OWASP`s Ten Most Critical Web Application Security Vulnerabilities
... 2. Broken Access Control Access control is how you keep one user away from other users’ information The problem is that many environments provide authentication, but don’t handle access control well Many sites have a complex access control policy Insidiously difficult to implement correctly ...
... 2. Broken Access Control Access control is how you keep one user away from other users’ information The problem is that many environments provide authentication, but don’t handle access control well Many sites have a complex access control policy Insidiously difficult to implement correctly ...
Chapter 4
... A user may change the network address of a w/s and may make it look as another w/s A user may eavesdrop on a session and mount a replay attack later ...
... A user may change the network address of a w/s and may make it look as another w/s A user may eavesdrop on a session and mount a replay attack later ...
Red Hat Database
... accepted mechanism whereby transmissions can be protected from snooping in transit. Red Hat Database connections can also be tunneled over SSH using SSH software, such as the freely available OpenSSH implementation. This is helpful if you already have deployed SSH in your organization, as it does no ...
... accepted mechanism whereby transmissions can be protected from snooping in transit. Red Hat Database connections can also be tunneled over SSH using SSH software, such as the freely available OpenSSH implementation. This is helpful if you already have deployed SSH in your organization, as it does no ...
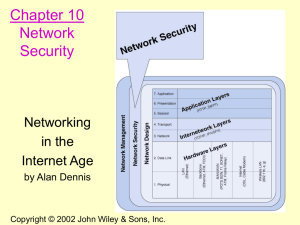
Chapter 10
... • Public key encryption: Uses two different keys, one private and one public. The keys are mathematically related so that data encrypted with one key can be decrypted using only the other key • Message integrity: The ability to be certain that the message being sent arrives at the proper destination ...
... • Public key encryption: Uses two different keys, one private and one public. The keys are mathematically related so that data encrypted with one key can be decrypted using only the other key • Message integrity: The ability to be certain that the message being sent arrives at the proper destination ...
MYDIGIPASS for Healthcare
... to secure login and fulfilment – all aspects of digital identity management are covered on a single, fully integrated platform. ...
... to secure login and fulfilment – all aspects of digital identity management are covered on a single, fully integrated platform. ...
Authentication and Remote Access
... Role-Based Access Control • Users are assigned a set of roles that they can perform. • Each role is assigned the access permissions needed to carry out its function. • Simplifies access control: people who need the same level of access are assigned to the same role, instead of having to give them al ...
... Role-Based Access Control • Users are assigned a set of roles that they can perform. • Each role is assigned the access permissions needed to carry out its function. • Simplifies access control: people who need the same level of access are assigned to the same role, instead of having to give them al ...
lesson05 - Seneca - School of Information & Communications
... reference model layer 1, which organizes data into bits, which are binary sequences of 0s and 1s used to transmit data across a wired or wireless network. – It does not perform any sort of processing against the data it receives. – Instead, it simply receives the incoming signal and recreates it for ...
... reference model layer 1, which organizes data into bits, which are binary sequences of 0s and 1s used to transmit data across a wired or wireless network. – It does not perform any sort of processing against the data it receives. – Instead, it simply receives the incoming signal and recreates it for ...
2012 Bond Planning Technology Project Update
... student use, additional software tools, and improved data analysis capabilities Significant investment in Computer & Devices Additional investment in educational technology innovation ...
... student use, additional software tools, and improved data analysis capabilities Significant investment in Computer & Devices Additional investment in educational technology innovation ...
Internet Security
... The router cannot prevent attacks that employ application-specific vulnerabilities or functions The logging functionality in the router is limited Most routers do not support advanced user authentication schemes The router is vulnerable to attacks and exploits that take advantage of flaws in ...
... The router cannot prevent attacks that employ application-specific vulnerabilities or functions The logging functionality in the router is limited Most routers do not support advanced user authentication schemes The router is vulnerable to attacks and exploits that take advantage of flaws in ...
Practice Questions with Solutions
... 14. An organization recently completed a risk assessment. Based on the findings in the risk assessment, the organization chose to purchase insurance to cover possible losses. This approach is known as: a. Risk transfer b. Risk avoidance c. Risk acceptance d. Risk reduction 15. After completing a ri ...
... 14. An organization recently completed a risk assessment. Based on the findings in the risk assessment, the organization chose to purchase insurance to cover possible losses. This approach is known as: a. Risk transfer b. Risk avoidance c. Risk acceptance d. Risk reduction 15. After completing a ri ...
Surface Balanced Magnetic Contact 1KR x 2
... The Z30 is a tough stainless steel finish, final exit switch with integral buzzer and 8 core cable, for use with all main UK Panels. It is a vandal resistant flush mounting button supplied with a mounting plate. It can be used without Face Plate if space is limited and is intended to be wired in a f ...
... The Z30 is a tough stainless steel finish, final exit switch with integral buzzer and 8 core cable, for use with all main UK Panels. It is a vandal resistant flush mounting button supplied with a mounting plate. It can be used without Face Plate if space is limited and is intended to be wired in a f ...
Irfan Ahmed Assistant Professor Department of Computer Science
... ! senses the temperature, and ! turns a heater on or off to maintain the temperature ...
