* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Lesson 8
Integrated Services Digital Network wikipedia , lookup
PSTN network topology wikipedia , lookup
Total Information Awareness wikipedia , lookup
Computer network wikipedia , lookup
History of wildlife tracking technology wikipedia , lookup
Packet switching wikipedia , lookup
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Windows Vista networking technologies wikipedia , lookup
Telecommunications in Russia wikipedia , lookup
History of mobile phones wikipedia , lookup
Telecommunications engineering wikipedia , lookup
Deep packet inspection wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
History of telecommunication wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Computer security wikipedia , lookup
Telecommunication wikipedia , lookup
Business telephone system wikipedia , lookup
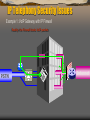
Securing Your Voice and Voice over Network Assets Lesson 08 Wiretapping and Eavesdropping Wiretapping Legal perspective (individual and gov) Techniques – Tape recorder – Lineman handset – Small RF transmitter in handset PBX soft wiretap Telephones as listening devices Eavesdropping Cordless (1.6-1.8MHz, 43.7-49.97MHz, 900MHz) Cellular – Conversation not the good stuff, the ‘serial’ number is -- cloning Telecommunications Fraud Blue Boxes blue box n. 1. obs. Once upon a time, before all-digital switches made it possible for the phone companies to move them out of band, one could actually hear the switching tones used to route long-distance calls. Early phreakers built devices called `blue boxes' that could reproduce these tones, which could be used to commandeer portions of the phone network. (This was not as hard as it may sound; one early phreak acquired the sobriquet `Captain Crunch' after he proved that he could generate switching tones with a plastic whistle pulled out of a box of Captain Crunch cereal!) There were other colors of box with more specialized phreaking uses; red boxes, black boxes, silver boxes, etc. 2. n. An IBM machine, especially a large (non-PC) one. (from Jargon File) Telecommunications Fraud PBX Fraud Common – A university with $200K bill – A computer manufacturer with $300K – “call sell” operation with $1.4M tag Risk of being caught generally low No special equipment needed There is money to be made in it! Commonly exploited through dial-up connection directly to the PBX – Discover number through war-dialing or social engineering – Once you have number, now you have to get past the password Octel Voice Network Login System Manager password is a # By default, set to 9999 From “Hacking Exposed” Copyright (C) 1994-1998 Octel Communications Corporation. All Rights Reserved Please Enter System Manager Password: Number must be entered Enter the password of either System Manager mailbox, then press “Return.” 9999 Williams PBX Type login Will be followed with prompt to enter user number. Requires four-digit numeric access code. – (how long will it take to guess one?) Meridian Links Looks similar in response to a Unix-based box userid: maint Password: maint will get you into management console userid: mluser Password: mluser will do the same will put you into a restricted unix shell ROLM PhoneMail Default Accounts: LOGIN: sysadmin LOGIN: tech LOGIN: poll PASSWORD: sysadmin PASSWORD: tech PASSWORD: tech ATT Definity G/System 75 Lots of possibilities here ATT UNIX S75 Login: Password: enquiry/enquirypw maint/rwmaint rcust/rcustpw support/supportpw kraft/kraftpw init/intpw locate/locatepw cust/custpw bcms/bcms craft/craftpw browse/looker tech/field inads/inads blue/bluepw field/support Threats to PBXs Theft of service – I.e., toll fraud, probably the most common of motives for attackers. Disclosure of information – data disclosed without authorization, either by deliberate action or by accident. Examples include both eavesdropping on conversations or unauthorized access to routing and address data. Data modification – data altered in some meaningful way by reordering, deleting or modifying it. For example, an intruder may change billing information, or modify system tables to gain additional services. Unauthorized access – actions that permit an unauthorized user to gain access to system resources or privileges Denial of service – actions that prevent the system from functioning in accordance with its intended purpose. A piece of equipment may be rendered inoperable or forced to operate in a degraded state. Traffic analysis – a form of passive attack in which an intruder observes information about calls and makes inferences from things such as the source and destination numbers, or the length or frequency of the calls. PBX security –vs- OS security PBXs are sophisticated computer systems, and many of the threats and vulnerabilities associated with OS’s are shared by PBXs. There are, however, two important distinctions: External access/control – Like larger telephone switches, PBXs typically require remote maintenance by the vendor. Instead of relying on local administrators