* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Managing the Digital Firm
Survey
Document related concepts
Transcript
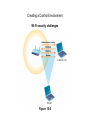
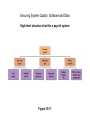
Chapter 15 Essentials of Management Information Systems, 6e Chapter 15 Information System Security and Control Information System Security and Control © 2005 by Prentice Hall Management Challenges 1. Achieving a sensible balance between too little control and too much. . 2. Applying quality assurance standards in large systems projects. System Vulnerability and Abuse Why Systems Are Vulnerable • • • • • Accessibility to electronic data Increasingly complex software, hardware Network access points Wireless vulnerability Internet System Vulnerability and Abuse Threats to Computerized Information Systems • • • • Hardware failure Software failure Personnel actions Terminal access penetration • Theft of data, services, equipment • • • • Fire Electrical problems User errors Unauthorized program changes • Telecommunication problems System Vulnerability and Abuse Telecommunications networks vulnerabilities Figure 15-1 System Vulnerability and Abuse Window on Organizations Credit Card Fraud: Still on the Rise • To what extent are Internet credit card thefts management and organizational problems, and to what extent are they technical problems? • Address the technology and management issues for both the credit card issuers and the retail companies. • Suggest possible ways to address the problem. System Vulnerability and Abuse Why Systems Are Vulnerable • • • • • • Hacker Trojan horse Denial of service (DoS) attacks Computer viruses Worms Antivirus software System Vulnerability and Abuse Window on Technology Smarter Worms and Viruses: The Worst Is Yet to Come • Why are worms so harmful? • Describe their business and organizational impact. System Vulnerability and Abuse Concerns for System Builders and Users • Disaster • Security • Administrative error • Cyberterrorism and Cyberwarfare System Vulnerability and Abuse Points in the processing cycle where errors can occur Figure 15-2 System Vulnerability and Abuse System Quality Problems: Software and Data Bugs and Defects Complete testing not possible The Maintenance Nightmare Maintenance costs high due to organizational change, software complexity, and faulty system analysis and design System Vulnerability and Abuse The cost of errors over the systems development cycle Figure 15-3 System Vulnerability and Abuse System Quality Problems: Software and Data Data Quality Problems Caused by errors during data input or faulty information system and database design Creating a Control Environment Controls • Methods, policies, and procedures • Protection of organization’s assets • Accuracy and reliability of records • Operational adherence to management standards Creating a Control Environment General Controls and Application Controls General Controls • Govern design, security, use of computer programs throughout organization • Apply to all computerized applications • Combination of hardware, software, manual procedures to create overall control environment Creating a Control Environment General Controls and Application Controls General Controls • • • • • • Software controls Hardware controls Computer operations controls Data security controls Implementation Administrative controls Creating a Control Environment Security profiles for a personnel system Figure 15-4 Creating a Control Environment General Controls and Application Controls Application Controls • Automated and manual procedures that ensure only authorized data are processed by application • Unique to each computerized application • Classified as (1) input controls, (2) processing controls, and (3) output controls. Creating a Control Environment General Controls and Application Controls Application Controls Control totals: Edit checks: Computer matching: Run control totals: Report distribution logs: Input, processing Input Input, processing Processing, output Output Creating a Control Environment Protecting the Digital Firm • • • • • • • High-availability computing Fault-tolerant computer systems Disaster recovery planning Business continuity planning Load balancing; mirroring; clustering Recovery-oriented computing Managed security service providers (MSSPs) Creating a Control Environment Protecting the Digital Firm Internet Security Challenges • Public, accessible network • Abuses have widespread effect • Fixed Internet addresses • Corporate systems extended outside organization Creating a Control Environment Internet security challenges Figure 15-5 Creating a Control Environment Protecting the Digital Firm • Firewall screening technologies • • • • Static packet filtering Stateful inspection Network address translation Application proxy filtering • Intrusion detection systems • Scanning software • Monitoring software Creating a Control Environment Protecting the Digital Firm Security and Electronic Commerce • • • • • • Encryption Authentication Message integrity Digital signatures Digital certificates Public key infrastructure (PKI) Creating a Control Environment Public key encryption Figure 15-6 Creating a Control Environment Digital certificates Figure 15-7 Creating a Control Environment Protecting the Digital Firm Security for Wireless Internet Access • Service set identifiers (SSID) – Identify access points in network – Form of password for user’s radio network interface card – Broadcast multiple time per second – Easily picked up by sniffer programs, war driving Creating a Control Environment Wi-Fi security challenges Figure 15-8 Creating a Control Environment Protecting the Digital Firm • Wired Equivalent Privacy (WEP): – Initial security standard – Call for access point and all users to share the same 