... ! senses the temperature, and ! turns a heater on or off to maintain the temperature ...
Acceptable Use Policy for IT
... level of personal use of the company’s IT systems. If employees are uncertain they should consult their manager. Any information that is particularly sensitive or vulnerable must be encrypted and/or securely stored so that unauthorised access is prevented (or at least made extremely difficult). Howe ...
... level of personal use of the company’s IT systems. If employees are uncertain they should consult their manager. Any information that is particularly sensitive or vulnerable must be encrypted and/or securely stored so that unauthorised access is prevented (or at least made extremely difficult). Howe ...
Firewalls - Angelfire
... Trusted System • Data Access Control Following successful login ,the user has been granted access to one or set of hosts and applications. This is generally not sufficient for system that includes sensitive data in its database. ...
... Trusted System • Data Access Control Following successful login ,the user has been granted access to one or set of hosts and applications. This is generally not sufficient for system that includes sensitive data in its database. ...
The Top Seven Security Problems of 802.11 Wireless
... which made it instantly familiar to the large community of Ethernet LAN administrators. As 802.11 continues its ascent, though, its differences from Ethernet are becoming more apparent. Many of these differences are due to the relative unfamiliarity of many network administrators with the radio freq ...
... which made it instantly familiar to the large community of Ethernet LAN administrators. As 802.11 continues its ascent, though, its differences from Ethernet are becoming more apparent. Many of these differences are due to the relative unfamiliarity of many network administrators with the radio freq ...
Presentation4 - University Of Worcester
... When a user first attempts to communicate with a web server over a secure connection: that server will present the web browser with authentication data presented as a server certificate (remember ...
... When a user first attempts to communicate with a web server over a secure connection: that server will present the web browser with authentication data presented as a server certificate (remember ...
Chapter 1. Introduction to Data Communications
... network resources a user can access and the type of access (e.g., read, write, create, delete). • Most access is still password based, that is, users gain access based on something they know. • Many systems require users to enter a password in conjunction with something they have, such as a smart ca ...
... network resources a user can access and the type of access (e.g., read, write, create, delete). • Most access is still password based, that is, users gain access based on something they know. • Many systems require users to enter a password in conjunction with something they have, such as a smart ca ...
Network File System (NFS)
... protocol is ubiquitous and supported generally by every UNIX-like variant, as well as being supported by operating systems by Microsoft and Apple. The system provides a system for permission management, as well as user and role-based access controls. The protocol dates itself to the 1980’s, with the ...
... protocol is ubiquitous and supported generally by every UNIX-like variant, as well as being supported by operating systems by Microsoft and Apple. The system provides a system for permission management, as well as user and role-based access controls. The protocol dates itself to the 1980’s, with the ...
Design and Implementation of Security Operating System based on
... Analyzes and reviews relative work of security ...
... Analyzes and reviews relative work of security ...
Cybersecurity for Critical Control Systems in the Power Industry
... Authentication for dial-up connectivity and a documented process for how this authentication is achieved. ...
... Authentication for dial-up connectivity and a documented process for how this authentication is achieved. ...
Enhanced Security Models for Operating Systems: A Cryptographic
... Strong security : Vaults provide a strong security baseline similar to mandatory security features in trusted system. Vaults implements Trusted finger print mechanism. Flexible and Intuitive security: Providing more flexibility by offering own security ...
... Strong security : Vaults provide a strong security baseline similar to mandatory security features in trusted system. Vaults implements Trusted finger print mechanism. Flexible and Intuitive security: Providing more flexibility by offering own security ...
- SlideBoom
... In which two situations should you use out-of-band management? (Choose two.) A. B. C. D. E. ...
... In which two situations should you use out-of-band management? (Choose two.) A. B. C. D. E. ...
Secure External Network Communications
... (TCP/IP) architecture and its internal addressing and protocol components. The router becomes the external filter, and the dial-up access control management system provides for secure individual authentication through the implementation of smart-card technology using challenge-response devices. Whil ...
... (TCP/IP) architecture and its internal addressing and protocol components. The router becomes the external filter, and the dial-up access control management system provides for secure individual authentication through the implementation of smart-card technology using challenge-response devices. Whil ...
DCRS-5750F Dual Stack Ethernet Switch Datasheet Product Overview
... The Digital China DCRS-5750F series switches are 10G dual stack full optical Ethernet Layer 3 switch. There are 2 types switch for this family. The product family include DCRS-5750-28F DCRS-5750-52F. All products support IPv6 with hardware and pass the IPv6 form certification Phase II. All products ...
... The Digital China DCRS-5750F series switches are 10G dual stack full optical Ethernet Layer 3 switch. There are 2 types switch for this family. The product family include DCRS-5750-28F DCRS-5750-52F. All products support IPv6 with hardware and pass the IPv6 form certification Phase II. All products ...
Access control
_before_allowing_a_driver_to_enter_the_gate_at_U.S._Fleet_Activities_Sasebo,_Japan.jpg?width=300)
In the fields of physical security and information security, access control is the selective restriction of access to a place or other resource. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.Locks and login credentials are two analogous mechanisms of access control.