to make operating system updates and patches, organizations normally have updates installed remotely by the switch manufacturer. This of course requires remote maintenance ports. Feature richness – The wide variety of features available on PBXs, particularly administrative features and conference functions, provide the possibility of unexpected attacks. A feature may be used by an attacker in a manner that was not intended by its designers. Features may also interact in unpredictable ways causing security problems. Even though the features may be fairly standard, the implementation between vendors is different, thus the reason instruments can often not be interchanged between PBXs. PBX susceptibility to tapping A PBX’s susceptibility to tapping depends on the methods used for communication between the PBX and its instruments. This may include voice, data, and signaling information. Signaling information is typically commands to the instrument (turn on indicators, microphones, speakers, etc.) and status from the instrument (hook status, keys pressed, etc.). Three general communication methods exist – Analog Voice with separate Control Signals – Analog Voice with inclusive Control Signals – Digital Voice with Inclusive Control Signals Analog Voice with separate Control Signals Simplest method. Analog voice is passed between the PBX and the instrument on either a single pair of wires or two pairs (one for transmit and one for receive). If there is any additional signaling communication (other than the hook switch) between the PBX and the instrument, it is done on wires that are separate from the voice pair(s). Voice information is transmitted essentially as it is picked up by the microphone. It is in a form that can be directly reproduced by a speaker. The voice line can be easily tapped by connecting an amplifier to the pair of voice wires. The amplified voice signal can then be heard directly with a speaker or headphones or be recorded. Analog Voice with inclusive Control Signals Analog voice and control signaling is passed between the PBX and the instrument on either a single pair of wires or two pairs. This can be done if the signal path is of high enough bandwidth to pass voice information (less than 4KHz) plus additional data information. For example, voice information can be combined with data information modulated onto a carrier tone that is centered outside of the voice band. Vulnerable to tapping by connecting an amplifier to the pair and passing signal through filters to separate the voice and data information. Data information can be recovered by demodulating the carrier tone. Digital Voice with Inclusive Control Signals Voice and control signaling data are passed across the same pair of wires. There may be two pairs of wires, one for each direction, or both directions could be combined onto one pair of wires using echo cancellation. Conventional tapping techniques won’t work against most types of digital lines. The format and type of digital signals that pass between the PBX and its instruments vary widely between vendors. If separate pairs are used for transmit and receive, each pair could be tapped to provide access to the bit streams but the format needs to be determined. Echo Cancellation If both transmit and receive are combined on one pair using echo cancellation, the previously described methods would not be useful for tapping. Each transmit end of the link can only determine what is being received by subtracting out what it is transmitting from the total signal. An outside observer tapping the line somewhere between the two ends would only have access to the total signal and would therefore find it very difficult to reproduce either end. An attack would depend on a known original condition on an end. Maintenance Feature Vulnerabilities Maintenance-out-of-service (MOS) – this feature allows maintenance personnel to place a line out of service for maintenance. If a line is placed MOS while it is in operation, the PBX may terminate its signaling communication with the instrument and leave the instrument’s voice channel connection active even after the instrument is placed onhook. Line Testing Capabilities – the ability to connect two lines together in order to transmit data from one line to the other and verify whether or not the second line receives the data properly. This feature would allow someone with maintenance access to connect a user’s instrument to an instrument at another location in order to eavesdrop on the area surrounding the user’s instrument without the user’s knowledge. Securing Voice over Networks The Promise of IP Telephony World moving toward “converged” networks Benefits usually cited for implementing VoIP Long-Distance toll savings Increased number of calls with less bandwidth Additional and enhanced services Most efficient use of IP assets Combined network/telecom infrastructure Additional Issues Related VoIP Issues International calls Telemarketing Call Centers Facsimile IP Telephony Protocols H.323 ITU -- 1996, 1998, 1999 SIP – Session