* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Chapter 14 Network Security
Cyberwarfare wikipedia , lookup
Information security wikipedia , lookup
Airport security wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Network tap wikipedia , lookup
Denial-of-service attack wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Deep packet inspection wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Wireless security wikipedia , lookup
Security-focused operating system wikipedia , lookup
Mobile security wikipedia , lookup
Computer security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Unix security wikipedia , lookup
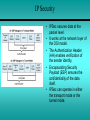
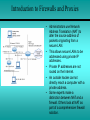
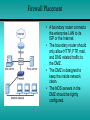
Module 12 Network Security 12.1 - Developing a Network Security Policy 12.2 - Threats to Network Security 12.3 - Implementing Security Measures 12.4 - Appling Patches and Upgrades 12.5 - Firewalls Developing a Network Security Policy Accessing Security Needs • • • • There must always be a delicate balance between security and accessibility. The more accessible a network is, the less secure it is. When it comes to a computer network, how much security is enough? There are several factors to consider: – The type of business in which the company engages – The type of data stored on the network – The management philosophy of the organization Acceptable Use Policy • The first step in creating a security policy for a company network is to define an Acceptable Use Policy (AUP). • An AUP tells the users what is acceptable and allowed on the company network. • To view some examples of AUPs, visit these websites: Username and Password Standards • Usually the system administrator will define the naming convention for the usernames on a network. • A common example is the first initial of the person's first name and then the entire last name. • A complex username naming convention is not as important as having a complex password standard. • When assigning passwords, the level of password control should match the level of protection required. Rules for Network Access • A system administrator who assigns the proper permissions on the share drives and directories defines the rules for network access. • By assigning the proper security permissions on the network, the system administrator should know who has access to specific directories. • Proper maintenance by the system administrator will be required to examine auditing logs of attempts that have been made to access the network shares. Policy for Disposal of Materials • Hardware, software, and data should never just be thrown away. • There are strict regulations that should be followed to control the disposal of computer components. • The system administrator is responsible for developing a policy based on environmental and safety guidelines for hardware that no longer works. • To view some examples of the disposal of materials policies visit these websites: Virus Protection Standards • Place proper filters and access lists on all the incoming gateways to protect the network from unwanted access. • To prevent viruses, e-mail policies also need to be developed that state what may be sent and received. • These websites provide sample e-mail policy standards: Online Security Resources • Web-based resources offer critical information and powerful tools that can be used to protect a network. Some of the best online security resources are the NOS manufacturer websites • To view examples of the online security resources visit these websites: Server Room Security • To protect computing resources, make sure that there is a locked door and four walls between the server and the rest of the area. • There are a variety of ways to permit or deny access to that area after it has been secured. • The lock and key is a tried and true method for physically securing the server environment. • This method works great if there are a limited number of people who need access. Server Room Security • Using a combination locking mechanism is similar to a lock and key. The advantages to this method: – Keys no longer have to be distributed – Key control lists no longer have to be maintained – Combinations can also be reset when needed • The one drawback to this model is that it is very easy to share a combination with someone not authorized. • Card readers are the most common of the access control mechanisms. • They work by reading a magnetic signature off an access card or token. • A biometrics based access control system uses measurable physical characteristics to authenticate users into an environment (fingerprints, retinal patterns, or speech). Anti-Theft Devices for Server Hardware • A common security measures is the locking mechanism included as part of the server itself. • Most high end servers enable the case to be locked, and in many cases to lock the drives into the server chassis. • Almost all rack systems include locking front and back doors. • Removable media drive locks are locking devices. – These devices fit over the floppy drive, zip drive, and CDROM drive to prevent unauthorized access. • Some