* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Its_time_to_go_hunting_-_IOC_vs_IOA_
Mobile device forensics wikipedia , lookup
Information privacy law wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Unix security wikipedia , lookup
Computer security wikipedia , lookup
Cyberwarfare wikipedia , lookup
Cyberattack wikipedia , lookup
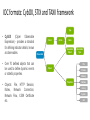
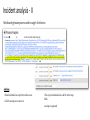
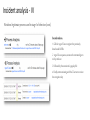
It’s time to go hunting! Indicators of Compromise vs. Indicators of Attack Octavian Savin Mihai Capraru About Us SecureWorks - global provider of intelligence-driven information security solutions, which enable organizations to fortify their cyber defenses to prevent security breaches, detect malicious activity in real time, prioritize and respond rapidly to security breaches and predict emerging threats. Mihai Capraru • Security Systems Sr. Analyst at SecureWorks • 5 years of experience in computer forensics and cybercrime investigations Octavian Savin • Security Systems Sr. Analyst at SecureWorks • 4 years IT experience, 2 years security experience Agenda The Cyber Kill Chain About Indicators of Compromise About Indicators of Attack Threat Hunting Case study: Unknown malware detection • The Cyber Kill Chain • Phases 1. Reconnaissance 2. Development 3. Weaponization 4. Delivery 5. Exploitation 6. Installation 7. Command and Control 8. Action on Objective Indicators of compromise What are IOCs Sources for IOCs IOCs formats What are IOCs? Analyze Data Pieces of forensic data found in log entries or system files. Made off virus signatures, IP addresses, URLs or domains, hash values, registry keys, filenames, HTTP user agents. Created through a multi-step process driven by analyst experience and knowledge. Collect Data Tet Create IOCs Identify Affected Systems Deploy IOCs IOC sources • Included in threat intelligence feeds. • Only released to paying customers • Rather expensive. Commercial and industry sources • Require a bit of detective work and a good knowledge of the internal network • Potential to produce very interesting results. Internally developed IOCs Free IOC sources • Specific IOC distribution sites • IOC Bucket IOC formats: OpenIOC • Open source framework developed by Mandiant • Utilizes XML to describe threat information • Easily transformed to a format used by IT monitoring tools (Yara and Snort) • Free tools for managing them: IOC Editor and IOC-EDT IOC formats: CybOX, STIX and TAXII framework Type • CybOX (Cyber Observable Expression) - provides a standard for defining indicator details, known as observables. • Over 70 defined objects that can be used to define dynamic events or stateful properties. • Objects: File, HTTP Session, Mutex, Network Connection, Network Flow, X.509 Certificate etc. Event Action Name Associated Object Observable Association Type File Object Process Memory Properties Address Library System GUI IOC formats: CybOX, STIX and TAXII framework (cont.) • STIX (Structured Threat Information Expression) - standardized, structured language to represent cyber threat information. • Supports the following data elements: Observables Incidents Adversary tactics, techniques and procedures (attack patterns, exploits, tools, infrastructure) Exploit targets Cyber attack campaigns Cyber threat actors IOC formats: CybOX, STIX and TAXII framework (cont.) • TAXII (Trusted Automated eXchange of Indicator Information) - set of specifications for exchanging cyber threat information. • Three sharing models: Consumer & Producer Peer A Subscriber Subscriber Producer Peer B Peer E Consumer Hub Hub and Spoke Consumer & Producer Subscriber Source Peer C Subscriber Peer D Source/Subscriber Peer-to-Peer • In 2015, these standards have been transitioned to the Organization for the Advancement of Structured Information Standards (OASIS), which has the role to develop them and promote their adoption, enabling cyber threat intelligence to be analyzed and shared among partners and communities worldwide. IOC formats: MAEC MAEC (Malware Attribute Enumeration and Characterization) is a standardized language developed by MITRE to describe information about malware based upon attributes such as behaviors, artifacts, and attack patterns. • The MAEC Bundle – capture and share data obtained from the analysis of a single malware instance. • The MAEC Package – capture and share data for one or more Malware Subjects (usually related). A Malware Subject contains details of a particular malware instance and any other data derived from analysis and metadata. • The MAEC Container – enables a user to share any collection of MAEC characterized data, including one or more Packages. MAEC Container (Tier 3) MAEC Package (Tier 2) MAEC Bundle (Tier 1) MAEC Default Vocabularies IOC formats: MAEC (cont.) • Cuckoo Sandbox can