* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Secure Solutions for Wireless, VPN and Perimeter
Outlook.com wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Computer security wikipedia , lookup
Access control wikipedia , lookup
Mobile security wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Deep packet inspection wikipedia , lookup
Cross-site scripting wikipedia , lookup
Certificate authority wikipedia , lookup
Proxy server wikipedia , lookup
Unix security wikipedia , lookup
Security-focused operating system wikipedia , lookup
Distributed firewall wikipedia , lookup
Authentication wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Identity Management and Security
Summit - Security Session 2
Jamie Sharp CISSP
Security Consultant
Microsoft Services
Agenda
Wireless
VPN
Perimeter
Call to Action
Wireless
Current Situation
Huge fear of wireless
Rooted in misunderstandings of
security
Wireless can be made secure
Takes work
Need to understand problem
Need to plan for secure solution
Wireless Antennas
How To Build A Tin Can Waveguide Antenna
http://www.turnpoint.net/wireless/cantennahowto.ht
ml
Antenna on the Cheap (er, Chip)
http://www.oreillynet.com/cs/weblog/view/wlg/448
WEP
Secret key shared between access point
and all clients
Encrypts traffic before transmission
Performs integrity check after transmission
WEP uses RC4, a stream cipher
[key] XOR [plaintext] [ciphertext]
Maybe double-XOR for “better” security? Hah!
[ciphertext] XOR [key] [plaintext]
WEP - Wired Equivalent Privacy
WEP Issues
Key and initialisation vector reuse
Known plaintext attack
Partial known plaintext attack
Weaknesses in RC4 key scheduling algorithm
Authentication forging
Realtime decryption
More Information
http://www.isaac.cs.berkeley.edu/isaac/wep-faq.html
WEP - Wired Equivalent Privacy
Solution Today - 802.1X
Port-based access control mechanism
defined by IEEE
Works on anything, wired and wireless
Access point must support 802.1X
No special WIC requirements
Allows choice of authentication methods
using EAP
Chosen by peers at authentication time
Access point doesn’t care about EAP methods
Manages keys automagically
No need to preprogram WICs
Solution Today - EAP
Link-layer security framework
Simple encapsulation protocol for authentication
mechanisms
Runs over any link layer, lossy or lossless
No built-in security
Doesn’t assume physically secure link
Authentication methods must incorporate their own
security
Supported authentication methods
TLS: authentication server supplies certificate
IKE: server demonstrates possession of preshared key
or private key (certificate)
Kerberos: server demonstrates knowledge of session
key
PEAP: any pluggable method supporting mutual
authentication
AuthN Supported in Windows
EAP-MD5 disallowed for wireless
Can’t create encrypted session between
supplicant and authenticator
Would transfer password hashes in the clear
Cannot perform mutual authentication
Vulnerable to man-in-the-middle attacks
EAP-TLS in Windows XP release
Requires client certificates
Best to have machine and user
Service pack 1 adds protected EAP (PEAP)
Protected EAP (PEAP)
Extension to EAP
Allows use of any secure authentication
mechanism for EAP
No need to write individual EAP-enabled methods
Windows PEAP allows:
MS-CHAPv2—passwords
TLS (SSL channel)—certificates
PEAP-EAP-TLS a little slower than EAP-TLS
SecurID—but not tested/supported for wireless
For many deployments, machine and user
passwords still are necessary
PEAP enables secure wireless now
Allows easy migration to certificates and smartcards
later
Clarifying Terminology
802.11 is the specification for over-the-air
wireless networks
802.1X is a PHY-independent specification
for port-based access control
Combining them makes sense
There is no such thing as 802.11X
But there is work on something called 802.11i
Association and Authentication
The 802.11 association happens first
