8.2 Interim Agreements on Key Issue #2: QoS
... 1a. Reflective QoS indication is signalled via inband or not signalled at all by the network. How to indicate reflective QoS to the UE is decided by the network during the PDU session establishment procedure. When reflective QoS is not signalled, all uplink flows use reflective QoS if there are corr ...
... 1a. Reflective QoS indication is signalled via inband or not signalled at all by the network. How to indicate reflective QoS to the UE is decided by the network during the PDU session establishment procedure. When reflective QoS is not signalled, all uplink flows use reflective QoS if there are corr ...
D2vol3 - EURESCOM Home Page
... Dedicated protection means that the entity to be protected is protected using dedicated resources. For example, in a ring the OCs are duplicated when inserted, one going in the clockwise direction, while the other goes in the anti-clockwise direction. The receiver selects the best signal by means of ...
... Dedicated protection means that the entity to be protected is protected using dedicated resources. For example, in a ring the OCs are duplicated when inserted, one going in the clockwise direction, while the other goes in the anti-clockwise direction. The receiver selects the best signal by means of ...
Universal WiFi Range Extender WN3000RP
... wireless device) to its wireless network. 3. Within 2 minutes, press the WPS button on your wireless device, or follow the WPS instructions that came with your wireless device. Your wireless device is now connected to the Extender. To log in to the Extender and use WPS to connect: 1. From the Extend ...
... wireless device) to its wireless network. 3. Within 2 minutes, press the WPS button on your wireless device, or follow the WPS instructions that came with your wireless device. Your wireless device is now connected to the Extender. To log in to the Extender and use WPS to connect: 1. From the Extend ...
AT Commands for GPRS
... response. Otherwise, the MT issues the intermediate result code CONNECT and enters V.25ter online data state. GPRS attachment and PDP context activation procedures may take place prior to or during the PDP startup if they have not already been performed using the +CGATT and +CGACT commands. If conte ...
... response. Otherwise, the MT issues the intermediate result code CONNECT and enters V.25ter online data state. GPRS attachment and PDP context activation procedures may take place prior to or during the PDP startup if they have not already been performed using the +CGATT and +CGACT commands. If conte ...
BASrouters — BACnet Routing Examples
... In a tunnelling application, a lower speed technology uses a high speed technology to pass data between two lower speed segments without any change in the end-to-end protocol. With this approach, minimal understanding of the high speed protocol is required. In this example, two BACnet MS/TP networks ...
... In a tunnelling application, a lower speed technology uses a high speed technology to pass data between two lower speed segments without any change in the end-to-end protocol. With this approach, minimal understanding of the high speed protocol is required. In this example, two BACnet MS/TP networks ...
EDTECH 552, lab 4 Lab 4.1 Convert Numbers among the binary
... An IPv6 address is a 128-bit address made up of two parts, the network portion, identified by the first 64 bits, or first four hextets, and the host portion, which is identified by the last 64 bits, or last four hextets. Remember that each number, or character, in an IPv6 address is written in hexad ...
... An IPv6 address is a 128-bit address made up of two parts, the network portion, identified by the first 64 bits, or first four hextets, and the host portion, which is identified by the last 64 bits, or last four hextets. Remember that each number, or character, in an IPv6 address is written in hexad ...
OpenFlow1.3 GUI Manual
... form a control plane, and their connections are represented in the graphical user interface (GUI) as grey lines, as shown in the diagram below. In addition, the data plane can be formed by connecting OpenFlow switches to other network devices, such as other OpenFlow switches or hosts. Data plane con ...
... form a control plane, and their connections are represented in the graphical user interface (GUI) as grey lines, as shown in the diagram below. In addition, the data plane can be formed by connecting OpenFlow switches to other network devices, such as other OpenFlow switches or hosts. Data plane con ...
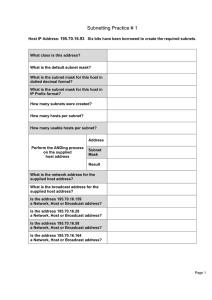
Subnetting Practice # 1
... You are the network administrator for Mangiare Food Supplies in Rome and are required to subnet the network according to the diagram. You have decided to use the network 172.31.0.0. It is the corporate policy that the IP address assigned to a default gateway is always the last host address in the su ...