generate malware analysis results in MAEC format. • CybOX is supported in the latest version of MAEC. • Benefits: standard representation – different tools can handle the same malware data without data conversion. improved data exchange flow - malware analyses can be exchanged in a common, well known and standardized language. Indicators of attack What are IOAs Assemble IOAs Benefits of using IOAs IOC vs IOA What are IOAs? Series of actions that an adversary must conduct in order to succeed. All actions done by the attacker in order to prepare his attacks. All the “signs” left by the attacker in earlier stages of the attack. Indicators of Attack Assemble IOAs Users activity Vulnerability info Suspicious attempts Network activity Suspicious user behavior Servers/Host activity Application activity Security Devices Analysis Information Gathering (scans) Database activity Other … Honeypot Other… Earlier stages of the attack Threat Hunting Alert Benefits of using IOAs Accuracy of detection and response • Provide indicators of action taken during every stage of the attack. Early detection • Help develop a strong game plan for a company’s defense. Faster response time IOAs Damage reduction • Enable to understand the internal environment and pinpoint probable targets for threat actors Diminished business impact Ability to see attacks in context IOC vs IOA • IoC’s are reactive indicators while IoA’s are proactive indicators • IoC’s can be used after a point in time, while IoA’s are used in real time • IoC’s are known, universal bad news, while IoA’s only become bad based on what they mean to you and the situation IoCs Malware Signature Exploits IP Addresses Vulnerabilities IoAs Code executions User behavior Malware behavior Persistence Stealth Threat hunting What is threat hunting? Mindset needed in threat hunting What is threat hunting? “The process of proactively and iteratively searching through networks to detect and isolate advanced threats that evade existing security solutions, as early as possible in the cyber kill chain” Approaches Frequency driven by Objective driven by Intelligence driven by Anomaly Ad-hoc Project based Continuous Mindset needed in threat hunting • “If you know your enemies and know yourself, you will not be imperiled in a hundred battles” (Sun Tzu) • Three major questions we need to answer about attackers: What is their avenue of approach? What are they looking for? How are they going to get it? • A formal hunting process has four stages: Hypothesis generation Investigation Pattern and TTP discovery Automated analytics The Threat Hunting Reference Model Part 2: The Hunting Loop (28 Oct 2015). Retrieved from ‘http://blog.sqrrl.com/the-threat-hunting-reference-model-part-2-the-hunting-loop’ Case study Unknown malware detection Case Study – unknown malware • • Process names: cmd.exe; wscript.exe; regsvr32.exe; powershell.exe • • Host abnormal behavior Windows legitimate processes used with suspicious cmdline Abnormal process tree Connections created by unusual processes Suspicious command lines run by the processes • • • Phase of the attack Benefits IoA used Parent name: iexplore.exe • • • • • Endpoint Detection and Response Full host visibility Cross network searches Initial stage of the attack Attacker didn’t meet the scope Earlier exploitation phase (not al malware components were installed/downloaded) Tools • • The files weren’t encrypted The host can be sanitized not reimaged The damage wasn’t produced The incident was contained Incident analysis - I Process tree Internet explorer child processes - cmd.exe spawns - wscript.exe spawns - cmd.exe spawns - regsvr32.exe Incident analysis - II Windows legitimate process used in stage I of infection cmd.exe 1. Downloads malicious script from malicious site 2. Calls for wscript.exe to execute it 3. The script is downloaded as a .dat file, in the temp folder 4. wscript.exe spawned Incident analysis - III Windows legitimate process used in stage I of infection (cont.) wscript.exe 1. Executes the downloaded .dat file 2. Creates a .dll file 3. Deletes the previously used .dat file 4. Spawns cmd.exe Incident analysis - IV Windows legitimate process used in stage I of infection (cont.) Second cmd.exe 1. Calls for regsvr32.exe to register the previously downloaded .dll file 2. regsvr32.exe spawns, executes the command given to it by cmd.exe 3. Followed by the creation of a ppp.key file 4. Finally communicating with the C2 server to receive the encryption key Root cause identification 1. The user searched something on Google 2. Connected to the website 3. Redirected to the malicious website 4. Gets infected Recommendations for ransomware mitigation (based on previous findings) Block process run in temp folder Block identified malicious IPs and domains Implement adware block solution The end Thank you! Questions?