ready to `software define` your Wide area network?
... vendors that Mulhall, an IT director at SnoIsle Libraries in Washington state, had never encountered before. One of them was a startup called Talari Networks, which back then billed its technology as “adaptive private networking.” The company claimed its appliances could supplant a costly MPLS netwo ...
... vendors that Mulhall, an IT director at SnoIsle Libraries in Washington state, had never encountered before. One of them was a startup called Talari Networks, which back then billed its technology as “adaptive private networking.” The company claimed its appliances could supplant a costly MPLS netwo ...
New Methods of Telephony Service
... The Internet Engineering Task Force (IETF) ratified Session Initiation Protocol (SIP) in August 1998 as a Proposed Internet Standard Request For Comment 2543 [12]. SIP ‘is an application-layer control (signaling) protocol for creating, modifying and terminating sessions with one or more participants ...
... The Internet Engineering Task Force (IETF) ratified Session Initiation Protocol (SIP) in August 1998 as a Proposed Internet Standard Request For Comment 2543 [12]. SIP ‘is an application-layer control (signaling) protocol for creating, modifying and terminating sessions with one or more participants ...
presentation source - CECS Multimedia Communications
... Data temporarily store in those buffers when sending to or receiving from the network In transmission of large files such as video frames, buffer capacity is very often inadequate to send or receive in realtime ...
... Data temporarily store in those buffers when sending to or receiving from the network In transmission of large files such as video frames, buffer capacity is very often inadequate to send or receive in realtime ...
William Stallings Data and Computer Communications
... Designed to be more efficient than X.25 Developed before ATM Larger installed base than ATM ATM now of more interest on high speed networks ...
... Designed to be more efficient than X.25 Developed before ATM Larger installed base than ATM ATM now of more interest on high speed networks ...
cellular - D
... Offers scalable bandwidths, from less than 5MHz up to 20MHz, together with support for both FDD (Frequency Division Duplex) paired and TDD (Time Division Duplex) ...
... Offers scalable bandwidths, from less than 5MHz up to 20MHz, together with support for both FDD (Frequency Division Duplex) paired and TDD (Time Division Duplex) ...
What is Leased Line
... University and Research networks before the Internet became widely available. ...
... University and Research networks before the Internet became widely available. ...
Standards for multimedia communications
... packets lost/corrupted and the interarrival jitter such that the corresponding end systems can use them to optimize the number and size of receiver buffers and to determine if the retransmission of lost packets is feasible. Call setup • LANs do not provide a guaranteed QoS and have no procedures to ...
... packets lost/corrupted and the interarrival jitter such that the corresponding end systems can use them to optimize the number and size of receiver buffers and to determine if the retransmission of lost packets is feasible. Call setup • LANs do not provide a guaranteed QoS and have no procedures to ...
Question Bank - Technical Symposium.
... 3. What is meant by piggybacking? What are its advantages and disadvantages? 4. How are errors caused in transmission lines? 5. Explain the Binary and Manchester encoding techniques with an example. 6. What is meant by congestion? List the ways of avoiding congestion. 7. Discuss the issues in networ ...
... 3. What is meant by piggybacking? What are its advantages and disadvantages? 4. How are errors caused in transmission lines? 5. Explain the Binary and Manchester encoding techniques with an example. 6. What is meant by congestion? List the ways of avoiding congestion. 7. Discuss the issues in networ ...
DwB Standard Presentation
... however only from accredited point of access in Germany. Humboldt University is accredited. France allows access from researchers own office in France as well as in other European countries ...
... however only from accredited point of access in Germany. Humboldt University is accredited. France allows access from researchers own office in France as well as in other European countries ...
Mobile Communication
... telephone network infrastructure (i.e., the Public Switched Telephone Network [PSTN]). It performs all switching and signaling functions for MSs located in its area. ...
... telephone network infrastructure (i.e., the Public Switched Telephone Network [PSTN]). It performs all switching and signaling functions for MSs located in its area. ...
William Stallings Data and Computer Communications
... Networking What are the differences? Communication - focuses on the transmission of data from one end, called the source, to another end, called the destination. Networking - focuses on the issues involved when connecting more communication hosts together and becoming a network. ...
... Networking What are the differences? Communication - focuses on the transmission of data from one end, called the source, to another end, called the destination. Networking - focuses on the issues involved when connecting more communication hosts together and becoming a network. ...
Network
... Two levels of addressing required Each computer needs unique network address Each application on a (multi-tasking) computer needs a unique address within the computer ...
... Two levels of addressing required Each computer needs unique network address Each application on a (multi-tasking) computer needs a unique address within the computer ...
Active/Passive Voice
... The person or thing doing the action is NOT IMPORTANT or NOT KNOWN. oYour reservations are confirmed for next week. oWhen you are introduced to another person, you forget the person’s name a few minutes later. ...
... The person or thing doing the action is NOT IMPORTANT or NOT KNOWN. oYour reservations are confirmed for next week. oWhen you are introduced to another person, you forget the person’s name a few minutes later. ...
