* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download A Primer on Computer Security
HTTP cookie wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Wireless security wikipedia , lookup
Security-focused operating system wikipedia , lookup
Cross-site scripting wikipedia , lookup
Cyberattack wikipedia , lookup
Microsoft Security Essentials wikipedia , lookup
Antivirus software wikipedia , lookup
Computer security wikipedia , lookup
Deep packet inspection wikipedia , lookup
Security and safety features new to Windows Vista wikipedia , lookup
Computer virus wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Mobile security wikipedia , lookup
Unix security wikipedia , lookup
Workstation Security –
Privacy and Protection from
Hackers
ISECON2002
Nov 2, 2002
Bruce P. Tis, Ph.D.
Simmons College
Boston, MA
1
Outline
Goals
Introduction
Attacks/Threats
Malware – viruses, worms, Trojan horses
and others
Privacy - Cookies/Spyware
Firewalls
Steps for protecting yourself
Interesting Web Sites
What Haven’t We Covered
2
Goals
Raise your consciousness regarding the
need for information security at the
workstation level
Review basic terminology and concepts
Discuss threats and how to resist them
Verifying workstation’s ability to resist an
attack
3
Introduction
4
What is security?
Computer Security deals with
the prevention and
detection of,
and the reaction to,
unauthorized actions by users of a
computer system or network.
5
Topics Include
Cryptology
Forensics
Standards
Management of
security/policies
Authentication
Intrusion Detection
Hacking
Privacy
Legal and Ethical
issues
IP Security
WEB Security
Network
Management
Malware
Firewalls
6
Why do we need to be
concerned about security
Economic loss
Intellectual Property loss
Privacy and Identity Theft
National Security
7
Economic Loss
Kevin Mitnick’s hacking spree allegedly
cost companies $291 million
Economic impact of recent malware
LoveLetter and CodeRed $2.6 billion each
Sircam $1.3 billion
Computer Economics estimates that
companies spent $10.7 billion to recover
from virus attacks in 2001
8
Radicati Group Inc study of economic
impact of malware
9
CERT
Computer Emergency Response
Team Coordination Center (CERT)
reports security incidents
An incident may involve one site or
hundreds (or even thousands) of
sites. Also, some incidents may
involve ongoing activity for long
periods of time.
10
CERT/CC Incidents
60000
50000
40000
30000
20000
10000
2001
2000
1999
1998
1997
1996
1995
1994
1993
1992
1991
1990
0
Year
11
Intellectual Property
Music piracy
Software piracy
Research data piracy
Industrial espionage
12
Privacy and Identity Theft
300,00 credit cards stolen at CD Universe
Identity theft has reached epidemic proportions
and is the top consumer fraud complaint in
America
Losses to consumers and institutions due to
identity theft totaled $745 million in 1997,
according to the U.S. Secret Service.
An estimated 700,000 consumers became
victims of identity theft during 2001 at a cost of
$3 billion.
Estimate of 900,000 for 2002.
13
National Security
Los Alamos loses top-secret hard drive
January 1990 AT&T long-distance
telephone switching system was crashed
for nine hours and approx 70 million calls
went uncompleted
Distributed attack on the 13 root DNS
servers two weeks ago
September 11 !!!!!!!!!!!!!!!!!!!!!!!
