The plotting of observations on probability paper
... where y’ = F(x) belonging value of the y equals (x-µ)/σ. The geometrical position of the points (x, y’) with y’ = F(x) becomes on the original linear y-scale the geometrical position of the points (x, (x-µ)/σ), being a straight line. In this, µ is the x co-ordinate (abscissa) of the point with co-or ...
... where y’ = F(x) belonging value of the y equals (x-µ)/σ. The geometrical position of the points (x, y’) with y’ = F(x) becomes on the original linear y-scale the geometrical position of the points (x, (x-µ)/σ), being a straight line. In this, µ is the x co-ordinate (abscissa) of the point with co-or ...
HUNTING-AS-A-SERVICE By Accenture, Powered by Endgame
... of a breach before security analysts take action. This approach is failing. The most dangerous hackers are — with minimal cost and effort — compromising victims at will by leveraging new techniques as their weapons of choice. These approaches include single-use rotating attack patterns that don’t le ...
... of a breach before security analysts take action. This approach is failing. The most dangerous hackers are — with minimal cost and effort — compromising victims at will by leveraging new techniques as their weapons of choice. These approaches include single-use rotating attack patterns that don’t le ...
A Cotangent Laplacian for Images as Surfaces
... locations and color values define energies whose minima intuitively propagate tone map adjustments [Lischinski et al. 2006] or sparse color values [Levin et al. 2004]. Other techniques have overlain triangle meshes atop images to reduce computation complexity (e.g. for image warping [Karni et al. 20 ...
... locations and color values define energies whose minima intuitively propagate tone map adjustments [Lischinski et al. 2006] or sparse color values [Levin et al. 2004]. Other techniques have overlain triangle meshes atop images to reduce computation complexity (e.g. for image warping [Karni et al. 20 ...
Chapter 5.1: Serology Techniques
... Not species-specific ▪ Reacts with semen from any animal ▪ Not usually a big problem in forensic casework ▪ Animal sperm are morphologically distinct from primate sperm under the microscope ...
... Not species-specific ▪ Reacts with semen from any animal ▪ Not usually a big problem in forensic casework ▪ Animal sperm are morphologically distinct from primate sperm under the microscope ...
Reading Room Policies Patron Information Form
... 2. Patrons must present identification in the form of a UA student/employee ID, valid driver’s license, or public library card upon entering the archives. 3. Food and drink (including water) are not permitted in the reading room. 4. Personal belongings including coats, briefcases, book bags, laptop ...
... 2. Patrons must present identification in the form of a UA student/employee ID, valid driver’s license, or public library card upon entering the archives. 3. Food and drink (including water) are not permitted in the reading room. 4. Personal belongings including coats, briefcases, book bags, laptop ...
Security - Computer Science Department
... – How do you know when you are being attacked? – How quickly can you stop the attack? – Attribution: can you identify the attacker(s)? – Can you prevent the attack from recurring? ...
... – How do you know when you are being attacked? – How quickly can you stop the attack? – Attribution: can you identify the attacker(s)? – Can you prevent the attack from recurring? ...
The Dark Ages
... 2. Does this founding of universities and construction of Notre Dame conflict with or match the textbook accounts of the Middle Ages? Explain. ...
... 2. Does this founding of universities and construction of Notre Dame conflict with or match the textbook accounts of the Middle Ages? Explain. ...
petition for the acceptance of a secondary school degree for
... years) and academic content (courses taken, results achieved) of the studies pertaining to the degree certificate submitted for acceptance. original or notarized official copy of the paper proving (and showing the result) that the student had taken an (examination) – if such exists – in his/her ho ...
... years) and academic content (courses taken, results achieved) of the studies pertaining to the degree certificate submitted for acceptance. original or notarized official copy of the paper proving (and showing the result) that the student had taken an (examination) – if such exists – in his/her ho ...
Threat Briefing - (AFCEA) Ottawa Chapter
... application of this security architecture methodology. IT Security Technical Safeguards This session will provide an overview of technical safeguards and, more specifically, the security functions that might be implemented in hardware or software to protect IT systems. IP Convergence Security; SCADA ...
... application of this security architecture methodology. IT Security Technical Safeguards This session will provide an overview of technical safeguards and, more specifically, the security functions that might be implemented in hardware or software to protect IT systems. IP Convergence Security; SCADA ...
JUnit - GETI
... version 2.0, DbUnit can works with very large dataset when use in streaming mode. DbUnit can also helps you to verify that your database data match expected set of values. ...
... version 2.0, DbUnit can works with very large dataset when use in streaming mode. DbUnit can also helps you to verify that your database data match expected set of values. ...
Network security policy: best practices
... system or data that if compromised would cause a moderate disruption in the business or minor legal or financial ramification, provide further access to other system The targeted system or data requires a moderate effort to restore The restoration process is disruptive to the system ...
... system or data that if compromised would cause a moderate disruption in the business or minor legal or financial ramification, provide further access to other system The targeted system or data requires a moderate effort to restore The restoration process is disruptive to the system ...
Forensic Biology by Richard Li
... Not species-specific ▪ Reacts with semen from any animal ▪ Not usually a big problem in forensic casework ▪ Animal sperm are morphologically distinct from primate sperm under the microscope ...
