* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Information Security
Survey
Document related concepts
Information privacy law wikipedia , lookup
Computer security wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Information security wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Do Not Track legislation wikipedia , lookup
Transcript
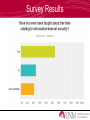
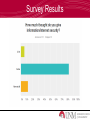
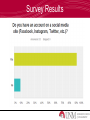
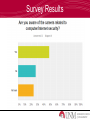
Information Security Survey Results Question What do you think Information Security is? What is Information Security? • Information Security is: – To protect the confidentiality, integrity and availability of information assets – It includes the systems and hardware that use, store, and transmit the information Survey Results Information Security in the News • Snowden NSA Leaks – Who: Edward Snowden – When: May 2013 – What: Espionage • Target Data Breach – Who: Unknown – When: December 2013 – What: Unauthorized access to credit/debit card information Why is Information Security Important? • Usage of computer/technology to store and transmit information • Increase of cybercrimes – Hacking • Securing private information • Daily use of technology and information systems How Does this Pertain to You? • Private information – Personal information • Daily use of technology – Computers/smart phones/tablets • Social networking – – – – Facebook Twitter Instagram And more! Survey Results What is Personal Information? • Personal information – Date of birth – Social security number – Passwords – Pin numbers – Addresses – Bank information – Answers to security questions • Mother’s maiden name, place of birth, etc. Question How can you protect your personal information on social networking sites? Protecting Your Information • Protecting your information – Privacy settings exist for a reason • Know how to secure information you don’t want public (i.e. pictures, personal info, school/work info, etc.) • Sensitive information on secure websites only Question Even though your privacy settings are properly set, what do you still have to be careful of on social networking sites? Privacy Settings are Properly Set but… • Privacy settings are set but you still have to be careful… – Who are your friends? • Do you know them? • Catfish – Are your Friends/Followers really who they say they are? Social Networking Sites • Accessing information is easy • Friending/following people • Information on social networking sites are searchable on search engines Social Networking Safety • • • • Don’t give out personal information Know what you’ve posted about yourself Location updates Be selective about who you accept as friends/followers • Assume everything you post is PERMANENT • Be careful about installing extras Webcams • Miss Teen USA 2013 • Laptop webcam hacked by former classmate • Hacker had as many as 150 “slave computers” • Began threatening victims How Does it Work? • RATs: Remote Administration Tools – Hackers can remotely access a person’s computer without the owner knowing – The camera light will not always be on! Question How can you make sure that no one watches you on your webcam? Choosing Strong Passwords • If your password is in the dictionary, it’s pretty much useless! – Dictionary attacks utilize software that scan a dictionary until the password is cracked • A strong password consists of – – – – – At least 8 characters Upper and lowercase letters Numbers Special characters ($, %, @, etc.) Password Generators, password cracking • If a hacker can’t crack your password within a few seconds or minutes, they will likely move on! Question What are the four components of a strong password? Survey Results Security-Related Careers • Security Crime • Federal government Investigator/Forensics • Security services Expert – Figure out how systems • Healthcare were hacked • System, Network, or Web Penetration Tester – Find vulnerabilities and test them (aka legal hacking!) • Banks • Pretty much anywhere! Technology Degrees • Information Assurance • Management Information Systems • Management of Technology • Computer Science • Computer Engineering • Cybersecurity Question Name two industries that hire people with security-related degrees Questions?