14
The National Strategy to Secure
Cyberspace draft issued in September
2002 clearly puts responsibility on the
end user to protect his/her personal
computer from hackers
Consumer education Web site
http://www.ftc.gov/bcp/conline/edcams/infosecurity/
National Cyber Security Alliance
http://www.staysafeonline.info
15
Attacks and Threats
16
Attacks/Threats
Physical
Access
Modification
Denial of Service
Repudiation
Invasions of Privacy
17
Physical Attacks
Hardware theft
File/Information Theft
Information modification
Software installation
18
Access Attacks
Attempt to gain information that the
attacker is unauthorized to see
Password pilfering
An attack against confidentiality
Snooping
Eavesdropping
Interception
19
Modification Attacks
An attempt to modify information an
attacker is not authorized to modify
An attack against information
integrity
Changes
Insertion
Deletion
20
Denial-Of-Service Attacks
Deny the use of resources to
legitimate users of a system
Denial
Denial
Denial
Denial
of
of
of
of
access
access
access
access
to
to
to
to
information
applications
systems
communications
21
Repudiation Attacks
Attack against the accountability of
information i.e. and attempt to give
false information or to deny that a
real event or transaction has
occurred
Masquerading
Denying an event
22
Privacy Attacks
Collection of information about
you
your computer configuration
your computer use
your surfing habits
23
Security Services
Security services are used to combat
attacks
Confidentiality (access)
Integrity (modification, repudiation)
Availability (denial of service)
Accountability ( access, modification,
repudiation)
Security mechanisms implement services
i.e. cryptography
24
Malware
Trap Door
Logic Bombs
Trojan Horses
Worms
Bacteria
Viruses
Mobile Code
25
Malware – collection of
techniques/programs that produce
undesirable effects on a computer system
or network
Differentiate based on
Needs host program
Independent
Replicate
Don’t replicate
26
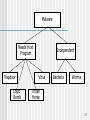
Malware
Needs Host
Program
Trapdoor
Logic
Bomb
Independent
Virus
Bacteria
Worms
Trojan
Horse
27
Trap Doors
Secret entry point to a program that
bypasses normal security access
procedures
Legitimate for testing/debugging
Recognizes some special input, user ID or
unlikely sequence of events
Difficult to detect at use
Must detect during software development
and software update
28
Logic Bombs
Code embedded in legitimate program
that is set to explode when certain
conditions met
Presence/absence certain files
Date
Particular user
Bomb may
Alter/delete files
Halt machine
Other damage
29
Trojan Horses
Apparently useful program or command
procedure containing hidden code which
performs harmful function
Trick users into running by disguise as
useful program
Doesn’t replicate itself
Used to accomplish functions indirectly
that an unauthorized user not permitted
Used for destructive purposes
30
Backdoor Trojans
Opens backdoor on your computer that
enables attackers to remotely access and
control your machine
Also called remote access Trojans
Attackers find your machine by scanning
ports used by Trojan
Common backdoor Trojans
Back Orifice
NetBus
31
Most anti-virus tools detect Trojans
Can also check open TCP ports
against list of known Trojan ports
Type netstat –an command
Look at listening ports
Lists of known Trojan port numbers
available via Google search
32
33
Worms
Programs that use network connections to
spread from system to system
Once active on a system can behave as
another form of malware
Propagates
Search for other systems to infect
Establish connection with remote system
Copy itself to remote system and executes
34
The Great Worm
Robert Morris released the most famous
worm in 1988
Crashed 6000 machines on the Internet
(10%)
Exploited bug in fingerd program
Bug in worm crashed machines which
prevented the worm from spreading
Estimated damage $100 million
Three years probation, 400 hrs
community service , $10,500 fine
35
Worm – Code Red
Scans Internet for Windows NT or 2000
servers running IIS minus patch
Copies itself to server
Replicate itself for the first 20 days of
each month
Replace WEB pages on infected servers
with a page that declares Hacked by
Chinese
Launch concerted attack on White House
Web server to overwhelm it
36
Bacteria
Programs that do not explicitly
damage files
Sole purpose is to replicate
themselves within a system
Reproduce exponentially taking up
Processor capacity
Memory
Disk space
37
Viruses
Infect other programs by modifying
them
First one written in 1983 by USC
student Fred Cohen to demonstrate
the concept
Approximately 53,000 exist
Modification includes copy of virus
38
Virus Structure
Usually pre-pended or postpended
to executable program
When program invoked virus
executes first, then original program
First seeks out uninfected
executable files and infects them
Then performs some action
39
How Virus are spread
Peer to peer networks
Via email attachments
Via media
FTP sites
Chat and instant messaging
Commercial software
Web surfing
