KPMG Screen template
... © 2014 KPMG LLP, a Canadian limited liability partnership and a member firm of the KPMG network of independent member firms affiliated with KPMG International Cooperative (“KPMG International”), a Swiss entity. All rights reserved. The KPMG name, logo and “cutting through complexity” are registered ...
... © 2014 KPMG LLP, a Canadian limited liability partnership and a member firm of the KPMG network of independent member firms affiliated with KPMG International Cooperative (“KPMG International”), a Swiss entity. All rights reserved. The KPMG name, logo and “cutting through complexity” are registered ...
Network Reference Model for cdma2000 Spread Spectrum
... • the ability to accept call contents for each intercept subject over one or more channels from each Access function. • the ability to deliver call contents for each intercept subject over one or more channels to a Collection Function as authorized for each law enforcement agency. • the ability to a ...
... • the ability to accept call contents for each intercept subject over one or more channels from each Access function. • the ability to deliver call contents for each intercept subject over one or more channels to a Collection Function as authorized for each law enforcement agency. • the ability to a ...
Interest Management - Newcastle University
... • Entities have control over their aura by permitting information dissemination to be restricted to particular regions on the virtual environment. – Subscribers have limited control over their nimbi because they can only filter based on a sender’s location. ...
... • Entities have control over their aura by permitting information dissemination to be restricted to particular regions on the virtual environment. – Subscribers have limited control over their nimbi because they can only filter based on a sender’s location. ...
Lesson 8
... techniques won’t work against most types of digital lines. The format and type of digital signals that pass between the PBX and its instruments vary widely between vendors. If separate pairs are used for transmit and receive, each pair could be tapped to provide access to the bit streams but the f ...
... techniques won’t work against most types of digital lines. The format and type of digital signals that pass between the PBX and its instruments vary widely between vendors. If separate pairs are used for transmit and receive, each pair could be tapped to provide access to the bit streams but the f ...
Kumar`s Security Slides
... secret key Ki known only to the HLR. * When MS notifies local MSC of its presence, local VLR contacts the HLR * VLR transmits it own identity , MS indentity (IMSI) and position to HLR. * HLR queries its AUc for a set of triplets containing a challenge, a signed response SRES and corresponding sessio ...
... secret key Ki known only to the HLR. * When MS notifies local MSC of its presence, local VLR contacts the HLR * VLR transmits it own identity , MS indentity (IMSI) and position to HLR. * HLR queries its AUc for a set of triplets containing a challenge, a signed response SRES and corresponding sessio ...
Standards for multimedia communications
... 5.3 Standards relating to interpersonal communications • Interpersonal communications such as telephony, video telephony, data conferencing, and videoconferencing can be provided both by circuit-mode networks and packetmode networks. • Most of the standards relating to these applications have been ...
... 5.3 Standards relating to interpersonal communications • Interpersonal communications such as telephony, video telephony, data conferencing, and videoconferencing can be provided both by circuit-mode networks and packetmode networks. • Most of the standards relating to these applications have been ...
The origin of Complexity - Brain Dynamics Laboratory
... biological systems face. The evolutionary success of biological structures and organisms depends on their ability to capture information about the environment, be it molecular or ecological. • Biological complexity may then emerge as a result of evolutionary pressure on the effective encoding of str ...
... biological systems face. The evolutionary success of biological structures and organisms depends on their ability to capture information about the environment, be it molecular or ecological. • Biological complexity may then emerge as a result of evolutionary pressure on the effective encoding of str ...
section 16290 - Siemens Industry
... configuration of the device can also be performed through the browser. Web pages must be configurable to allow custom HTML pages to be created. Device must also support display of downstream devices from the web browser, i.e. feeders and trip units on customizable web pages within the meter. c. ...
... configuration of the device can also be performed through the browser. Web pages must be configurable to allow custom HTML pages to be created. Device must also support display of downstream devices from the web browser, i.e. feeders and trip units on customizable web pages within the meter. c. ...
section 16290
... configuration of the device can also be performed through the browser. Web pages must be configurable to allow custom HTML pages to be created. Device must also support display of downstream devices from the web browser, i.e. feeders and trip units on customizable web pages within the meter. c. ...
... configuration of the device can also be performed through the browser. Web pages must be configurable to allow custom HTML pages to be created. Device must also support display of downstream devices from the web browser, i.e. feeders and trip units on customizable web pages within the meter. c. ...
Monica Nusskern Week 9 Final Exam
... data mining technique if the relationship between the dependent and the independent variable is linear and not as much so when the outcome is binary in nature. This is due to the restrictions that are placed on the value of the dependent variable that cannot be determined by the equation. Good e. Lo ...
... data mining technique if the relationship between the dependent and the independent variable is linear and not as much so when the outcome is binary in nature. This is due to the restrictions that are placed on the value of the dependent variable that cannot be determined by the equation. Good e. Lo ...
Chapter 1
... • When converting digital data to digital signals common techniques are used : – Non-Return to Zero (NRZ) uses two levels of signaling or is bipolar – The two levels or states can be expressed as either on or off or high or low – This is the most basic and simplistic method of encoding ...
... • When converting digital data to digital signals common techniques are used : – Non-Return to Zero (NRZ) uses two levels of signaling or is bipolar – The two levels or states can be expressed as either on or off or high or low – This is the most basic and simplistic method of encoding ...
Introduction to network security
... Computer security is not restricted to these three broad concepts. Additional ideas that are often considered part of the taxonomy of computer security include: Access control -- Ensuring that users access only those resources and services that they are entitled to access. Nonrepudiation -- Ensuring ...