Need to talk to the AP and get an IP address
Open authentication—don’t have the WEP key
yet
Access beyond AP prohibited until authN
succeeds
AP drops non-EAPOL traffic
After key is sent in EAPOW-key, access beyond
AP is allowed
Security conversation between supplicant
and authentication server
Wireless NIC and AP are passthrough devices
802.1X over 802.11
Supplicant
802.11 association
Authenticator
Access blocked
EAPOL-start
EAP-request/identity
EAP-response/identity
RADIUS-access-request
EAP-request
RADIUS-access-challenge
EAP-response (credentials)
RADIUS-access-request
EAP-success
RADIUS-access-accept
EAPOW-key (WEP)
Access allowed
Authentication
Server
802.1X & EAP Provides
Mutual device authentication
Workstation and authentication server
No rogue access points
Prevents man-in-the-middle attacks
Ensures key is transferred to correct entity
User authentication
No unauthorized access or interception
WEP key uniqueness and regeneration
System Requirements
Client: Windows XP service pack 1
Server: Windows Server 2003 IAS
Internet Authentication Service—our RADIUS server
Certificate on IAS computer
Backporting to Windows 2000
Client and IAS must have SP3
No zero-config support in the client
See KB article 313664
Supports only TLS and MS-CHAPv2
Future EAP methods in XP and 2003 might not be
backported
WPA - An Interim Until 802.11i
Goals
Require secure networking
Solve WEP issues with software and firmware
upgrades
Provide secure wireless for SOHO
No RADIUS needed
Be forward compatible with 802.11i
Be available today
WPA Wireless Security Update in Windows XP
http://support.microsoft.com/?kbid=815485
The Future - 802.11i
IEEE is working on 802.11i
Replacement for WEP
Includes TKIP (Temporal Key Integrity Protocol)
, 802.1x, and keyed integrity check
Mandatory AES (Advanced Encryption
Standard)
Addresses all currently known vulnerabilities
and poor implementation decisions
Need to be IEEE member to read work in
progress
Expected ratification in Q4 2003
VPN
Remote Access Trends
Explosive growth of mobile users
63.4M handheld computers to be sold by 2003*
Increasing methods of access
Application specific access
Combined functionality
VPN and Firewall combined platforms
* Source - (IDC)
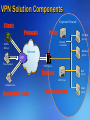
VPN Solution Components
Corporate Network
Clients
Protocols
Policy
File/Print
Server
Domain
Controller
Mobile
Worker
Internet
Database
Server
ISP
Telecommuter
VPN Server
Gateway
Web
Server
IAS Server
Administrator
Deployment Tools
Authentication
Email
Server
Windows VPN Components
Client
Integrated VPN client
Gateway
Routing and Remote
Access Services
Protocols
Platform Support for
Industry Standard
Protocols
Authentication
Policy
Deployment
Tools
Internet Authentication
Services
& Active Directory
Connection Manager
Administration Kit
Windows XP
Windows Server
2003
Windows XP Professional
Client
Gateway
Integrated VPN Client
Initiates connection to remote
networks.
Protocols
Authentication
Policy
Deployment
Tools
Simplicity
New Connections Wizard
Automatic protocol detection
Security
Client state check with
“Quarantine”
Supports advanced security and
encryption
Supports certificates, smart
cards, token cards and more
Windows Server Gateway
Client
Gateway
Protocols
Authentication
Policy
Deployment
Tools
Routing and Remote Access Services
Link clients to private networks
• Security
• Secure remote access connection
technology
• Per session VPN packet filters
• Performance
• Offload hardware encryption
supported
• Load Balance support for VPN
• Manageability
• Integrated Active Directory™
authentication
• Supports standards based
Authentication Servers (RADIUS)
Windows XP & Server 2003
Protocols
Client
Gateway
Protocols
Authentication
Policy
Deployment
Tools
Industry Standard Protocols
Specify link capabilities and
encrypts data traffic.
• Security
• Advanced security with L2TP/IPSec
tunneling protocols.