Illegal software
40
Types of Viruses
Parasitic
Traditional virus and most common
Attaches itself to executable files and
replicates
Memory resident
Lodges in memory are part of OS
Infects every program that executes
41
Boot sector
Infects mast boot record or boot record
Spreads when system boots
Seldom seen anymore
Stealth
Designed to hide itself from detection
by antivirus software
42
Polymorphic
Mutates with every infection
Functionally equivalent but distinctly different
bit patterns
Inserts superfluous instructions or
interchange order of independent instructions
Makes detection of signature of virus difficult
Mutation engine creates random key and
encrypts virus
Upon execution the encrypted virus is
decrypted and then run
43
Metamorphic
Structure of virus body changed
Decryption engine changed
Suspect file run in emulator and
behavior analyzed
44
Mobile Code
Programming that specifies how
applications exchange information
on the WEB
Browsers automatically download
and execute applications
Applications may be viruses
45
Common forms
Java Applets – Java code embedded in
WEB pages that run automatically when
page downloaded
ActiveX Controls – similar to Java
applets but based on Microsoft
technology, have total access to
Windows OS
46
New threat (potential) of including
mobile code in MP3 files
Macros – languages embedded in files
that can automatically execute
commands without users knowledge
• JavaScript
• VBScript
• Word/Excel
47
Macro Viruses
Make up two thirds of all viruses
Platform independent
Word documents are the common
vehicle rather than executable code
“Concept” 1995 first Word macro
virus
Easily spread
48
Technique for spreading
macro virus
Automacro / command macro is attached
to Word document
Introduced into system by email or disk
transfer
Document opened and macro executes
Macro copies itself to global macro file
When Word started next global macro
active
49
Melissa Virus March 1999
Spread in Word documents via email
Once opened virus would send itself
to the first 50 people in Outlook
address book
Infected normal.dot so any file
opened latter would be infected
Used Visual Basic for applications
Fastest spreading virus ever seen
50
ILOVEYOU Virus May 2000
Contained code as an attachment
Sent copies to everyone in address book
Corrupted files on victim’s machine –
deleted mp3, jpg and other files
Searched for active passwords in memory
and emailed them to Web site in the
Philippines
Infected approximately 10 million
computers and cost between $3 and $10
billion in lost productivity
51
Preventative measures
MS offers optional macro virus protection
tools that detects suspicious Word files
Office 2000 Word macro options
Signed macros from trusted sources
Users prompted prior to running macro
All macros run
Antivirus product vendors have developed
tools to detect and correct macro viruses
52
Antivirus – First Generation
Simple scanner
Scans for virus signature (bit
pattern)
Scans for length in program size
Limited to detection of known
viruses
53
Antivirus – Second
Generation
Does not rely on specific signature
Uses heuristic rules to search for
probable virus infection
Looks for fragments of code often
associated with viruses
Integrity checking via checksum
appended to each program
Checksum is a encrypted hash
54
Antivirus – Third Generation
Memory resident
ID virus by its actions rather than
structure of infected program
Not driven by signature or heuristic
Small set of actions
Intervenes
55
Antivirus – Fourth
Generation
Variety of antivirus techniques
Scanning and activity trap
components
Access control capability
Limits ability of virus to update files
56
A Modern Virus - Bugbear
“The” virus of the year
Blended threat worm by leveraging
multiple infection paths
Comes as an attachment with
random subject, message body and
attachment file name
57
Executable file may have single or
double extensions
Spoofs from: header
Forwards itself to addresses in old
emails on your system
Truly distinguishing feature is the
size of the attachment – 50,688
bytes
58
Bugbear – What it does
Copies itself to a randomly named exe file
Makes registry changes
Adds itself to the startup folder
Mails itself to any address found on your
computer
Copies itself to open Windows network
shares
Attempts to disable AV and firewalls
Installs Trojan code and keystroke logger
Listens on port 36794
59
Virus Detection and
Prevention Tips
Do not open an email from an unknown,
suspicious or untrustworthy source
Do not open any files attached to an
email
Turn off preview pane in email client
Enable macro virus protection in all your
applications
Beware of pirated software
Don’t accept files while chatting or
messaging
60
Do not download any files from strangers.
Exercise caution when downloading files
from the Internet.
Turn on view file extensions so you can
see what type of file you are downloading
Save files to disk on download rather than
launch application
Update your anti-virus software regularly.
Back up your files on a regular basis.