Initiation Protocol IETF -- 1999 MGCP – Media Gateway Control Protocol (Megaco/H.248) IETF/ITU -- 1999 IP Telephony Overview H.323 Architecture Router MCU Gatekeeper Gatekeeper Ethernet Phone intranet, Internet, VPNs Ethernet Phone H.323 Terminal Gateway PBX-std. Phone Packet-switched IP Network H.323 Terminal Router Gateway PBX Circuit-switched Networks Standard Phone PBX PSTN, ISDN, wireless From: “Security Requirements and Constraints of VoIP” by Mika Marjalaakso H.323 Components Terminal – a terminal, or a client, is an endpoint where H.323 data streams and signaling originate and terminate. It may be a multimedia PC with a H.323 compliant stack or a standalone device such as a USB (universal serial bus) IP telephone. A terminal must support audio communication; video and data communication support is optional. Gateway – a gateway is an optional component in a H.323enabled network. When communication is required between different networks a gateway is needed at the interface. It provides data format translation, control signaling translation, audio and video codec translation, and call setup and termination functionality on both sides of the network. H.323 Components (cont.) Gatekeeper – a gatekeeper is a very useful, but optional, component of an H.323-enabled network. Gatekeepers are needed to ensure reliable, commercially feasible communications. When a gatekeeper exists all endpoints (terminals, gateways, and MCUs) must be registered with it. A gatekeeper provides several services to all endpoints in its zone. These services include: – – – – Address translation Admission and access control of endpoints Bandwidth management Routing capability H.323 Components (cont.) MCU – a multipoint control unit (MCU) enables conferencing between three or more endpoints. Although the MCU is a separate logical unit it may be combined into a terminal, gateway, or gatekeeper. The MCU is an optional component of an H.323-enabled network. The multipoint controller provides a centralized location for multipoint call setup. Call and control signaling are routed through the MC so that endpoints capabilities can be determined and communication parameters negotiated. Standards for IP Telephony H.323 for IP Telephony Video Audio H.261 H.263 (video Coding) G.711 G.722 G.723 G.728 G.729 RTP RTCP RTP Control Data H.245 H.225 H.225 Terminal to gatekeeper signaling Call signaling T.120 (Multipoint data transfer) RTCP Unreliable Transport (UDP) Reliable Transport (TCP) From: IP Telephony, by Goralski & Kolon H.225 and H.245 H.225 performs the signaling for call control uses H.245 to establish and terminate individual logical channels for communication Five phases of signaling process Call setup Initial communications and capability exchange Establishment of audiovisual communication Call services Call termination Encoding techniques 70 60 50 Data Rate Delay (ms) Quality (MOS) 40 30 20 10 0 G.711 G.722 G.726 G.728 G.729 G.723 From: IP Telephony, by Goralski & Kolon IP Telephony Overview Session Initiation Protocol (SIP) Architecture Location Server Redirect Server Proxy Server SIP Phone Proxy Server Packet-switched IP Network SIP Terminal intranet, Internet, VPNs SIP Phone Router SIP Terminal Router From: “Security Requirements and Constraints of VoIP” by Mika Marjalaakso IP Telephony Overview MGCP, H.248/Megaco Architecture Media Gateway Controller Signaling Conversion Sigtran Signaling Gateway Media Gateway Controller IP Signaling H323, SIP, ISUP Signaling Conversion Sigtran Signaling Gateway Packet-switched IP Network PSTN Signaling SS7, ISDN, Q.Sig PSTN Signaling SS7, ISDN, Q.Sig Media GW Control MGCP, Megaco/H.248 SS7 PSTN SS7 Media RTP/RTCP TDM Media Gateway TDM PSTN Media Gateway From: “Security Requirements and Constraints of VoIP” by Mika Marjalaakso IP Telephony Overview The Protocol Stack Signaling Gateway Control Media H.323 H.450.x H.235 H.225.0 (Q.931) H.245 Codecs (A/V) MGCP RAS SIP SGCP TCP IPDC H.248 Megaco RTP RTCP RTSP UDP IP From: “Security Requirements and Constraints of VoIP” by Mika Marjalaakso Approaches to IP Telephony Strategy One (PBX Vendors) PBX Private Branch Exchange T1 Phones ISDN ANALOG Approaches to IP Telephony Strategy One-a (PBX Vendors) PBX Private Branch Exchange T1 Phones ISDN ANALOG Approaches to IP Telephony Strategy Two (Networking Vendors) PBX Private Branch Exchange Data Switch IP Phones Approaches to IP Telephony Strategy Three (Telecom Firewall) PBX Private Branch Exchange T1 ISDN ANALOG Least cost Routing Security – PSTN & Internet Leverage Existing Infrastructure Quality of Service Issues “Perhaps the most vexing problem in voice- over-IP, in general, has been the issue of quality of service (QoS). The delay in conversation that many VoIP users encounter is caused by the jitter and latency of packet delivery within the Internet itself” [J. Rosenberg, Computer Telephony: The SIP Protocol. June 2000] Quality of Service Issues Bandwidth (minimum) Latency (maximum) Jitter (delay variation) Packet loss (network congestion or errors) Availability (individual) Reliability (network) Network Reliability Reliability 99% 99.5% 99.9% 99.95% 99.99% 99.995% 99.999% Total yearly Downtime 3.65 days 1.825 days 8.76 hours 4.38 hours 52.56 minutes 26.28 minutes 5.25 minutes From: IP Telephony, by Goralski & Kolon Quality of Service Issues Prevailing IP Telephony thinking: security reduces QoS to unacceptable levels security or QoS - but not both let’s fix QoS then worry about security security and QoS are competing requirements security isn’t necessary over well-managed IP networks (e.g. “I’m not using the Internet, so why worry.”) Quality of Service Issues Scheduled downtime is not a term used in the telephony world. Security is not usually thought of as a QoS issue -- but it should be! VoIP Security “It may seem painfully obvious, but it’s important to remember that a VoIP network is an IP network. Any VoIP device is an IP device, and it’s therefore vulnerable to the same types of attacks as any other IP device. In addition, a VoIP network will almost always have non-VoIP devices attached to it and be connected to other mission-critical networks.” Dr. Andrew Molitor, Aravox Technologies Special VoIP Security Considerations Availability requirements for VoIP are extremely critical, higher than normal network operations. VoIP applications are badly behaved IP applications. Tend to use dynamically negotiated ports. Makes security job harder since we don’t know in advance which port numbers represent legitimate communication. VoIP applications are more sensitive to delays and other performance issues IP designed to work over slow, noisy networks. Current IP security devices designed to meet the needs of a data-oriented network. IP Telephony Security Issues Security in IP Telephony achieved using built-in mechanisms of protocols achieved using external application or network layer protocols (e.g. IPSEC) IP Telephony Security Issues Benefits of Security in IP Telephony Confidentiality Integrity Availability Authentication Non-repudiation IP Telephony Security Issues Basic Threats to Traditional Telephony Phone disturbance Prank calls Free calls using someone else’s phone number Masquerading as someone else Denial-of-Service attacks aimed at phone system Attacks aimed at telephony equipment – Voicemail attacks – PBX configuration port attacks IP Telephony Security Issues Basic Threats to IP Telephony Data network access through VoIP ports (tunneling) Free long distance calls over PSTN (spoofing) Eavesdrop on conversations (packet sniffing) Record conversations without authorization Modify, delete, or replace fax/voice packets Forward incoming phone calls to somewhere else Denial-of-Service attack on business phone system Denial-of-Service attack on business data network Expose private conversations on Internet Hijack conversations Block calls of targeted individuals Log all calls through an organization The Threats to VoIP Attack Category Denial of Service Eavesdropping Unauthorized Access Spoofing Information Loss Repudiation Information Corruption Likelihood 3 2-3 Impact 3 1-3 2-3 2 1-2 1-2 1 Risk Factor 9 7 2-3 3 3 3 3 7 6 5 5 3 DTR/TIPHON-08002 V0.1.8 (2000-12-07) Telecommunications and Internet Protocol Harmonization over Networks (TIPHON Eavesdropping on VoIP IP Telephony Security Issues Security Constraints – the reason why security in IP Telephony is practically non-existent adds latency to the voice packet increases computational load of network devices doesn’t work well with data-centric VPNs doesn’t work well with data-centric firewalls increases bandwidth requirements public-key infrastructure not globally available doesn’t work well with NAT-enabled routers/firewalls IP Telephony Security Issues Example 1: VoIP Gateway with IP Firewall The Ideal - the Firewall allows VoIP packets across 10/100 GW IP Firewall PBX Internet PSTN Router IP Telephony Security Issues Example 1: VoIP Gateway with IP Firewall Reality - the Firewall blocks VoIP packets 10/100 GW IP Firewall PBX Internet PSTN Router IP Telephony Security Issues Example 1: VoIP Gateway with IP Firewall Some firewall ports are left open to allow VoIP packets. Danger – opened VoIP ports can be attacked 10/100 GW IP Firewall PBX Internet PSTN Router VoIP - Capable Firewalls Firewalls have to support IP telephony to allow use of VoIP or IP telephony has to support firewalls to allow use of VoIP A VoIP Capable Firewall should: Allow a host to send packets to another through dynamically assigned ports, Allow signaling devices to “control” the firewall. IP Telephony Security Issues Traditional Responses to Security Threats IP Firewalls – must prioritize to not delay critical packets such as VoIP – must handle multiple dynamic UDP port assignments – must be able to handle or else not use NAT VPNs – must prioritize VoIP packets – must handle numerous smaller packets – must not add too much latency Encryption – needs to be FAST – PKI issues need to be addressed Summary What is the Importance and Significance of this material? How does this topic fit into the subject of “Voice and Data Security”?