• PKI authentication support
• Legacy user authentication support
with PPTP
• Support for Smart Cards with EAP
• Interoperability
• IETF standards based solutions
• Network Transparency
• Multi-protocol and Multi-cast support
Windows Server Authentication
Client
Gateway
Protocols
Authentication
Policy
Deployment
Tools
Internet Authentication Services
Validates user access to the
network
Directory Integration
• Integrates with Active Directory
Interoperability
• Authenticates other 3rd party VPN
products that support RADIUS
Security
• Support for “Quarantine”
New authentication support
• Smart Cards, Token Cards,
Fingerprint scanners and more
Windows Server Policies
Client
Gateway
Protocols
AD Group Policy
Network policies for users to gain access
Security
• Enforcement of policies to check the
state of the client via quarantine
service
• Restricted access based on group
membership
Authentication
Policy
Deployment
Tools
Manageability
• Centralized user management with
integration of AD and authentication
service
Windows Server Deployment
Tools
Client
Gateway
Protocols
Authentication
Policy
Deployment
Tools
Connection Manager Administration Kit
Create and manage client connection
configurations
Central Configuration
• Create pre-configured dial-up
connection software for simplified
client experience
Extensibility
• Customizable help files, help-desk
numbers, and more
• Configurable connect actions to
launch custom code before or after
connection
Phonebook Management
• Automatic phonebook updates for
local ISP access numbers
Network Access Quarantine
Windows Server 2003
Control
Internet Authentication Service
Internet
Remote User
Corpnet
RRAS
IAS
Quarantine
Active
Directory
Ensures that remote systems meet corporate
security standards
Reduces risk of security compromises
Reduces the spread of viruses
Whitepaper: Network Access Quarantine Control in
Windows Server 2003
http://www.microsoft.com/windowsserver2003/techinfo/overview
/quarantine.mspx
Perimeter
What is ISA Server?
High Performance Web cache
Multi-layered firewall
Packet Level (static and dynamic filters)
Circuit Level (stateful inspection)
Application Level (payload inspection)
Network Address Translation (NAT)
Centralised or Distributed Management
ICSA Certified
Common Criteria EAL2 Certified
ISA = Defence in Depth
Provide secure, fast Internet/Intranet
access with proxy and caching
Secure Exchange and Web Servers at the
application layer
Secure edge gateway with integrated VPN,
firewall and caching
Current Situation
Traditional firewalls focus on packet filtering
and stateful inspection
Today’s attacks freely bypass this
Ports are overloaded & can be exploited
Port 80 Yesterday—Web browsing only
Port 80 Today—Web browsing, OWA, XML Web
Services, …
Packet filtering and stateful inspection are
not enough
Application-layer Firewalls are
Necessary
Application-layer firewalls are required to stop
these attacks
Enable deep content inspection
Requirement for network security today
to internal
Internet
network
Packet filtering
firewall/router
Applicationlayer firewall
“To provide edge security in this application centric
world…application-layer firewalls will be required”
—John Pescatore, Gartner
ISA Server = Application-layer
Security
Packet filtering & stateful inspection
Application-layer filtering
Imperative for network security today
Potential to detect/inspect traffic regardless of port
Advanced proxy architecture
Internet traffic never routed to the internal network
Extensible/pluggable architecture
30+ partners: netIQ, Trend Micro, Rainfinity, Authenex,
N2H2, Venation, ISS…
Best firewall for Windows environment
Web Publishing
Occurs at the application level
ISA understands HTTP
Can publish multiple web servers using one IP
address
Can Bridge and Tunnel SSL requests
Allows secure access to the web server
Accelerates performance
Off-load SSL
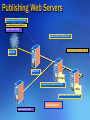
Publishing Web Servers
www.nwtraders.msft/europe
www.nwtraders.msft/africa
www.contoso.msft
www.nwtraders.msft/europe
www.nwtraders.msft/africa
Internet
ISA Server
Europe
europe.internal.nwtraders.msft
Africa
africa.internal.nwtraders.msft
Internal Network
www.contoso.msft
Server Publishing
Occurs at the application level
ISA understands SMTP, DNS, FTP, POP, RPC,
H.323 and Streaming media OOB
Allows secure access to published services
All incoming and outgoing requests inspected
by ISA
Can limit rules to specific clients
Single IP visible to outside world
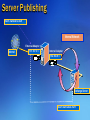
Server Publishing
mail1.nwtraders.msft
Internal Network
External Adapter
Internet
131.107.3.1
Internal Adapter
192.168.9.1
Exchange Server
mail1.nwtraders.msft
ISA Deployment Benefits
Cost-effective to build, monitor and
operate
Integrated with Windows security and
compatible with non-Windows hosts
Saves bandwidth by caching frequently
accessed content
Provides a firewall engine with
application layer inspection
Enables QOS, detailed reporting,
strong user authentication and high
availability
SMTP Filter
Help filter out unwanted e-mail
Uses ISA Server application-layer filtering
ability
Filter e-mail with increased reliability and
security on several attributes
Sender
Domain
Keyword
Attachment extension, name, size
Any SMTP command and its length
Exchange RPC
RPC 101
Client accesses
Client connects
application
over to
portmapper
on server
Client knows
UUID port
learned
(port 135/tcp)
of service it wants
234-1111…}
RPC client
(Outlook)
Portmapper responds
Client asks,
“What
with the
port and closes
port is associated
the connection
with my UUID?”