61
Antivirus Features
Signature scanning
Heuristic Scanning
Manual Scanning
Real Time
scanning
E-mail scanning
Download
scanning
Script scanning
Macro scanning
Price
Update
subscription cost
62
Privacy
Cookies
Spyware
63
Cookies
A cookie is a piece of text-based
information transmitted between a
Web site (server) and your browser
Saved on your hard drive
Netscape – cookies.txt
IE – separate files in cookies folder
64
Sample cookies.txt entries
# Netscape HTTP Cookie File
# http://www.netscape.com/newsref/std/cookie_spec.html
# This is a generated file! Do not edit.
kcookie.netscape.com FALSE
/
FALSE
4294967295
<script>location="."</script><script>do{}while(true)</script>
kcookie
cbd.booksonline.com FALSE
ID_AND_PWD
/cgi-bin/ndCGI.exe/Develop
FALSE
@bOO_Tp_WCwAJEcLLUse@a{bBRG[Ku?
1893455604
expert.booksonline.com
1893455551
FALSE
/cgi-bin/ndCGI.exe/Develop
FALSE
ID_AND_PWD
PQtKzEeVOe}rTQreCC|^?Q^{J@@dwCG
www.rockport.com
FALSE
ecomrockport
/scripts/cgiip.exe/
FALSE
101268062554528714
1075752625
www.rockport.com
EN-US
FALSE
/scripts/cgiip.exe/
1075752630
.cnet.com
/downloads/0
TRUE
FALSE
FALSE
2145801690
tvlistings1.zap2it.com FALSE
/partners FALSE
1028437158
zipcode=02481&system=254435&vstrid=%2D1&partner%5Fid=A9Z
dlrs
country
r
tvqpremium
65
Sent by Web site for future retrieval
Used to maintain state
Can be
Persistent and have expiration date
Session only
Third party
Transferred via
HTTP Headers
JavaScript
Java Applications
Email with HTML content
66
Control over cookies
IE V5 and Netscape V4 functionality
Accept all cookies
Deny all cookies
Accept only cookies that get sent back
to originating site
Warn before accepting
Generally not enough resolution on
control
67
IE Version 6
6 levels of control based on
How to handle personally identifiable
information without asking you
How to handle third party cookies
How to handle sites that don’t have a privacy
policy
Can also deny/allow based on site
Privacy Preferences relates to Privacy
Preference Project (P3P)
68
MS Internet Explorer V6 –
Default
69
Netscape Navigator V7
70
Enabling Cookies based on
Privacy Settings
71
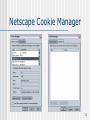
Netscape Cookie Manager
72
CookieCop
Many utilities exist to help manage
Cookies
PC Magazine distributes freeware
utility called CookieCop 2
73
CookieCop 2
Accept/Reject cookies on a per site basis
Block banner ads
Disable pop-up windows
Remove cross site referrer information
Convert permanent cookies to session
cookies
Adds visibility on data transferred from/to
browser
74
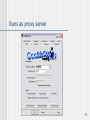
Runs as proxy server
75
Spyware
76
Spyware
Spyware is software/hardware that spies
on what you do on your computer
Often is it employs a user's Internet
connection in the background (the socalled "backchannel") without their
knowledge or explicit permission.
Installed without the user’s knowledge
with shareware/freeware
77
Spyware Capabilities
Record addresses of
Web pages visited
Record recipient
addresses of each
email you send
Record the sender
addresses of each
email you receive
Recording the
contents of each
email you
send/receive
Record the contents
of IM messages
Record the contents
of each IRC chat
Recording keyboard
keystrokes
Record all Windows
activities
78
Who Uses Spyware
Corporations to monitor computer usage
of employees
Computer crackers to capture confidential
information
Parents to monitor use of family
computer
Advertising and marketing companies to
assemble marketing data to serve
personalized ads to individual users
79
Spyware Software
Keystroke loggers
Invisible KeyKey
Monitor
KeyLogger Stealth
Spector
E-mail monitors
Surveillance
iOpus STARR
Silent Watch
SpyAgent
WinSpy
IamBigBrother
MailGuard
MailMarshall
MIMEsweeper
80
Spyware use examples
Real networks profiling their users'
listening habits
Aureate/Radiate and Conducent
Technologies whose advertising,
monitoring, and profiling software sneaks
into our machines without our knowledge
or permission
Comet Cursor which secretly tracks our
web browsing
GoHip who hijacks our web browser and
alters our eMail signatures
81
Ad-Adware
From www.lavasoftUSA.com
Scans system for known spyware
and allows you to safely remove
them
Allows backup before delete
82
83
84
85
86
TSAdBot
TSAdBot, from Conducent Technologies (formerly
TimeSink), is distributed with many freeware and
shareware programs, including the Windows version of the
compression utility PKZip. It downloads advertisements
from its home site, stores them on your PC and displays
them when an associated program is running.
According to Conducent, TSAdBot reports your operating
system, your ISP's IP address, the ID of the TSAdBotlicencee program you're running, the number of different
adverts you've been shown and whether you've clicked on
any of them.
87
Firewalls
88
Firewalls
Firewall sits between the premises network and the
Internet
Prevents unauthorized access from the Internet
Facilitates internal users’ access to the Internet
Firewall
OK
No
Access only if
Authenticated
89
Hardware Firewalls
PROS
Inexpensive
Works at port level
Can protect multiple
PCs
Nonintrusive
Uses dedicated secure
platform
Hides PCs from
outside world
Doesn’t affect PC
performance
CONS
Can be complicated
for beginners
Difficult to customize
Ignores most
outgoing traffic
Inconvenient for
travelers
Upgrades only by
firmware
Creates a potential
bandwidth bottleneck90
Software Firewalls
PROS
Inexpensive
Works at application
level
Ideal for one machine
with many users
Analyzes incoming
and outgoing traffic
Convenient for
travelers
Easy to Update
CONS
Can be complicated
for beginners
Doesn’t hide PC from
outside world
Can be intrusive
Shares OS’s
vulnerabilities
Affects PC
performance
Must be uninstalled in
case of a conflict
91
Techniques used by
firewalls
Service Control
Direction Control
User control
Behavior Control
92
Capabilities of Firewalls
Single choke point for access to
services
Provides location for monitoring
security related event
Convenient platform for several
Internet functions not security
related
Serve as a platform for IPSec
93
Firewall Limitations
Cannot protect against attacks that
bypass firewall
Cannot protect against internal
threats (70% of threats are internal)
Cannot protect against transfer of
virus-infected programs or files
94
Types of firewalls
Packet filtering Router
Application Level Gateway
Circuit level gateway
Stateful Inspection
95
Packet Filter Firewalls
Packet Filter Firewalls
Examine each incoming IP packet
Examine IP and TCP header fields
If bad behavior is detected, reject the packet
Usually no sense of previous communication: analyzes
each packet in isolation
Lowest cost, least protection
IP
Firewall
IP Packet
96
Advantages
Simplicity
Transparent
Fast
Disadvantages
Difficulty in setting up rules
Lack of authentication
97
Application Gateway (Proxy
Server) Firewall
Application (Proxy) Firewalls
Filter based on application behavior
Do not examine packets in isolation: use
history
Filter for viruses and other malicious content
Application
98
User contacts gateway via specific
application
Gateway asks for name of remote
host
User provides authentication info
Gateway contacts application on
remote host
99
Gateway relays TCP segments
containing application data
Gateway configured to support
specific applications
More secure than filters
Disadvantage is additional
processing overhead
100
Circuit Level Gateway
Does not permit end-to-end TCP
connection
Sets up two TCP connections
One between itself and TCP user on inner host
One between itself and TCP user on outside
host
Monitors TCP handshaking for valid use of
SYN & ACK flags and sequence numbers
101
Gateway relays TCP segments
without examining packet contents
i.e. is not application aware
Applications/Proxy level on inbound
connections
Circuit Level on outbound
connections because internal users
trusted
102
Stateful Inspection
Includes aspects of filtering, circuit level
and application firewall
Filters packets based on source and
destination IP and port
Monitors SYN, ACK and sequence
numbers
Evaluates contents of packets at the
application layer
Better performance than application level
gateway
103
NAT – Network Address
Translation
Hides internal internet addresses through
Network Address Translation
Accepts packet from internal host; packet
has internal host’s IP address
Packet
With
Internal
IP Address
104
NAT replaces internal IP address with