40bit encrypted password • Wi-Fi Protected Access (WPA) specification – 128-bit, non-static encryption key – Data-packet checking Creating a Control Environment Developing a Control Structure: Costs and Benefits Criteria for Determining Control Structure • Importance of data • Cost effectiveness of control technique – Efficiency – Complexity – Expense • Risk assessment: Level of risk if not properly controlled – Potential frequency of problem – Potential damage Creating a Control Environment The Role of Auditing in the Control Process MIS Audit • Identifies all controls that govern individual information systems and assesses their effectiveness • Lists and ranks all control weaknesses and estimates the probability of their occurrence Creating a Control Environment Sample auditor’s list of control weaknesses Figure 15-9 Ensuring System Quality: Software and Data Software Quality Assurance Methodologies and Tools Development Methodology • Collection of methods • One or more method for every activity in every phase of development project Ensuring System Quality: Software and Data Software Quality Assurance Methodologies and Tools Structured Methodologies • • • • • Used to document, analyze, design information systems Top-down Process-oriented Linear Includes: – Structured analysis – Structured design – Structured programming Ensuring System Quality: Software and Data Software Quality Assurance Methodologies and Tools Structured Analysis • • • • • Defines system inputs, processes, outputs Logical graphic model of information flow Data flow diagram Data dictionary Process specifications Ensuring System Quality: Software and Data Data flow diagram for mail-in university registration system Figure 15-10 Ensuring System Quality: Software and Data Software Quality Assurance Methodologies and Tools Structured Design • Set of design rules and techniques • Promotes program clarity and simplicity • Design from top-down; main functions and subfunctions • Structure chart Ensuring System Quality: Software and Data High-level structure chart for a payroll system Figure 15-11 Ensuring System Quality: Software and Data Software Quality Assurance Methodologies and Tools Structured Programming • Organizes and codes programs to simplify control paths for easy use and modification • Independent modules with one entry and exit point • Three basic control constructs: – Simple sequence – Selection – Iteration Ensuring System Quality: Software and Data Basic program control constructs Figure 15-12 Ensuring System Quality: Software and Data Software Quality Assurance Methodologies and Tools Limitations of Traditional Methods • Can be inflexible and time-consuming • Programming depends on completion of analysis and design phases • Specification changes require changes in analysis and design documents first • Function-oriented Ensuring System Quality: Software and Data Software Quality Assurance Methodologies and Tools Unified Modeling Language (UML) • Industry standard for analysis and design of object-oriented systems • Represents different views using graphical diagrams • Underlying model integrates views for consistency during analysis, design, and implementation Ensuring System Quality: Software and Data Software Quality Assurance Methodologies and Tools UML Components • Things: – Structural things – Behavioral things – Grouping things – Annotational things Classes, interfaces, collaborations, use cases, active classes, components, nodes Interactions, state machines Packages Notes Ensuring System Quality: Software and Data Software Quality Assurance Methodologies and Tools UML Components • Relationships – Structural – Behavioral Dependencies, aggregations, associations, generalizations Communicates, includes, extends, generalizes • Diagrams – Structural – Behavioral Class, object, component, and deployment diagrams Use case, sequence, collaboration, stateschart, and activity diagrams Ensuring System Quality: Software and Data A UML use-case diagram Figure 15-13 Ensuring System Quality: Software and Data A UML sequence diagram Figure 15-14 Ensuring System Quality: Software and Data Software Quality Assurance Methodologies and Tools Computer-Aided Software Engineering (CASE) • • • • • • Automation of step-by-step methodologies Reduce repetitive development work Support documentation creation and revisions Organize design components; design repository Support code generation Require organizational discipline Ensuring System Quality: Software and Data Software Quality Assurance Methodologies and Tools • Resource Allocation: Assigning costs, time, personnel to different development phases • Software Metrics: Quantified measurements of systems performance • Testing: Walkthroughs, debugging Ensuring System Quality: Software and Data Data Quality Audits and Data Cleansing • Data Quality Audit – Survey end users for perceptions of data quality – Survey entire data files – Survey samples from data files • Data Cleansing – Correcting errors and inconsistencies in data between business units Chapter 15 Case Study Could a Missing Hard Drive Create Canada’s Biggest Identity Theft? 1. Summarize the ISM security problem and its impact on ISM and its clients. 2. Describe the control weaknesses of ISM and those of its clients that made it possible for this problem to occur. What management, organization, and technology factors contributed to those weaknesses? Chapter 15 Case Study Could a Missing Hard Drive Create Canada’s Biggest Identity Theft? 3. Was the disappearance of the hard drive a management problem, an organization problem, or a technical problem? Explain your answer. 4. If you were responsible for designing security at ISM and its client companies, what would you have done differently? How would you have solved their control problems?