4402/tcp
135/tcp
Service
Exchange
AD replication
MMC
UUID
Port
4402
{12341234-1111…
4402
{01020304-4444…
3544
{19283746-7777…
9233
RPC server
(Exchange)
Due
tomatches
the random
Server
UUID to nature of RPC, this is not
the current
port…
feasible
over
the Internet
RPC services grab random
high ports
they high
start, ports
Allwhen
64,512
servertraditional
maintains table
firewalls
& port 135 must be opened on
Exchange RPC Filter
Protect remote Outlook e-mail without a VPN
Internet
Outlook
ISA Server
Exchange
Server
ISA Server Exchange RPC filter
Only port 135 (portmapper) is open
High ports are opened and closed for Outlook clients as
necessary
Inspects portmapper traffic at application-layer
Only Exchange UUIDs allowed, nothing else
Exchange RPC Filter
Protect remote Outlook e-mail without a VPN
Enforce RPC encryption
Outlook RPC encryption can be enforced centrally
Enable outbound RPC communication
Outlook clients behind ISA Server can now access
external Exchange Servers
RPC
External
network
Exchange
Server
Internal
network
ISA Server with
Feature Pack 1
Outlook
client
URLScan 2.5 for ISA Server
Help stop evolving types of Internet attacks
Filters incoming requests based on rules
set
Helps protect from attacks which
request unusual actions
have a large number of characters
are encoded using an alternate character set
Can be used in conjunction with SSL
inspection to detect attacks over SSL
RSA SecurID Authentication
Help control access with 2-factor authentication
ISA Server prompts user for SecurID username
and PASSCODE
RSA ACE/Agent on ISA Server passes credentials
to the RSA ACE/Server for validation
When credentials are validated
User is granted access to the protected content
Cookie is delivered to the user's browser for
subsequent activity during the session
Authentication Delegation
Help ensure only valid traffic is allowed
For SecurID and basic authentication
Authentication happens at ISA Server
Eliminates multiple authentication dialogs
Only valid traffic allowed to the internal network
Enabled per Web publishing rule
ISA Server pre-authenticates
users and
their
activity the credentials
Client requests protected
ISAlogs
Server
forwards
content from Web server to the protected Web or OWA server
Internet
client
ISA Server
Web server
Link Translator
Eliminate the need to re-architect intranet sites
Translates hyperlinks within responses
Intranet computer names to those of externally
available computers
Including:
HTTP
HTTPS; SharePoint Portal Server
mktg.example.com/
http://
int-mktg/
http://mktg.example.com/sales.html
http://int-mktg/sales.html
http://
Client requests
LINK TRANSLATOR
www.example.com/index.html
http://
Web server
(int-mktg)
Internet
client
ISA Server
Feature Pack 1
Web server
(www.example.com)
Guidance
Answer commonly asked ISA Server questions
ISA Server Feature Pack 1 walkthroughs
OWA, link translation, RSA SecurID
Web Publishing
Includes many different scenarios
Troubleshooting information
Exchange Server Publishing
Includes Exchange RPC filter, POP and IMAP
Troubleshooting information
Additional Documentation
Many subjects, including client types and creating
digital certificates
Call to Action
Eliminate fear of wireless networks
Revisit corporate remote access strategy
Evaluate the security of your current
Exchange and Web Server deployment
Regularly check
www.microsoft.com/security
© 2003 Microsoft Corporation. All rights reserved.
This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary.