* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Important Concepts.
Next-Generation Secure Computing Base wikipedia , lookup
Airport security wikipedia , lookup
Cyberwarfare wikipedia , lookup
Cryptography wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Deep packet inspection wikipedia , lookup
Unix security wikipedia , lookup
Information security wikipedia , lookup
Distributed firewall wikipedia , lookup
Cyberattack wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Wireless security wikipedia , lookup
Social engineering (security) wikipedia , lookup
International cybercrime wikipedia , lookup
Security-focused operating system wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Mobile security wikipedia , lookup
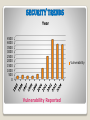
UNIT 1 INTRODUCTION TO NETWORK SECURITY Prof.Ms.S.G.Pundkar PRMIT&R Contents Computer Security Concepts 1.1 The OSI Security Architecture 1.2 Security Attacks 1.3 Security Services 1.4 Security Mechanisms 1.5 A Model for Network Security : Symmetric Encryption and Message 2.1 Symmetric Encryption Principles 2.2 Symmetric Block Encryption Algorithms 2.3 Random and Pseudorandom Numbers 2.4 Stream Ciphers and RC4 2.5 Cipher Block Modes of Operation Confidentiality Important Concepts. 1. What is Network Security ? • A specialized field in computer networking that involves securing a computer network infrastructure. • • Network security is handled by a network admin. Admin implements the security policy, network Software and Hardware needed to protect a network and the resources from unauthorized access • ensure that employees have adequate access to the network and resources to work. 2. What is Vulnerability ? In computer and network security, vulnerability refers to any weakness in the computer’s or network’s. 3. What is threat ? • Threat is a possible danger that might exploit a vulnerability to breach security and thus cause possible harm. • A threat can be either "intentional" (i.e., intelligent; e.g., an individual cracker or a criminal organization) or "accidental" (e.g., the possibility of a computer malfunctioning, or the possibility of a natural disaster such as an earthquake, a fire, or a tornado) or otherwise a circumstance, capability, action, or event • 4. What is Malware ? Malware (malicious software), is software used to disrupt computer operation. • It gather’s sensitive information, or gain access to private computer systems. • It can appear in the form of code, scripts, active content, and other software. • 'Malware' is a general term used to refer to a variety of forms of hostile or intrusive software. 5.What is Spyware ? Spyware is software that aids in gathering information about a person or organization without their knowledge. Spyware is software that sends information about your Web surfing habits to its Web site. Spyware is often installed without the user’s knowledge or explicit permission in combination with a free download. 7. Denial of Service (DoS) The denial of service prevents or inhibits the normal use or management of communications facilities. This attack may have a specific target; for example, an entity may suppress all messages directed to a particular destination (e.g., the security audit service). Another form of service denial is the disruption of an entire network—either by disabling the network or by overloading it with messages so as to degrade performance. 8. Key Logger A computer program or hardware device specialized to record your keystrokes. It can record anything that you type, including your passwords, emails, credit card number. They save the recorded keystrokes into a log file or send them to another machine. Most key-loggers can be detected by spyware removal software. 9. Packet Sniffing Packet sniffing is the act of capturing packets of data flowing across a computer network. Software or device used for this is called a packet sniffer. Packet sniffing in computer networks is like wire tapping in telephone network. Widely used by hackers to gather information illegally like passwords, IP addresses, protocols being used on the network and other information that will help the attacker to do their work. Packet sniffing also has legitimate uses for monitoring network performance or troubleshoot problems communications. with network 10. Phishing (Fishing) Phishing is committing fraud to get financial information without the user realizing it. Trying to trick somebody into providing bank or credit-card information. Usually done by sending a fraudulent e-mail purporting to be from a bank, Internet provider, etc. asking for verification of an account number or password. 11. Port Scan (Port Sniffing) A port is an endpoint of communication in an operation system. A port scan is a method used by hackers to determine what ports are open or in use on a system or network. Using tools a hacker can send data to TCP or UDP ports one at a time. Based on the response received the port scan utility can determine if that port is in use. Using this information the hacker can then focus their attack on the ports that are open and try to exploit any weaknesses to gain access Some Example of PORTS File Transfer Protocol (FTP)----20/21 Secure Shell (SSH)-------------22 Domain Name System (DNS)—53 Trivial File Transfer Protocol (TFTP)--69 Important Concepts. 12. Proxy Server A proxy server acts as a middleman between your internal and external networks. It serves the dual roles of speeding up access to the Internet as well as providing a layer of protection for the internal network. Speedup by caching pages that have been previously requested, rather than going to the web site again. When using a proxy server, external systems only see the IP address of the proxy server so the true identity of internal computers is hidden. Important Concepts. 