by applying the Jaccard coefficient and the Euclidean distance. In the case of the Jaccard coefficient (dJ), the similarity is maximum for dJ=1, whereas for the Euclidean distance (dE) the similarity is maximum when the distan ...
Visualization
... Correlation uses software technology to analyze aggregated data, in real-time, to determine if specific patterns exist. These patterns of similar security events often correspond to specific securityattacks – whether denial of service,anti virus, or some other form of attack. Visualization, the fina ...
... Correlation uses software technology to analyze aggregated data, in real-time, to determine if specific patterns exist. These patterns of similar security events often correspond to specific securityattacks – whether denial of service,anti virus, or some other form of attack. Visualization, the fina ...
ppt
... • Goal – limit attacker’s possibilities by creating layers of hindrance (e.g. access) • Administrative controls should be part of security policy ...
... • Goal – limit attacker’s possibilities by creating layers of hindrance (e.g. access) • Administrative controls should be part of security policy ...