... You are the network administrator for Mangiare Food Supplies in Rome and are required to subnet the network according to the diagram. You have decided to use the network 172.31.0.0. It is the corporate policy that the IP address assigned to a default gateway is always the last host address in the su ...
VMware Virtual SAN Network Design Guide
... The following sections review general guidelines that should be followed when designing Virtual SAN network. These recommendations do not conflict with general vSphere network design best practices. ...
... The following sections review general guidelines that should be followed when designing Virtual SAN network. These recommendations do not conflict with general vSphere network design best practices. ...
Network Reference Model for cdma2000 Spread Spectrum
... Emergency Service Network Entity (ESNE) The ESNE routes and processes the voice band portions of the emergency calls. This is composed of selective routers (also known as Routing, Bridging, and Transfer Switches), public safety answering points and emergency agencies. The structure of the Emergency ...
... Emergency Service Network Entity (ESNE) The ESNE routes and processes the voice band portions of the emergency calls. This is composed of selective routers (also known as Routing, Bridging, and Transfer Switches), public safety answering points and emergency agencies. The structure of the Emergency ...
Packet Optical Networking for LTE Cell Tower Backhaul
... High bandwidth cell site base stations upgrade to Ethernet Ethernet over SONET on MSPPs not efficient for packet-centric traffic • How do you evolve this to a more efficient technology? Backhaul Network ...
... High bandwidth cell site base stations upgrade to Ethernet Ethernet over SONET on MSPPs not efficient for packet-centric traffic • How do you evolve this to a more efficient technology? Backhaul Network ...
《Electromagnetic Field and Microwave Technology》 Course syllabus
... (1)The history of Circuit switch development (2)Circuit switch foundation. (3)Basic switch unit (4)Switch network 3 Digital program-controlled switching technology (12 class hour) (1) Characteristics and business performance of digital program-controlled switchboard (2)hardware structure of digital ...
... (1)The history of Circuit switch development (2)Circuit switch foundation. (3)Basic switch unit (4)Switch network 3 Digital program-controlled switching technology (12 class hour) (1) Characteristics and business performance of digital program-controlled switchboard (2)hardware structure of digital ...
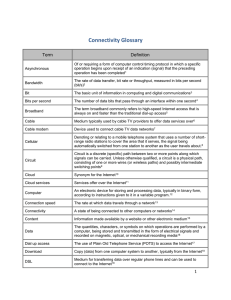
Connectivity Glossary
... The term broadband commonly refers to high-speed Internet access that is always on and faster than the traditional dial-up access5 ...
... The term broadband commonly refers to high-speed Internet access that is always on and faster than the traditional dial-up access5 ...
Communicating over the Network - Seneca
... Function of Protocol in Network Communication Technology independent Protocols – Many diverse types of devices can communicate using the same sets of protocols – This is because protocols specify network functionality, not the underlying technology to support this functionality ...
... Function of Protocol in Network Communication Technology independent Protocols – Many diverse types of devices can communicate using the same sets of protocols – This is because protocols specify network functionality, not the underlying technology to support this functionality ...
Distribution Loss Factors - Australian Energy Regulator
... “Distribution loss factors must be determined by the DNSP for all connection on its distribution network either individually, for all connection points assigned to a single transmission network connection point under clause 3.6.3(c), or collectively, for all connection points assigned to a transmiss ...
... “Distribution loss factors must be determined by the DNSP for all connection on its distribution network either individually, for all connection points assigned to a single transmission network connection point under clause 3.6.3(c), or collectively, for all connection points assigned to a transmiss ...
True-False Questions
... b. network topology in which all computers are linked by a closed loop in a manner that passes data in one direction from one computer to another. c. network topology linking a number of computers by a single circuit with all messages broadcast to the entire network. d. network architecture that giv ...
... b. network topology in which all computers are linked by a closed loop in a manner that passes data in one direction from one computer to another. c. network topology linking a number of computers by a single circuit with all messages broadcast to the entire network. d. network architecture that giv ...