13. Spoofing (E-mail) Email spoofing is the forgery of an email header so that the message appears to have originated from someone or somewhere other than the actual source Important Concepts. 14. Backdoor A backdoor is a secret or undocumented means of getting into a computer system. Many programs have backdoors placed by the programmer to allow them to gain access to troubleshoot or change the program. Some backdoors are placed by hackers once they gain access to allow themselves an easier way in next time or in case their original entrance is discovered. Important Concepts. 15. Browser Hijacker A Browser Hijacker is any program that changes some settings in your browser. Browser hijackers commonly redirect your "search" page to pass all searches to a certain pay-per-search site, change the default home page to the desired company page and often transmit URLs (websites) viewed toward the desired company server. Important Concepts. 16. Encryption : Encryption is the conversion of electronic data into another form, called cipher-text, which cannot be easily understood by anyone except authorized parties. Primary purpose of encryption is to protect the confidentiality of digital data stored on computer systems or transmitted via the Internet or other computer networks Important Concepts. 17. Decryption : The process of decoding data that has been encrypted into a secret format. Decryption requires a secret key or password. Decryption is the reverse process to Encryption. Frequently, the same Cipher is used for both Encryption and Decryption. While Encryption creates a Cipher-text from Plaintext, Decryption creates a Plaintext from a Cipher-text. a Important Concepts. 18. What is Digital Signature ? Is an electronic signature that can be used to authenticate the identity of the sender of a message or the signer of a document, to ensure that the original content of the message or document that has been sent is unchanged. Digital signatures are easily transportable, cannot be imitated by someone else, and can be automatically time-stamped. Important Concepts. Types of Malicious Code Virus Attaches itself to program & propagate copies of itself to other program. (Vital Information Resources Under Seize ) Trojan Horse Contain Unexpected, additionally functionality (remember it doesn’t replicate like virus). It is a program designed to cut the security of a computer system while performing some function. Logic Bomb Triggers actions when condition occurs. Time Bomb Triggers actions, when specified time access. Trapdoor Allows unauthorized access to functionality. Worm Propagates copies of itself through Network. Rabbit Replicate itself without limit to exhaust resources. A rabbit (also known as computer bacteria) in computing is any computer program . PROFESSIONAL ELECTIVE - II (IV) NETWORK SECURITY Unit I : Introduction: Security Trends, The OSI Security Architecture. Security Attacks, Security Services, Security Mechanisms, A Model for Internetwork Security, Internet Standards and the Internet Society. Symmetric Encryption and Message Confidentiality : Symmetric Encryption Principles, Symmetric Block Encryption Algorithms, stream Ciphers and RC4, Cipher Block Modes of Operation, Location of Encryption Devices, Key Distribution. (08 Hrs) Unit II: Public-Key Authentication: Cryptography and Message Approaches to Message Authentication, Secure Hash Functions and HMAC, Public Key Cryptography Principles, Public Key Cryptography Algorithms, Digital Signatures, Key Management. Unit III: Authentication Applications: (08 Hrs) Kerberos, X.509 Authentication Service, public-Key Infrastructure, Electronic Mail Security: Pretty Good Privacy ( PGP), S/MIME, (08 Hrs) Unit IV: IP Security: IP Security Overview, IP Security Architecture, Authentication Header, Encapsulating Security Payload, Combining Security Associations, Key Management, Web Security: Web Security Considerations, secure socket Layer (SSL) and Transport Layer Security (TLS), Secure Electronic Transaction (SET). (08 Hrs) Unit V : Network Management Security: Basic Concepts of SNMP, SNMPv1 Community Facility, SNMPv3, Intruders: Intruders, Intrusion Detection, Password Management (08 Hrs) Unit VI: Malicious Software: Viruses and Related Threats, Virus Countermeasures, Distributed Denial of Service Attacks, Firewalls: Firewall Design Principles, Trusted Systems, Common Criteria for Information Technology Security of Evolution. (08 Hrs) TEXT BOOK: William Stallings: "Network Security Essentials Applications and Standards" Pearson Education, Thirds/Fourth Edition. REFERENCE BOOKS: 1. Atul Kahate: " Cryprography and Network Security" Mc Graw Hill .0 2. Forouzan and Mudhopahyay: ""Cryptography and Network Security" Mc Graw Hill. 3. Matt Bishop: " Computer Security: Art & Science" Pearson Education. 4. Brijendra Singh: " Network Security & Management " PHI. 1.1 Security Trends Internet Architecture Board issued report in 1994 named “Security in the Internet Architecture”. Report Provide general consensus that Internet needs more and better security. Concentrating need to secure Network Infrastructure from unauthorized access. Network traffic Security using proper authentication and encryption methods. Security Trends Fig shows vulnerabilities reported to CERT (Computer Emergency Response Team) over 10 year period. It includes security weakness in OS of attached Computers (Windows, Linux) etc, Vulnerability in Routers and other Network devices. Security Trends Year 4500 4000 3500 3000 2500 2000 1500 1000 500 0 Vulnerability Vulnerability Reported Security Trends Fig shows the number of security incidents reported to CERT. Includes DOS attacks, IP Spoofing, Packet Sniffing. Over the time the attacks & Internet attached system grows dramatically but the skill and knowledge required to defend them has declined. Attacks becomes more automated. Leads to greater amount of damage. Increase in attacks is due to increase in use of Internet, applications, Internet etc. Therefore wide range of technology and tools is needed to deal with this attacks. Security Trends CERT Statistics : No Of Incidents Reported 160000 140000 120000 100000 80000 60000 40000 20000 0 Incidents Reported. 