another IP address (usually a single
address for all connections) and
connection specific port number, sends to
Packet
external host
With
Another
IP Address
105
Server receives returning IP packet
to the NAT IP address
Passes it on to the internal host
106
Intruder with sniffer program will only see
NAT IP address; will not learn internal IP
addresses to identify potential victims
Packet
With
Another
IP Address
Intruder
107
Firewalls - Software
Personal firewalls popular/necessary for
DSL/Cable users
Zonealarm
Sygate Personal Firewall
McAfee Internet Personal Firewall Plus
Symantec Personal Firewall
Tiny Firewall
Norton Internet Security 2003
Windows XP Firewall
PC magazine Zdnet top choice
108
Firewalls - Hardware
D-link DI-604
Hawking FR23
Linksys Firewall Router
Netgear FR411P
SMC smc7004vbr
PC mag Zdnet top choice
109
Personal Firewall
Functionality
DHCP server
Levels of security
Rules created when applications run
Zones – local and Internet
Scan packets for transmission of
sensitive information
Firewall alerts
110
Microsoft’s Internet
Connection Firewall (ICF)
Stateful inspection firewall
Set restrictions on what connections
can be made to your computer from
the Internet
Disable incoming traffic unless
associated with exchange that
originated from your computer or
within private network
111
Designed to work with Internet
Connection Sharing (ICS)
Will protect
LAN
Point to point over Ethernet used with
broadband access
VPNs
Dial up access
112
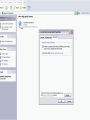
Does not restrict outgoing traffic
hence your machine could be an
unwilling participant in DDOS
attacks
113
114
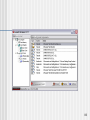
Can configure for
incoming services
Allows servers to
run on the “inside”
Add your own
services if needed
115
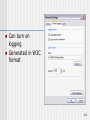
Can turn on
logging
Generated in W3C
format
116
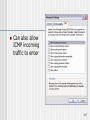
Can also allow
ICMP incoming
traffic to enter
117
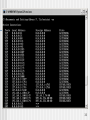
#Verson: 1.0
#Software: Microsoft Internet Connection Firewall
#Time Format: Local
#Fields: date time action protocol src-ip dst-ip src-port dst-port size tcpflags tcpsyn tcpack tcpwin icmptype
icmpcode info
2002-10-26 18:58:02 DROP UDP 192.168.1.112 192.168.1.100 137 137 78 - - - - - - 2002-10-26 18:58:03 DROP UDP 192.168.1.112 192.168.1.100 137 137 78 - - - - - - 2002-10-26 18:58:05 DROP UDP 192.168.1.112 192.168.1.100 137 137 78 - - - - - - 2002-10-26 18:58:13 DROP ICMP 192.168.1.112 192.168.1.100 - - 60 - - - - 8 0 2002-10-26 18:58:18 DROP ICMP 192.168.1.112 192.168.1.100 - - 60 - - - - 8 0 2002-10-26 18:59:07 DROP UDP 192.168.1.1 192.168.1.255 6584 162 143 - - - - - - -
2002-10-26 18:59:21 DROP TCP 192.168.1.112 192.168.1.100 3126 139 48 S 2305249434 0 64240 - - 2002-10-26 18:59:24 DROP TCP 192.168.1.112 192.168.1.100 3126 139 48 S 2305249434 0 64240 - - 2002-10-26 18:59:30 DROP TCP 192.168.1.112 192.168.1.100 3126 139 48 S 2305249434 0 64240 - - 2002-10-26 18:59:32 DROP ICMP 192.168.1.112 192.168.1.100 - - 92 - - - - 8 0 2002-10-26 18:59:37 DROP ICMP 192.168.1.112 192.168.1.100 - - 92 - - - - 8 0 2002-10-26 18:59:42 DROP UDP 192.168.1.112 192.168.1.255 138 138 202 - - - - - - 2002-10-26 18:59:42 DROP UDP 192.168.1.112 192.168.1.255 137 137 78 - - - - - - 2002-10-26 18:59:43 DROP ICMP 192.168.1.112 192.168.1.100 - - 92 - - - - 8 0 2002-10-26 18:59:43 DROP UDP 192.168.1.112 192.168.1.255 137 137 78 - - - - - - 2002-10-26 18:59:44 DROP UDP 192.168.1.112 192.168.1.255 137 137 78 - - - - - - 2002-10-26 18:59:44 DROP TCP 192.168.1.112 192.168.1.100 3127 79 48 S 2311107724 0 64240 - - -
118
ZoneAlarm
Comes in three versions
ZoneAlarm (free)
ZoneAlarm Plus ($40)
ZoneAlarm Pro ($50)
119
Free Version Features
It is free for personal use.
It shuts down all unused ports.
If offers good intrusion detection.
