* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Introduction
Multilevel security wikipedia , lookup
Distributed firewall wikipedia , lookup
Cyberwarfare wikipedia , lookup
Wireless security wikipedia , lookup
Information security wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Mobile security wikipedia , lookup
Security printing wikipedia , lookup
Airport security wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Social engineering (security) wikipedia , lookup
Security-focused operating system wikipedia , lookup
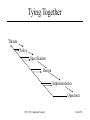
CSC 382: Computer Security Introduction CSC 382: Computer Security Slide #1 About Me http://www.eecs.utoledo.edu/~jwalden James Walden – Assistant Professor of Computer Science – [email protected] – Interests: • • • • Software Security Programming Languages Software Engineering Network Security CSC 382: Computer Security Slide #2 Course Administration http://www.eecs.utoledo.edu/~jwalden/2005/spring/eecs4980 • Web Site – Notes, readings, and assignments on web site. • Discussion Board • Assignment submission – Send electronic submissions to [email protected] • Contact Information – Email: – Phone: – Office Hours: CSC 382: Computer Security Slide #3 Course Goals Learn how to answer these questions: • • • • • • • • • What is computer security? How do computer systems fail? How can risks be evaluated? How does a particular security solution mitigate risks? How can costs and tradeoffs of security solutions be balanced? How can secure software be designed, written, and tested? When and how can cryptography be used securely? How viruses and worms propagate and how can we stop them? What are the essential problems and solutions of network security? CSC 382: Computer Security Slide #4 Course Outline 1. 2. 3. 4. 5. 6. 7. 8. Introduction: Components and Importance of Security. Risk Evaluation. Secure Design Principles. Secure Programming. Buffer Overflows. Vulnerability Analysis. Testing Software Security. Access Control. Security Policies. CSC 382: Computer Security 9. Cryptography. 10. Authentication and Identity. 11. TCP/IP Security. 12. UNIX Security. 13. Network Scanning. 14. Network Attacks. 15. Malware and Rootkits. 16. Incident Response and Forensics. 17. Emission and Physical Security. Slide #5 Grading Midterm Exam 30% Final Exam 40% Assignments 30% Exams are take-home comprehensive tests of how you think about information security. – You may use class readings and notes to help on exams. – Test how well you think about security issues. CSC 382: Computer Security Slide #6 Topics A first look at five important questions: – – – – – What is security? What are the threats to our information assets? How do we evaluate risks of various threats? How does security mitigate these risks? How do we balance the costs and trade-offs of our security solutions? CSC 382: Computer Security Slide #7 9/11 Most devastating terrorist attack in history. – Low-tech. – Innovative. • Completely different than earlier hijackings. • We thought we had solved airplane bombings by ensuring passengers were on same flight as baggage. – What were the security responses? • How effective were the responses? • What were the costs? CSC 382: Computer Security Slide #8 What is Security? Security is the prevention of certain types of intentional actions from occuring in a system. – – – – These potential actions are threats. Threats that are carried out are attacks. Intentional attacks are carried out by an attacker. Objects of attacks are assets. CSC 382: Computer Security Slide #9 Safety vs Security Adversary: An intelligent attacker who intentionally causes the system to fail. Safety • Home: fire alarm. • Car: crumple zones. • Computer: UPS. Security • Home: door lock. • Car: alarm. • Computer: Login password. Safety and security can interact: Who is watching your computer room after the fire alarm was pulled? CSC 382: Computer Security Slide #10 What are threats? • What threats can you think of to your home? • To your money (including bank accounts, checks, credit and debit cards)? • To your home computer? CSC 382: Computer Security Slide #11 What are threats? • Home: • Computer: – Burglary – Fire – Vandalism • Money (cash/credit): – – – – Theft. Counterfeiting. Signature forgery. Identity theft. CSC 382: Computer Security – – – – – Viral/worm infection. Adware/spyware. Denial of service. Data destruction. Physical destruction (overheat, flash “ROM” overwriting) – Use of computer for felonious purposes. Slide #12 Digital Threats: More of the Same • • • • • • • Theft Vandalism Extortion Con Games Fraud Stalking Voyeurism CSC 382: Computer Security Slide #13 Digital Threats: What’s Different • Automation – Salami Attack from Office Space. • Action at a Distance – Volodya Levin, from St. Petersburg, Russia, stole over $10million from US Citibank. Arrested in London. – Operators of CA BBS tried and convicted in TN court because TN had d/led pornography f/ CA. • Technique Propagation – Criminals share techniques rapidly and globally. CSC 382: Computer Security Slide #14 Classes of Threats • Disclosure • Deception • Disruption • Usurpation CSC 382: Computer Security Slide #15 Classes of Threats • Disclosure – unauthorized access to data – Examples • copyright infringement • unauthorized CC use • Deception – acceptance of false data – Examples • Anti-spam filter techniques • “Social engineering” CSC 382: Computer Security Slide #16 Classes of Threats • Disruption – interruption of correct system operation – Examples: • DDOS attacks • Usurpation – unauthorized control of system component – Example: Nicholas Jacobsen • Controlled T-mobile’s systems in 2004 • Monitored e-mail, downloaded web-cam photos • Sold customer records (incl SSN, voicemail pw, etc) CSC 382: Computer Security Slide #17 Types of Threats • Snooping – interception of data – Examples: • Reading email, or intercepting cleartext passwords. • ECHELON. • Modification – Examples: • Changing student grades in War Games. • Web site defacing (>1500/month recorded at attrition.org in 2001) • Spoofing – impersonation – Examples: • Spam emails almost always spoof source address. • The many Citibank phishing scams. CSC 382: Computer Security Slide #18 Types of Threats • Repudiation of Origin – Deny ordering goods. • Denial of Receipt – Deny receipt of payment or goods. – Examples • eBay • Credit card payments. • Denial of Service – Examples: • 2000: “Mafiaboy” DDOS takes down Amazon, eBay, Yahoo. • Filling up disk with spam, unauthorized copies of files. CSC 382: Computer Security Slide #19 Current Threat Information • • • • • SANS Internet Storm Center Bugtraq CERT Packet Storm Risks Digest CSC 382: Computer Security Slide #20 ISC Survival Time Graph CSC 382: Computer Security Slide #21 Who are the Attackers? • Hackers vs Crackers • Levels of attackers – Developer • Finds new security vulnerabilities • Writes tools and exploits – User • Understands tools; modifies tools/exploits – Script Kiddie CSC 382: Computer Security Slide #22 Who are the Attackers? • Criminals. – 1993: Thieves installed bogus ATM at Manchester Mall. Saved account#s + PINs. • Organized crime. – 2000: Mafia-led organization members arrested for attempt to steal $680million from Bank of Sicily. • Malicious insiders. – 2001: Mike Ventimiglia deletes files of his employer, GTE. $200,000 damage. • Industrial espionage. – 2001: Verdicts in Cadence Design Systems vs. Avant against 7 employees incl CEO. 5 sentenced to jail. CSC 382: Computer Security Slide #23 Who are the Attackers? • Press. – 1998: Cincinnati Enquirer reporter Michael Gallagher breaks into Chiquita Fruits voicemail to expose illegal activities. • Police. – 1997: LAPD illegal wiretapping scandal. • Terrorists. – 1999: DOS attacks and web defacements against NATO country computers during Kosovo bombings. • National Intelligence. – 2000: Former CIA Directory Woolsey admitted to using ECHELON information to help US companies win foreign contracts. CSC 382: Computer Security Slide #24 Policies and Mechanisms • Policy states what is, and is not, allowed – Policy defines “security” for the site/system/etc. – Policies may be written as: • Natural language. • XML-based formal policy language. • Form mathematics. – Composition of policies • If policies conflict, discrepancies may create security vulnerabilities. CSC 382: Computer Security Slide #25 Policies and Mechanisms • Mechanisms enforce policies. • Technical mechanisms: – – – – Alarms. Access Control: locks and ACLs. Authentication: biometrics or passwords. Cryptography. • Human mechanisms: – Guards. – Hiring policies. – Incident response procedures. CSC 382: Computer Security Slide #26 Types of Mechanisms Secure Precise Broad Set of reachable states. Set of secure states. CSC 382: Computer Security Slide #27 Goals of Security • Prevention – Prevent attackers from violating security policy • Detection – Detect attackers’ violation of security policy • Recovery – Stop attack, assess and repair damage • Survivability – Continue to function correctly even if attack succeeds CSC 382: Computer Security Slide #28 NSTISSC Security Model CSC 382: Computer Security Slide #29 Components of Security • Confidentiality – Keeping data and resources hidden. Privacy. • Integrity – Preventing unauthorized changes to data or resources. • Availability – Enabling access to data and resources CSC 382: Computer Security Slide #30 Confidentiality • Authentication – Passwords, mother’s maiden name • Corporations – Trade secrets, e.g., the formula for Coca Cola. • Databases – SSN, Driver’s license • Governments – National security – Embarrassing information: www.thememoryhole.org CSC 382: Computer Security Slide #31 Integrity • Data Integrity – content of the information. – ex: 2005 Walmart $1.5 million bar code scam. • Origin Integrity (authentication) – source of the information. – ex: 1997 Kurt Vonnegut MIT commencement address email. Vonnegut was not the 1997 speaker and the content wasn’t his. • Prevention vs Detection CSC 382: Computer Security Slide #32 Availability • Prevent loss of system access. • Denial of service attacks common. – Easy to launch, difficult to track down. – Can be just part of another attack CSC 382: Computer Security Slide #33 States of Information 1. Storage – Information not currently being accessed. 2. Processing – Information currently being used by processor. 3. Transmission – Information in transit between one node and another. CSC 382: Computer Security Slide #34 Security Measures • Technology. – Hardware/software used to ensure confidentiality, integrity, or availability. • Policy and practice. – Security requirements and activities. • Education, training, and awareness. – Understanding of threats and vulnerabilities and how to protect against them. CSC 382: Computer Security Slide #35 How can we evaluate security solutions? 1. What assets are you trying to protect? 2. What are the risks to those assets? 3. How well does the security solution mitigate those risks? 4. What other risks does the security solution cause? 5. What costs and trade-offs does the security solution impose? CSC 382: Computer Security Slide #36 Aspects of Risks • To evaluate a risk, we need to evaluate both: – Probability of risk occurring. – Cost incurred by risk if it occurs. • Minimize product of probability and cost. • Risks are impacted by environment. – Building a house in a flood plain incurs additional risks beyond that of house itself. – Similarly, installion and configuration options impact risk of software systems. CSC 382: Computer Security Slide #37 Security is a matter of Trade-offs • Security is only one of many system goals: – – – – – – Functionality Ease of Use Efficiency Time to market Cost Security CSC 382: Computer Security Slide #38 Cost-Benefit Analysis • Is it cheaper to prevent violation or recover? – Cost of good network security: • Money, time, reduced functionality, annoyed users. • Large and ongoing. – Risks of bad network security: • Angry customers, bad press, network downtime. • Small and temporary. CSC 382: Computer Security Slide #39 Security Liability • Product liability: – Tires: Continental recalled Ford SUV tires in 2002 due to wire and vibration problems. – Software: Manufacturer not liable for security flaws. • Since Microsoft isn’t liable for Windows security failures, why would they want to sacrifice money, time, functionality, and ease of use for security? CSC 382: Computer Security Slide #40 Security: Laws and Customs • Are desired security measures illegal? – cryptography export before 2000 – is it legal to monitor security breakins? – international commerce • Will users circumvent them? – writing down passwords – removing file ACLs CSC 382: Computer Security Slide #41 Airport Security Let’s consider the issue of airport security again from the standpoint of what we’ve learned. Develop a solution, keeping the 5 questions in mind: 1. What assets are you trying to protect? 2. What are the risks to those assets? 3. How well does the security solution mitigate those risks? 4. What other risks does the security solution cause? 5. What costs and trade-offs does the security solution impose? CSC 382: Computer Security Slide #42 Human Issues: Organizations • Low priority – Security costs, but doesn’t produce income. – Lack of liability reduces costs of bad security. • Variable impact – Cost of security violation highly variable. – Insurance converts variable risk to fixed cost, but risk too variable for much involvement so far. • Power and responsibility – Personnel responsible for security often don’t have power to enforce security. CSC 382: Computer Security Slide #43 Human Issues: People Problems • Social engineering – Kevin Mitnick testified before Congress “I was so successful in that line of attack that I rarely had to resort to a technical attack.” • Circumvention – Users write down