servers are shipped with holes in the cases, which are predrilled for a padlock. • Alarms are the final add-on, and best suited for the shared office environment. Securing Removable Media • Security of removable media includes the following: – Removable disks, floppy, Zip, Jaz, LS120, CD-RW – Removable hard drives – Backup media, tapes • Several methods are used to ensure the security of removable media: – – – – Lock the media in an office Place the media in a locked cabinet with strict key control Place the media in a safe, or a fire-resistant safe Engage a third-party firm to store the tapes in their secure facility Threats to Network Security Overview: Internal/External Security • The Internet essentially works by following rules that are open to the public. • If one studies the rules enough, one is bound to find loopholes and weaknesses that can be exploited. • The number of individuals, organizations, and institutions connected to the Internet are growing. • Connecting to the Internet opens the door to network intruders. Outside Threats • Several outside sources can cause attacks: • Hackers - the true hacker desires to dissect systems and programs to see how they work. • Crackers - those that break in to computer systems to tamper with, steal, or destroy data. • Virus - it causes some unexpected and usually undesirable event. • Worms - a self-replicating virus that does not alter files but resides in active memory and duplicates itself. • Trojan horse - is a program that presents itself as another program to obtain information Denial of Service (DoS) • A DoS attack occurs when the targeted system cannot service legitimate network requests effectively. • As a result, the system has become overloaded by illegitimate messages. • DoS attacks originate from one host or a group of hosts. • When the attack comes from a coordinated group of hosts, such attacks are called Distributed DoS (DDoS). • A common DoS attack is to overload a target system by sending more data than it can handle. Denial of Service (DoS) • There are several specific types of DoS attacks: – A buffer overflow attack is designed to overwhelm the software running on the target system. – The so-called ping of death is a well known buffer overflow DoS attack. – The TCP synchronization (SYN) attack exploits the TCP protocol three-way handshake. • The attacker sends a large volume of TCP synchronization requests (SYN requests). Distributed Denial of Service (DDoS) • Before the hacker can attack the ultimate target, a "fleet" of "zombies" (unsecure host with a permanent Internet connection) must be coordinated for the attack. • The hacker takes advantage of the zombie's lack of security. • The hacker breaks in to the system either directly or through an e-mail virus. • The goal of the break in or virus is to install software on the zombie system. • The hacker uses the zombies to launch a DDoS attack on the ultimate target. Well Known Exploits • Each combination of NOS and application software contains it’s own unique set of vulnerabilities and weaknesses. • Threats to network security comes from individuals with sophisticated tools. • Some of these individuals are often called "script kiddies". • Script kiddy is a negative term used to describe immature individuals that use scripts, software programs, or techniques created by other, more skilled crackers. Trojan Horse Programs • A Trojan horse is a program that presents itself as another program to obtain information. For example, there is a Trojan horse that emulates the system login screen. • When users type in their account name and password, the information is stored or transmitted to the originator of the Trojan horse. The username and password Inside Threats • Corporate espionage is the most sophisticated type of internal security threat. • Employees can be approached by competing companies. • There are freelance corporate spies who take assignments on a contract basis. • Internal security breaches can also be the result of rebellious users who disagree with security policies. • While not accidental, these breaches are not designed to cause harm. Implementing Security Measures File Encryption • File encryption is a way of encrypting data stored on a computer disk so that it is unreadable to anyone but the creator of the data. • Windows 2000 includes a file encryption function. • Windows 9x and Windows NT do not. • Third party encryption programs are available for OSs: – PC Guardian, Deltacrypt, Winzap IP Security • IPSec secures data at the packet level. • It works at the network layer of the OSI model. • The Authentication Header (AH) enables verification of the sender identity. • Encapsulating Security Payload (ESP) ensures the confidentiality of the data itself. • IPSec can operate in either the transport mode or the tunnel mode. Secure Sockets Layer (SSL) • SSL was developed by Netscape to provide security for its web browser. • It uses public and private key encryption. • SSL operates at the application layer and must be supported by the user application. E-mail Security • E-mail users think they have the same expectation of privacy when sending