EEE449 Computer Networks - Universiti Sains Malaysia
... The essence of BGP is the exchange of routing information among participating routers in multiple ASs. a router that implements BGP will also implement an internal routing protocol such as OSPF to exchange routing information with other routers within the AS Next, the router can issue an Update mess ...
... The essence of BGP is the exchange of routing information among participating routers in multiple ASs. a router that implements BGP will also implement an internal routing protocol such as OSPF to exchange routing information with other routers within the AS Next, the router can issue an Update mess ...
Ethernet - Binus Repository
... cable) is an Ethernet network that typically uses unshielded twisted-pair (UTP) to connect computers. While 10BaseT normally uses UTP, shielded twisted-pair (STP) will also work without changing any of the 10BaseT parameters. Most networks of this type are configured in a star pattern but internally ...
... cable) is an Ethernet network that typically uses unshielded twisted-pair (UTP) to connect computers. While 10BaseT normally uses UTP, shielded twisted-pair (STP) will also work without changing any of the 10BaseT parameters. Most networks of this type are configured in a star pattern but internally ...
Sample – Firewall PowerPoint
... What does a Firewall do? • Firewalls examine each data packet “passing through” the firewall • Firewalls can control access based on a number of parameters, depending on the type of firewall -– ...
... What does a Firewall do? • Firewalls examine each data packet “passing through” the firewall • Firewalls can control access based on a number of parameters, depending on the type of firewall -– ...
4100ES, 4190, 4010ES and 4010 Network
... using 4190-9010 Bi-Directional Coupler is the same with either size cable because the coupler input cables are 62.5/125 fiber allowing launch power to be the same. 4. Dual Fiber optic distances are using 4010-9819, 4100-6057 or 4190-6037 media modules. Single fiber optic distances require using 4190 ...
... using 4190-9010 Bi-Directional Coupler is the same with either size cable because the coupler input cables are 62.5/125 fiber allowing launch power to be the same. 4. Dual Fiber optic distances are using 4010-9819, 4100-6057 or 4190-6037 media modules. Single fiber optic distances require using 4190 ...
CCNA2 Chapter 1 Wide Area Networks and Routers
... WAN – Wide Area Networks WAN is a data communications network that operates beyond a LAN’s geographic scope. ...
... WAN – Wide Area Networks WAN is a data communications network that operates beyond a LAN’s geographic scope. ...
- IEEE Mentor
... operators it holds roaming agreements with so that the UE can decide whether to attach to the network or not. TS 23.234 [1] suggests using the SSID (Service Set ID) in the beacon signal for 802.11. It is unclear exactly how this would work and by being specific to the individual standards (e.g. 802. ...
... operators it holds roaming agreements with so that the UE can decide whether to attach to the network or not. TS 23.234 [1] suggests using the SSID (Service Set ID) in the beacon signal for 802.11. It is unclear exactly how this would work and by being specific to the individual standards (e.g. 802. ...
3GPP TSG-SA2 Meeting #30
... and which operators it holds roaming agreements with so that the UE can decide whether to attach to the network or not. TS 23.234 [1] suggests using the SSID (Service Set ID) in the beacon signal for 802.11. It is unclear exactly how this would work and by being specific to the individual standards ...
... and which operators it holds roaming agreements with so that the UE can decide whether to attach to the network or not. TS 23.234 [1] suggests using the SSID (Service Set ID) in the beacon signal for 802.11. It is unclear exactly how this would work and by being specific to the individual standards ...
PSTN network topology

A PSTN network topology is the switching network topology of a telephone network connected to the public switched telephone network (PSTN).In the United States and Canada, the Bell System network topology was the switching system hierarchy implemented and operated from the late 1940s to the 1980s for the purpose of integrating the diverse array of local telephone companies and telephone numbering plans to achieve nationwide Direct Distance Dialing (DDD) by telephone subscribers. It was the precursor of the world-wide interconnected public switched telephone network (PSTN).The ideas originated in the Bell System in the United States, but were soon adopted by other countries where telephone operators were facing similar issues, even when service smaller geographic areas. The system in the United Kingdom implemented by the General Post Office resulted in fewer switching levels than the Bell System.