... Not species-specific ▪ Reacts with semen from any animal ▪ Not usually a big problem in forensic casework ▪ Animal sperm are morphologically distinct from primate sperm under the microscope ...
CS 446 Computer Integrated Surgery II Critical Review Group 8 Woo
... While the paper discusses the use of a master-slave surgical system for vitreoretinal surgery, it briefly discusses the advantages and disadvantages of other types of surgical systems, including the cooperative control robot that we are using for our experiments. In addition, many feature ideas for ...
... While the paper discusses the use of a master-slave surgical system for vitreoretinal surgery, it briefly discusses the advantages and disadvantages of other types of surgical systems, including the cooperative control robot that we are using for our experiments. In addition, many feature ideas for ...
CHAPTER I INTRODUCTION A. Background of the Study
... expected to be able to communicate well with foreigners. Yet, I found it hard to deal with Korean customers as I could not understand what they said. When Korean customers talk to me to order some drink, I had to ask them to repeat several times. The ordering time took longer than it should and I wa ...
... expected to be able to communicate well with foreigners. Yet, I found it hard to deal with Korean customers as I could not understand what they said. When Korean customers talk to me to order some drink, I had to ask them to repeat several times. The ordering time took longer than it should and I wa ...
word-template-empty.dot - Journal of Machine Learning Research
... 201 S. Craig Street, 2 West Pittsburgh, PA 15213, USA Editor: Leslie Lamport Abstract This document, which is based on an earlier document by Minton et al., (1999), describes the required formatting of JMLR papers, including margins, fonts, citation styles, and figure placement. It describes how aut ...
... 201 S. Craig Street, 2 West Pittsburgh, PA 15213, USA Editor: Leslie Lamport Abstract This document, which is based on an earlier document by Minton et al., (1999), describes the required formatting of JMLR papers, including margins, fonts, citation styles, and figure placement. It describes how aut ...
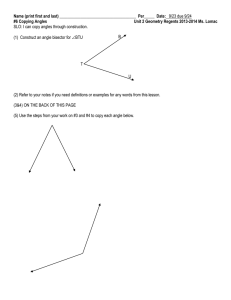
2.6 Copying Angles 092313 (doc)
... Name (print first and last) _____________________________________ Per_____ Date: 9/23 due 9/24 #6 Copying Angles HW Unit 2 Geometry Regents 2013-2014 Ms. Lomac (1) Copy the three angles below with a compass and straightedge. Then go back and bisect the original angle. ...
... Name (print first and last) _____________________________________ Per_____ Date: 9/23 due 9/24 #6 Copying Angles HW Unit 2 Geometry Regents 2013-2014 Ms. Lomac (1) Copy the three angles below with a compass and straightedge. Then go back and bisect the original angle. ...
Enhancing the Security and Capacity of Collaborative Software for
... groupware for first responder”. The idea is to design a framework for enhancing the security, effectness, and capacity of the collaborative software tools for first responders and large task forces. An application of such framework will be enhancing some existing instant messenger and decision suppo ...
... groupware for first responder”. The idea is to design a framework for enhancing the security, effectness, and capacity of the collaborative software tools for first responders and large task forces. An application of such framework will be enhancing some existing instant messenger and decision suppo ...
powershred® p-35c - Fellowes Canada Ltd.
... Warning: Changes or modifications to this unit not expressly approved by the party responsible for compliance could void the user's authority to operate the equipment. NOTE: This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FC ...
... Warning: Changes or modifications to this unit not expressly approved by the party responsible for compliance could void the user's authority to operate the equipment. NOTE: This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FC ...
This paper consists of two parts both of which attempt to provide
... computed by a polynomial sized circuit family. In the earlier Krajı́ček paper, τ (g)b (x) tautologies, where g computes a certain pseudo-random number generator, were put forward as candidate hard tautologies for propositional proof systems like extended Frege. Another choice of g suggested in this ...
... computed by a polynomial sized circuit family. In the earlier Krajı́ček paper, τ (g)b (x) tautologies, where g computes a certain pseudo-random number generator, were put forward as candidate hard tautologies for propositional proof systems like extended Frege. Another choice of g suggested in this ...
Advanced Linux Security
... • Malicious code, that manages to bypass the application level security, will usually be executed with the same permissions the current user has • Malicious or careless users might also leak sensitive data unless the rules for handling such data are not enforced by the system ...
... • Malicious code, that manages to bypass the application level security, will usually be executed with the same permissions the current user has • Malicious or careless users might also leak sensitive data unless the rules for handling such data are not enforced by the system ...
Handbook for Magnaflux Y6 Electromagnetic Yoke - Nov 11
... strong attractive carrying case. A light source, attached to one leg of the Y6 Yoke, is activated by the magnetic field and switches on automatically during testing. Ideal for darker corners. Light source for Y6 Yoke – part number ...
... strong attractive carrying case. A light source, attached to one leg of the Y6 Yoke, is activated by the magnetic field and switches on automatically during testing. Ideal for darker corners. Light source for Y6 Yoke – part number ...