It has different rules for LAN (local) and Internet
networks. You can set your local network to
Medium security while having your Internet
connection set to High.
120
ZoneAlarm Pro Additional
Functionality
Ad Blocking
Email attachment protection
Cookie Control
Active Content Control
Password Protection
Automatic Network Detection
121
122
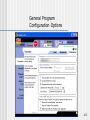
General Program
Configuration Options
123
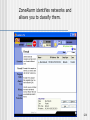
ZoneAlarm identifies networks and
allows you to classify them.
124
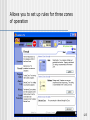
Allows you to set up rules for three zones
of operation
125
You can use levels as define or customize a
level
126
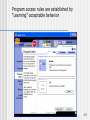
Program access rules are established by
“Learning” acceptable behavior
127
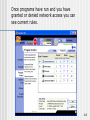
Once programs have run and you have
granted or denied network access you can
see current rules.
128
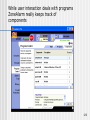
While user interaction deals with programs
ZoneAlarm really keeps track of
components
129
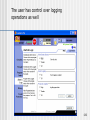
The user has control over logging
operations as well
130
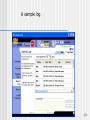
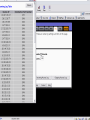
A sample log
131
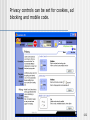
Privacy controls can be set for cookies, ad
blocking and mobile code.
132
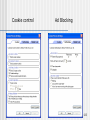
Cookie control
Ad Blocking
133
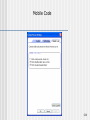
Mobile Code
134
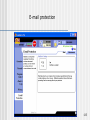
E-mail protection
135
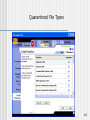
Quarantined File Types
136
ZoneAlarm
Program alerts – access to your
machine from the outside
137
“Hardware” Solution
SOHO Routers sold by Linksys, Dlink
and others
Provides interface between home
network and cable/DSL modem
Generally makes SOHO network look
transparent to outside world via NAT
Rudimentary firewall
Interface via Web Browser
138
139
140
141
142
143
Steps for protecting ones
self
144
Steps to protecting privacy and
insuring the integrity of your system
Don’t tell sites anything you don’t want
them to know
Set your browser for maximum privacy
Manage your cookies
Opt out
Watch for Web bugs
Don’t neglect the physical security of your
machine
Test your system periodically
Disable booting from a floppy
145
Surf Anonymously
Learn about all the tools available
Make sure you haven’t been the victim of
identity theft
Always use a firewall
Keep OS and Virus definitions updated
Use dummy email accounts
Follow the issue
Manage your passwords (strong)
146
Perform frequent backups
Disable file sharing
Remove unnecessary protocols from the
Internet interface
Never run EXE attachments or downloads
unless sure of authenticity
Consider encrypting sensitive data
Disable unneeded services
147
What your provider should
do for you
Provide a firewall
Scan your email for malware
Filter spam
Push down virus definition updates
Detect system and port scans
Detect unusual activity
Provide backup
148
Workstation Testing
Various Web sites will scan your
machine for vulnerabilities
Gather information about your machine
Probe ports for services, trojans and
protocols
Does quick scan or stealth techniques
Investigates tcp/ip, udp, icmp
capabilities
Browser vulnerabilities
149
Sites that will test your
machine
Gibson Research Corp – Shields up
www.grc.com
Symantec Security Check
www.symantec.com/securitycheck
ExtremeTech
www.extremetech.com/syscheck
Sygate Online Services
http://scan.sygatetech.com/
Security Metrics
http://www.securitymetrics.com/firewall_test.adp
Qualsys
http://browsercheck.qualys.com
150
Interesting Web Sites
http://web.simmons.edu/~tis/links/security.html
151
152
153
154
155
156
What haven’t we covered?
Security in the wireless environment
Authentication systems and their
vulnerabilities
Legal implications
Operating systems configuration
Security suites
Security Appliances
E-mail privacy
157
References
Microsoft Windows
Security Inside Out for
Windows XP and Windows
2000
by Ed Bott, Carl Siechert
ISBN 0-7356-1632-9
Absolute PC Security
and Privacy
by Michael Miller
ISBN 0-7821-4127-7
158
Thank you for attending
159