... Computer security is not restricted to these three broad concepts. Additional ideas that are often considered part of the taxonomy of computer security include: Access control -- Ensuring that users access only those resources and services that they are entitled to access. Nonrepudiation -- Ensuring ...
lecture26
... • Known attacks and intrusion scenarios • Specific actions or patterns of behavior that are suspicious or known security violations ...
... • Known attacks and intrusion scenarios • Specific actions or patterns of behavior that are suspicious or known security violations ...
Ultralink/Ultrawire Downhole Controller
... The XTU Downhole Controller is an intelligent bridge between the Ultrawire toolbus and the NHI Ultralink telemetry system. It serves both as a communications interface and as a programmable logging controller. It also incorporates a dc-dc converter (switch mode power supply) to convert the high volt ...
... The XTU Downhole Controller is an intelligent bridge between the Ultrawire toolbus and the NHI Ultralink telemetry system. It serves both as a communications interface and as a programmable logging controller. It also incorporates a dc-dc converter (switch mode power supply) to convert the high volt ...
Ken Kavanagh, August 2014(opens in new window)
... information held by public authorities is a fundamental human [writer’s emphasis] right which should be given effect at the national level through comprehensive legislation (for example, Freedom of Information Acts) based on the principle of maximum disclosure, establishing a presumption that all in ...
... information held by public authorities is a fundamental human [writer’s emphasis] right which should be given effect at the national level through comprehensive legislation (for example, Freedom of Information Acts) based on the principle of maximum disclosure, establishing a presumption that all in ...
ICT & Prog
... The arithmetic/logic unit (ALU) contains the electronic circuitry that executes all arithmetic and logical operations. The control unit (CU) of the CPU contains circuitry that uses electrical signals to direct the entire computer system to carry out, ...
... The arithmetic/logic unit (ALU) contains the electronic circuitry that executes all arithmetic and logical operations. The control unit (CU) of the CPU contains circuitry that uses electrical signals to direct the entire computer system to carry out, ...
Cisco Network Visibility Flow Protocol Specification
... Interface Info template records identify each interface instance on the endpoint. Any change in to interface attributes should trigger a new Interface Info record to be sent with corr ...
... Interface Info template records identify each interface instance on the endpoint. Any change in to interface attributes should trigger a new Interface Info record to be sent with corr ...
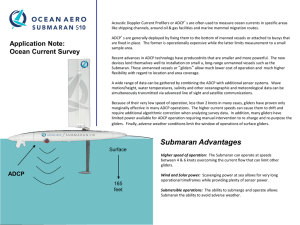
Submaran Ap Notes - Oceanology International North America
... various noise and make accurate identifications. Advanced third party software is also be able to differentiate between species. Tracking information is then communicated via Iridium satellite link to a base station accessible via internet. The system can be programmed to communicate at specific int ...
... various noise and make accurate identifications. Advanced third party software is also be able to differentiate between species. Tracking information is then communicated via Iridium satellite link to a base station accessible via internet. The system can be programmed to communicate at specific int ...
CAANS Overdose Awareness Day Media Release
... Red Deer - Red Deer joins Edmonton and Calgary and other centres in holding an International Overdose Awareness Day event on Friday, August 29th. International Overdose Awareness Day is a global event held each year to raise awareness of overdose and reduce the stigma of drug-related deaths. It also ...
... Red Deer - Red Deer joins Edmonton and Calgary and other centres in holding an International Overdose Awareness Day event on Friday, August 29th. International Overdose Awareness Day is a global event held each year to raise awareness of overdose and reduce the stigma of drug-related deaths. It also ...
Integrated Design Techniques Ltd www .idtuk.com Communications
... withdrawal of these circuits the traffic management industry panicked as it meant that traffic lights might stop working. UTMC to the rescue (?) The UTMC initiative was conceived to address this specific problem. It has, however, tackled it in rather a roundabout way. The core problem was defined in ...
... withdrawal of these circuits the traffic management industry panicked as it meant that traffic lights might stop working. UTMC to the rescue (?) The UTMC initiative was conceived to address this specific problem. It has, however, tackled it in rather a roundabout way. The core problem was defined in ...
10209144R1 - Telecommunications Industry Association
... Each message consists of the r field, the message ID field, R field, Sync state field, and Octets field. The r field and message ID field together comprise one octet. The R field and Sync State field comprise one octet. Octets field contains an integral number of octets. If the message contains HDLC ...
... Each message consists of the r field, the message ID field, R field, Sync state field, and Octets field. The r field and message ID field together comprise one octet. The R field and Sync State field comprise one octet. Octets field contains an integral number of octets. If the message contains HDLC ...
Chapter 1 - William Stallings, Data and Computer Communications
... rely in part on common carrier circuits alternative technologies used include: ...
... rely in part on common carrier circuits alternative technologies used include: ...
Pharmacovigilance Workshop II 20th June 2003 Medicines
... Workshop II 20th June 2003 Medicines Regulation Michael Bonett ...
... Workshop II 20th June 2003 Medicines Regulation Michael Bonett ...
Total Information Awareness

Total Information Awareness (TIA) was a program of the US Information Awareness Office. It was operated from February until May 2003, before being renamed as the Terrorism Information Awareness Program.Based on the concept of predictive policing, TIA aimed to gather detailed information about individuals in order to anticipate and prevent crimes before they are committed. As part of efforts to win the War on Terror, the program searched for all sorts of personal information in the hunt for terrorists around the globe. According to Senator Ron Wyden (D-Ore.), TIA was the ""biggest surveillance program in the history of the United States"".The program was suspended in late 2003 by the United States Congress after media reports criticized the government for attempting to establish ""Total Information Awareness"" over all citizens.Although the program was formally suspended, its data mining software was later adopted by other government agencies, with only superficial changes being made. According to a 2012 New York Times article, the legacy of Total Information Awareness is ""quietly thriving"" at the National Security Agency (NSA).