1.2 OSI Security Architecture Note terms ◦ Threat – a potential for violation of security, Threat is , a possible danger that might exploit vulnerability. ◦ Attack – an assault on system security, It is an intelligent attack i.e. a deliberate attempt to avoid security services. ◦ The Open Systems Interconnection model (OSI model) is a conceptual model that characterizes and standardizes the communication function of a telecommunication or computing system without regard to their underlying internal structure and technology. ◦ The OSI model describes how information or data makes its way from application programmes (such as spreadsheets) through a network medium (such as wire) to another application programme located on another network. ◦ The OSI security architecture is useful to managers as a way of organizing the task of providing security. ◦ The OSI security architecture focuses on security attacks, mechanisms, and services OSI Security Architecture ITU-T=International Telecommunication Union/ Sector 1.3 Security Attacks Passive Attacks Here the goal of the opponent is to obtain information that is being transmitted. Two types of passive attacks 1. Release of message contents 2. Traffic Analysis Passive attacks are difficult to detect coz they do not involve any alteration of data. Receiver or Sender are unaware of third party has read the message or observed the traffic pattern can be prevented, rather than detected; use of encryption Passive Attacks : 1. Release Of Message Contents Release of message contents : A telephone conversation, email, and a transferred file may contain sensitive data. Passive Attacks 2: •In this attack the eavesdropper analyzes the traffic, determine the location, identify communicating hosts, observes the frequency and length of message being exchanged. •All incoming and out going traffic of network is analysed but not altered. Eavesdropping is secretly listening to the private conversation of others without their consent Active Attacks Active attacks involves some modification of data or creation of false stream . 1. It is subdivided into four categories: Masquerade 2. Replay 3. Modification of message 4. Denial of service. Security Attacks Security Attacks Interruption: This is an attack on availability Interception: This is an attack on confidentiality Modification: This is an attack on integrity Fabrication: This is an attack on authenticity Active Attacks : 1.Masquerade •A masquerade attack is an attack that uses a fake identity, such as a network identity, to gain unauthorized access to personal computer information through legitimate access identification. •If an authorization process is not fully protected, it can become extremely vulnerable to a masquerade attack. •e.g. Authentication sequences can be captured and replayed after a valid authentication sequence has taken place. Active Attacks : 2. Replay Replay involves the passive capture of data unit and its subsequent retransmission to produce an unauthorized effect A replay attack (also known as playback attack) is a form of network attack in which a valid data transmission is maliciously repeated or delayed. Active Attacks : 3. Modification of Message Modification of messages simply means that some portion of a message is altered, or that messages are delayed or reordered, to produce an unauthorized effect . For example, a message meaning “Allow John Smith to read confidential file accounts” is modified to mean “Allow Fred Brown to read confidential file accounts.” Active Attacks : 4. Denial of Service Denial of Service DOS prevents the normal use of communication facilities. It has an specific target: e.g. an entity may suppress all messages directed to a particular destination. Another type; disruption of an entire network by disabling the network or by overloading it with unwanted (flooding of messages) messages and degrades the performance. Active and Passive Attacks Active attacks has opposite characteristics of Passive attacks. Passive; difficult to detect, but measures are available to prevent their success. Active; difficult to prevent , for preventing its require physical protection of all communication facilities all times. It is good to detect them and to recover from disruption or delay caused by them. 1.4 Security Service Enhance security of data processing systems and information transfers of an organization. Intended to counter security attacks. Using one or more security mechanisms. Often replicates functions normally associated with physical documents which, for example, have signatures, dates; need protection from disclosure, tampering, or notarized or witnessed; be recorded or licensed destruction; be Security Service X.800: defines a security service “a service provided by a protocol layer of communicating open systems, which ensures adequate security of the systems or of data transfers” Clear view is mention in RFC2828. RFC 2828: definition “a processing or communication service provided by a system to give a specific kind of protection to system resources” Security service includes security policies and security mechanism Security Services (X.800) X.800 divides services into five categories and includes 14 specific services. 