CORD Fabric, Overlay Virtualization, and Service Composition
... Finally, SR is sourcerouting, where we can change the path traffic takes through the network, by simply changing the label assignment at the source (leaf) switch there is only one switch to ‘touch’ instead of the entire ‘path’ of switches. This is how we have performed elephantflow trafficen ...
... Finally, SR is sourcerouting, where we can change the path traffic takes through the network, by simply changing the label assignment at the source (leaf) switch there is only one switch to ‘touch’ instead of the entire ‘path’ of switches. This is how we have performed elephantflow trafficen ...
William Stallings Data and Computer Communications
... Network can provide sequencing and error control Packets are forwarded more quickly No routing decisions to make ...
... Network can provide sequencing and error control Packets are forwarded more quickly No routing decisions to make ...
Basic Ingredients of Network Management
... network, it makes the devices hard to reach Also hard to find out what it happen ...
... network, it makes the devices hard to reach Also hard to find out what it happen ...
Network Address Translation (NAT)
... company maps its local inside network addresses to one or more global outside IP addresses and unmaps the global IP addresses on incoming packets back into local IP addresses. This helps ensure security since each outgoing or incoming request must go through a translation process that also offers th ...
... company maps its local inside network addresses to one or more global outside IP addresses and unmaps the global IP addresses on incoming packets back into local IP addresses. This helps ensure security since each outgoing or incoming request must go through a translation process that also offers th ...
PDF Download(PDF Type,777kbytes)
... transmission speed and optical frequency bandwidth to support diversified services with different types of traffic, such as internet, enterprise line, and mobile services. We demonstrated the reliability of EλAN through a prototype testbed network which utilizes optical path provisioning and switchi ...
... transmission speed and optical frequency bandwidth to support diversified services with different types of traffic, such as internet, enterprise line, and mobile services. We demonstrated the reliability of EλAN through a prototype testbed network which utilizes optical path provisioning and switchi ...
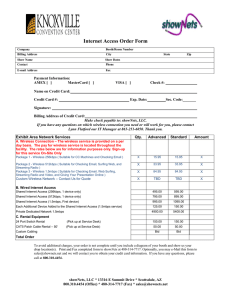
Enter through the Order/Inquire Button:
... prior to the event, connect your machine to the Cat5 cable that is installed at your location. Open a browser and enter your user id and password to access the Internet. If you order on-site, connect you machine to the Cat5 cable installed in your location. Open a browser and enter the information r ...
... prior to the event, connect your machine to the Cat5 cable that is installed at your location. Open a browser and enter your user id and password to access the Internet. If you order on-site, connect you machine to the Cat5 cable installed in your location. Open a browser and enter the information r ...
What Advantages Does an Agile Network Bring (Issue
... 1 Challenges to Enterprise Networks Brought by Social Media and Multi-Service Social media is a challenge to network capacity. Different services place different requirements on network quality. For example, the packet loss ratio of voice service should be smaller than 10-2 and that of High Definiti ...
... 1 Challenges to Enterprise Networks Brought by Social Media and Multi-Service Social media is a challenge to network capacity. Different services place different requirements on network quality. For example, the packet loss ratio of voice service should be smaller than 10-2 and that of High Definiti ...
ICN lecture1 - OSI & TCP_IP
... Agreed rules form the basis of harmonious data exchange between network nodes. These rules are referred to as protocols in the telecoms world. All telecommunications technologies are underpinned by protocols that should be recognised internationally managed by established standards bodies. A protoco ...
... Agreed rules form the basis of harmonious data exchange between network nodes. These rules are referred to as protocols in the telecoms world. All telecommunications technologies are underpinned by protocols that should be recognised internationally managed by established standards bodies. A protoco ...
Maretron NMEA 2000 Network Installation Guide
... To drop off the trunk line, you connect a device using a tee connector. Daisy-chaining of devices is not allowed, as it is a requirement to be able to remove a component from the network without affecting any other device. This allows you to remove a device for servicing while the rest of the networ ...
... To drop off the trunk line, you connect a device using a tee connector. Daisy-chaining of devices is not allowed, as it is a requirement to be able to remove a component from the network without affecting any other device. This allows you to remove a device for servicing while the rest of the networ ...
PSTN network topology

A PSTN network topology is the switching network topology of a telephone network connected to the public switched telephone network (PSTN).In the United States and Canada, the Bell System network topology was the switching system hierarchy implemented and operated from the late 1940s to the 1980s for the purpose of integrating the diverse array of local telephone companies and telephone numbering plans to achieve nationwide Direct Distance Dialing (DDD) by telephone subscribers. It was the precursor of the world-wide interconnected public switched telephone network (PSTN).The ideas originated in the Bell System in the United States, but were soon adopted by other countries where telephone operators were facing similar issues, even when service smaller geographic areas. The system in the United Kingdom implemented by the General Post Office resulted in fewer switching levels than the Bell System.