e-mail as they do when sending a letter through the postal service. • A more accurate expectation would be to assume that the email is like a postcard that can be read by anyone who handles it during its journey from sender to recipient. • They often travel through dozens of nodes or servers on their way from sender to recipient. Public/Private Key Encryption • One key is published and is widely available. • The other key is private and known only to the user. • Both keys are required to complete the secure communication. • This type of encryption, is also referred to as asymmetric encryption. • With this type of encryption, each user has both a public and a private key, called a key pair. Appling Patches and Upgrades Finding Patches and Upgrades • Patches are fixes to existing software code. • A NOS manufacturer typically provides security patches. • Microsoft now includes the option to use software called Windows Update with its operating systems. Selecting Patches and Upgrades • Software makers recommend installing software security patches immediately. • This is done to reduce exposure to known vulnerabilities. • Software venders release security updates as soon as they are available. • Understanding the effect on the system will help determine if an update, fix, or patch is necessary. Applying Patches and Upgrades • Periodically, NOS vendors issue updates to their network operating systems. These updates have various names: – Microsoft Service Packs – IBM Fixpacs – Novell Patches • These updates usually fix bugs or close security holes that have been found in the released version of the OS. • Download the updates from the network operating system vendor’s website. Firewalls Introduction to Firewalls and Proxies • A proxy is software that interacts with outside networks on behalf of a client host. • Typically, client hosts on a secure LAN request a web page from a server running proxy services. • The proxy server then goes out on the Internet to retrieve the web page. • The web page is then copied to the proxy server, this is referred to as caching. Introduction to Firewalls and Proxies • Administrators use Network Address Translation (NAT) to alter the source address of packets originating from a secure LAN. • This allows secure LANs to be addressed using private IP addresses. • Private IP addresses are not routed on the Internet. • An outside hacker cannot directly reach a computer with a private address. • Some experts make a distinction between NAT and a firewall. Others look at NAT as part of a comprehensive firewall solution. Packet Filtering • The most basic firewall solution is an IP packet filter. • To configure a packet filter, a network administrator must define the rules that describe how to handle specified packets. • The most basic firewall solution is an IP packet filter. • To configure a packet filter, a network administrator must define the rules that describe how to handle specified packets. Packet Filtering • Both TCP and UDP use port numbers to address specific applications running on a host. • Both TCP and UDP use port numbers to address specific applications running on a host. • Firewall software must guess at what connectionless traffic is invited and what connectionless traffic is not. • The most comprehensive form of packet filtering examines layer 3 and 4 headers and the layer 7 application data as well. • Layer 7 firewalls look for patterns in the payload of the packet. • This is done in an effort to determine what application is being used, such as HTTP, FTP, and so on. Firewall Placement • A boundary router connects the enterprise LAN to its ISP or the Internet. • The boundary router should only allow HTTP, FTP, mail, and DNS related traffic to the DMZ. • The DMZ is designed to keep the inside network clean. • The NOS servers in the DMZ should be tightly configured. Common Firewall Solutions • The PIX Firewall 515 uses TFTP for image download and upgrade. • It has a low profile design, 128,000 simultaneous sessions, and 170 Mbps thru-put. • The PIX Firewall 520 uses a 3.5inch floppy disk drive to load the image and upgrade. • It has an enterprise chassis design, 256,000 simultaneous sessions, and 240 Mbps thru-put. • The PIX Firewall is secure right out of the box. • Default settings allow all connections from the inside interface access to the outside interface. Common Firewall Solutions • The Cisco IOS Firewall Feature Set provides stateful packet filtering. • Another firewall solution is a UNIX host. • The UNIX host serves as a router, running packet filtering software such as ipfw, and/or NAT. • Home users have a variety of firewall options available as well. Using an NOS as a Firewall • In high-traffic environments, a specialized packet filtering and NAT solution is recommended. • A device such as a router or firewall appliance is designed to switch packets and manipulate them quickly. • A NOS running on ordinary hardware may be able to do the job. • However, it is not without adding latency and overhead on the server. • In low traffic environments, such as small offices and home networks, a NOS firewall solution is a good choice.