1. Authentication – It is concerned with assuring that a communication is authentic. Assurance that communicating entity is the one that is claimed to be. Peer entity authentication Data origin authentication. oThere are two kinds of authentication services: Peer Entity Authentication : Two entities are considered peer if they both implement the same protocol in different systems. e.g. Two TCP modules in two communication systems. Provided for proving identity of a peer entity in an association.. It is use at the time of establishment and during data transfer phase of connection. It will provide confidence that an entity is not performing a masquerade or unauthorized replay of previous connection. Security Services (X.800) Data Origin Authentication : Provides confirmation of the source of a data unit. It doesn’t provide protection against the duplication or modification of data unit. e.g. E-mail like apps in which there is no prior interactions between the communicating entities. 2. Access Control - Prevention of the unauthorized use of a resource In network security, access control is the ability to limit and control the access to systems and applications via links. for this each entity trying to gain access must be first identified, or authenticated, so that access rights can be assigned. 3.Data Confidentiality – Protection of data from unauthorized disclosure. It is a protection of transmitted data from passive attacks. 4.Data Integrity – Assurance that data received are exactly as sent by an authorized entity. (i.e., contain no modification, insertion, deletion, or replay). Data integrity can be maintained through the use of various error checking methods and validation procedures. Data integrity and data security are related terms, each playing an important role in the successful achievement of the other. Data security refers to the protection of data against unauthorized access or corruption and is necessary to ensure data integrity. That said, data integrity is a desired result of data security, but the term data integrity refers only to the validity and accuracy of data rather than the act of protecting data. Data security, in other words, is one of several measures which can be employed to maintain data integrity, as unauthorized access to sensitive data can lead to corruption or modification of records and data loss. Whether it's a case of malicious intent or accidental compromise, data security plays an important role in maintaining data integrity. 5.Non-Repudiation Non-Repudiation prevents either sender or receiver from denying a transmitted message. Thus, when a message is sent, the receiver can prove that the alleged sender in fact sent the message. Similarly, when a message is received, the sender can prove that the alleged receiver in fact received the message. 1.5 Security Mechanism Q : Describe 8 Security mechanism ? [8 marks] ▪Mechanisms are divided into those that are implemented in specific protocol layer and those that are not specific to any protocol layer or security service. ▪ X.800 distinguishes between reversible encipherment mechanism and irreversible encipherment mechanism. Reversible encipherment mechanism consist of encryption algorithm that allows data encryption and decryption. Irreversible encipherment includes Hash algorithm and message authentication codes, which are used in digital signature and message authentication applications. Specific Security mechanism : This may be incorporated in appropriate protocol layer for providing some OSI security service. 1. En-cipher-ment: Converting one form of data to other using mathematical algorithms such that converted form is not readily intelligible. Transformation and subsequent recovery of data depends on an algorithm and zero or more encryption keys. 2. Digital Signature : • A Digital Signature is a mathematical scheme for demonstrating the authenticity of a digital message or document. A valid digital signature gives a recipient reason to believe that the message was created by a known sender, such that the sender cannot deny having sent the message (authentication and non-repudiation) and that the message was not altered in transit 3. Access Control : Access Control is any mechanism by which a system grants or revokes the right to access some data/resources, or perform some action. Access Control systems include: File permissions, such as create, read, edit or delete on a file server. Program permissions, such as the right to execute a program on an application server. Data rights, such as the right to retrieve or update information in a database. 4. Data Integrity : Data integrity refers to the overall Completeness, accuracy and consistency of data. A variety of mechanisms is used to assure the integrity of a data unit or stream of data unit. 5. Authentication Exchange : A mechanism intended to ensure the identity of an entity by means of information exchange. 6. Traffic Padding : It is an insertion of bits into gaps in a data stream for traffic analysis attempts. Other Security Mechanism : Mechanism that are not specific to any particular OSI security service or protocol layer. 1. Trusted Functionality : Any functionality providing or accessing security mechanisms should be trustworthy. May involve combination of software and hardware. 2. Security Label : Any resource (e.g. stored data, processing power, communications bandwidth) may have security label associated with it to indicate security sensitivity. Similarly labels may be associated with users. Labels may need to be securely bound to transferred data. 3. Event Detection : Includes detection of Security relevant events 4. Security Recovery : Includes mechanisms to handle requests to recover from security failures. May include immediate abort of operations, temporary invalidation of an entity, addition of entity to a blacklist. Security Mechanism Model for Network Security Consider a example for sending message between two parties. Logical information channel is established by defining routes from source and destination. E.g. TCP/IP communication protocol. Security aspects is needed to protect from opponent. Model for Network Security All techniques for security have two components. 1. A security-related transformation on information to be sent. E.g. encryption along with code to verify the identity of sender. 2. Some secret information shared by the two principals and, it is hoped, unknown to the opponent. An example is an encryption key used in the transformation to scramble the message before transmission and unscramble it on reception. Trusted third party is needed to achieve secure transmission. E.g. for distributing the secret information to two end points (principals), to solves disputes between them. Model for Network Security This general model consist of four tasks in designing a particular service. 1. Design a suitable algorithm for the security transformation. The algorithm should be such that an opponent cannot defeat its purpose. 2. Generate the secret information (keys) used by the algorithm 3. Develop methods to distribute and share the secret information 4. Specify a protocol enabling the principals to use the transformation and secret information for a security service Model for Network Access Security This model deals with protecting an information system from unwanted access. Safety from Hackers and Intruder is needed, as they can harm data. Two types of threats. 1. Information access threats : intercept or modify data on behalf of user. 2. Service Threats : exploit service flaws in computers to inhibit use by legitimate users Model for Network Access Security Viruses and worms are kind of S/W attacks. Such kind of attack can be introduced in systems by means of logic in disk or can be spread via network. Security Mechanisms needed to cope with this unwanted access fall into two broad categories 1. Gatekeeper : Includes password-based login procedure, which can deny to all but authorized users. And can have logic to detect and reject worms, viruses, and similar attacks. 2. Once unwanted user or S/W gains access, second line of defense consist of a variety of internal controls for monitoring activities and analyze stored information. Internet standards and The Internet society Q. How does a specification become a standard ? Explain ? Q. Describe the RFC publication procedure ? A Request for Comments (RFC) is a type of publication from the Internet Engineering Task Force (IETF) and the Internet Society (ISOC), the principal technical development and standards-setting bodies for the Internet. RFC is also an abbreviation for Remote Function Call . A Request for Comments(RFC) is a formal document from the Internet Engineering Task Force ( IETF ) that is the result of committee drafting and subsequent review by interested parties. Some RFCs are informational in nature. 70 It consist of three organizations 1. Internet Architecture Board (IAB) : Responsible for defining the overall architecture of the internet, providing guidance and broad direction to the IETF. (Internet Engineering Task Force) 2. Internet Engineering Task Force (IETF): The Protocol engineering and development arm of the Internet. 3.Internet Engineering Steering Group (IESG): Responsible for technical management of IETF activities and the Internet standards process. 71 Internet Engineering Task Force (IETF) working is divided into eight (8) areas, each with area director and working groups. General Application Internet Security Transport User Service Operations and Management Routing. 72 The work of the IETF is divided into eight areas, each with an area director and composed of numerous working groups: General: IETF processes and procedures. An example is the process for development of Internet standards. Applications: Internet applications. Examples include Web-related protocols, EDI-Internet integration, LDAP. Internet: Internet infrastructure. Examples include IPv6, PPP extensions. Operations and management: Standards and definitions for network operations. Examples include SNMPv3, remote network monitoring. 73 Routing: Protocols and management for routing information. Examples include multicast routing, OSPF. Security: Security protocols and technologies. Examples include Kerberos, IPSec, X.509, S/MIME, TLS. Transport: Transport layer protocols. Examples include differentiated services, IP telephony, NFS, RSVP. User services: Methods to improve the quality of information available to users of the Internet,. Examples include responsible use of the Internet, user services, FYI documents. 74 75 76 Left side of figure shows the series of steps Steps involved increasing amounts of security and testing. IETF make recommendation for advancement of protocol, at each steps. White boxes represents temporary states, which should be occupied for minimum practical time. Document must remain Proposed standard for at least six months and a draft sentence for at least four months for review and comments. Grey boxes represents long-termed states that must be occupied for years. 77 For specification to be advanced to Draft standard status, it is require minimum two independent and interoperable implementations. This generates operational experience. After significant implementation and operational experience, specification get elevated to Internet Standard. Now the specification is assigned STD number and RFC number. Finally the protocol become obsolete. And it is assigned to the Historic state. 78