passwords, leave screens unlocked. • Insider attacks CSC 382: Computer Security Slide #44 Assumptions • Security rests on assumptions specific to type of security required and environment. • Example: – TCP/IP designed for pre-commercial Internet. • Assumed only legitimate admins had root access. • Trusted IP addresses, since only root can set IP addr. • What happens to network when Windows 95 systems added to network, where desktop user has all privileges? CSC 382: Computer Security Slide #45 Trust and Assumptions • Underlie all aspects of security • Policies – Unambiguously partition system states into secure and insecure sets of states. – Correctly capture security requirements. • Mechanisms – Assumed to enforce policy. – Support mechanisms (compilers, library, hardware, networks, etc.) work correctly. CSC 382: Computer Security Slide #46 How much do you trust? • Ken Thompson’s compiler hack from “Reflections on Trusting Trust.” – Modified C compiler does two things: • If compiling a compiler, inserts the self-replicating code into the executable of the new compiler. • If compiling login, inserts code to allow a backdoor password. – After recompiling and installing old C compiler: • Source code for Trojan horse does not appear anywhere in login or C compiler. • Only method of finding Trojan is analyzing binary. CSC 382: Computer Security Slide #47 Assurance • How much can you trust a system? • Example: – Purchasing aspirin from a drugstore. – Bases for trust: • Certification of drug by FDA. • Reputation of manufacturer. • Safety seal on bottle. CSC 382: Computer Security Slide #48 Assurance • Assurance performed during all parts of software design cycle. – – – – Specification Design Implementation Testing CSC 382: Computer Security Slide #49 Why Assurance? • Security is NOT an add-on feature • Penetrate and Patch – – – – You can only patch holes you know about. Patches are often rushed and buggy. Patches often attack only the symptom. Patches are often not applied in time. • Patch Tuesday – MS releases security patches every 2nd Tuesday – Jan 11th: 2 critical (1 impacts SP2), 1 important CSC 382: Computer Security Slide #50 Assurance: Specification • Requirements Analysis – What resource should you protect? – Who are you protecting it from? – How long do you need to protect the resource? • Potential problems – Early Design: How are you going to protect it? – Vague or silent areas of spec => vulnerabilites CSC 382: Computer Security Slide #51 Assurance: Design • How system will meet specification • How to protect each resource? – Which components need each resource? – How data flows between components? – How much do components trust each other? • Secure design principles • Design more important than implementation CSC 382: Computer Security Slide #52 Assurance: Implementation • Malicious input – Buffer overflows – Code injection • Race conditions • Cryptography problems – Randomness problems – Don’t write your own CSC 382: Computer Security Slide #53 Assurance: Testing • Formal proof techniques – Difficult to get right – Assumptions can be wrong • Testing – Unit tests – Integration tests • Common Criteria CSC 382: Computer Security Slide #54 Tying Together Threats Policy Specification Design Implementation Operation CSC 382: Computer Security Slide #55 Key Points • Policy defines security; mechanisms enforce policy. • Components of security – Confidentiality – Integrity – Availability • Evaluating risk and security solutions. – Security is a matter of trade-offs. • Security is not an add-on; it must be designed into a system from the beginning of development. • The human factor. CSC 382: Computer Security Slide #56 Assignment • Analyze the security of your home PC – Check for spyware, using at least two tools such as Ad-aware, Spybot S&D, Hijack This, Windows Antispyware (Beta), etc. – Use the Sites and Tools pages as starting point. • Bring a one-sheet summary of what you found (noting differences between tools) and how your discoveries changed your perception of your home PC’s security to share in class on Thursday. CSC 382: Computer Security Slide #57 References 1. 2. 3. 4. 5. 6. Anderson, Ross, Security Engineering, Wiley, 2001. Bishop, Matt, Introduction to Computer Security, Addison-Wesley, 2005. Neumann, Peter (moderator), Risks Digest, http://catless.ncl.ac.uk/Risks/ SANS Internet Storm Center, http://isc.sans.org/ Schneier, Bruce, Beyond Fear, Copernicus Books, 2003. Thompson, Ken, “Reflections on Trusting Trust”, Communication of the ACM, Vol. 27, No. 8, August 1984, pp. 761-763 (http://www.acm.org/classics/sep95/) CSC 382: Computer Security Slide #58