monitor
... • Control Framework: A control framework is a set of controls that protects data within the IT infrastructure of a business or other entity. • Framework: an arrangement of parts that provides a form, or structure, to the whole. ...
... • Control Framework: A control framework is a set of controls that protects data within the IT infrastructure of a business or other entity. • Framework: an arrangement of parts that provides a form, or structure, to the whole. ...
Avaya™ G700 Media Gateway Security - Issue 1.0
... 5) Firewalls and Routers that implement, and are managed by, an SNMPv3-based network management system are recommended (vs. SNMPv1 or SNMPv2) because the security of SNMPv3 can prevent unauthorized updates to the routing tables and access control list by an intruder. Layer 2 switches are preferred t ...
... 5) Firewalls and Routers that implement, and are managed by, an SNMPv3-based network management system are recommended (vs. SNMPv1 or SNMPv2) because the security of SNMPv3 can prevent unauthorized updates to the routing tables and access control list by an intruder. Layer 2 switches are preferred t ...
Top-Ten Web Security Vulnerabilities
... Security Features = Secure Features ??? Security features do not necessarily make for a secure application. ...
... Security Features = Secure Features ??? Security features do not necessarily make for a secure application. ...
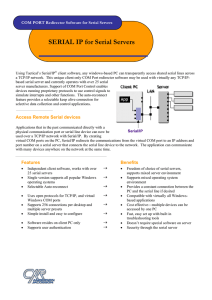
SERIAL-IP COM PORT Redirector Software for Serial Servers
... Using Tactical’s Serial/IP® client software, any windows-based PC can transparently access shared serial lines across a TCP/IP network. This unique client only COM Port redirector software may be used with virtually any TCP/IPbased serial server and currently operates with over 25 serial server manu ...
... Using Tactical’s Serial/IP® client software, any windows-based PC can transparently access shared serial lines across a TCP/IP network. This unique client only COM Port redirector software may be used with virtually any TCP/IPbased serial server and currently operates with over 25 serial server manu ...
ppt 2
... • Once the request is verified • the monitor module records non-secure states • then switches monitoring sessions to trusted zone • Like a context switch • The monitor module protects data in the trusted zone from infiltrating into normal zone • This is all achieved by hardware, not the OS • TrustZo ...
... • Once the request is verified • the monitor module records non-secure states • then switches monitoring sessions to trusted zone • Like a context switch • The monitor module protects data in the trusted zone from infiltrating into normal zone • This is all achieved by hardware, not the OS • TrustZo ...
Ingen bildrubrik
... Integrated Abloy 8164 NetLock interface Integrated Ethernet interface Integrated FT/10 LonWorks® field bus Integrated X10 interface Integrated GSM/GPRS module for SMS messaging and host communication Integrated backup power - up to 60 hours ...
... Integrated Abloy 8164 NetLock interface Integrated Ethernet interface Integrated FT/10 LonWorks® field bus Integrated X10 interface Integrated GSM/GPRS module for SMS messaging and host communication Integrated backup power - up to 60 hours ...
Document
... HS usually does not have the user interface , AG will control some of the basic settings of HS (e.g volume setting, changing the passkey). The pairing will only succeed if only the AG knows the correct pass-key of HS. If the HS is stolen , the thief will not know the pass-key and will not succeed to ...
... HS usually does not have the user interface , AG will control some of the basic settings of HS (e.g volume setting, changing the passkey). The pairing will only succeed if only the AG knows the correct pass-key of HS. If the HS is stolen , the thief will not know the pass-key and will not succeed to ...
Do`s and Don`ts for web application developers
... 1.Rely on client-side data validation. 2.Trust anything a user or other process sends to ...
... 1.Rely on client-side data validation. 2.Trust anything a user or other process sends to ...
Security Architecture - Department of Computer Science
... To reduce the apparent main memory access time Volatile: data is lost if power is off ...
... To reduce the apparent main memory access time Volatile: data is lost if power is off ...
Cyber Security Education Consortium 2008 Retreat
... • Experts seeing increased interest in Control Systems by terrorists & foreign governments • Evidence that nation-states have been taking remote control of Control Systems • Denial by some companies that there is a problem • Some companies are now starting to see the need and address the issues ...
... • Experts seeing increased interest in Control Systems by terrorists & foreign governments • Evidence that nation-states have been taking remote control of Control Systems • Denial by some companies that there is a problem • Some companies are now starting to see the need and address the issues ...
Lecture 8 - Bhecker.com
... • Public key encryption: Uses two different keys, one private and one public. The keys are mathematically related so that data encrypted with one key can be decrypted using only the other key • Message integrity: The ability to be certain that the message being sent arrives at the proper destination ...
... • Public key encryption: Uses two different keys, one private and one public. The keys are mathematically related so that data encrypted with one key can be decrypted using only the other key • Message integrity: The ability to be certain that the message being sent arrives at the proper destination ...
Symbolic Honeynets for Gathering Cyber
... Vulnerabilities are indicated by “ “ and involve physical/human/cyber entities. For example: the Remote Operator or their computer may be compromised, the behavior of the Relay or the Merge Unit Brick may be irregular (because of unexpected inputs), etc. Our goal is to: ...
... Vulnerabilities are indicated by “ “ and involve physical/human/cyber entities. For example: the Remote Operator or their computer may be compromised, the behavior of the Relay or the Merge Unit Brick may be irregular (because of unexpected inputs), etc. Our goal is to: ...
Addressing security threats and vulnerabilities
... • Availability – Ensures that information and equipment can be used only by those who are authorized to do so • C-I-A triad – Trade-offs ...
... • Availability – Ensures that information and equipment can be used only by those who are authorized to do so • C-I-A triad – Trade-offs ...
Network Security (Daliah Stephan).
... your wireless network is practically invisible when SSID broadcasting is disabled. • When you disable broadcasting, you must configure each wireless client with the exact name of the ...
... your wireless network is practically invisible when SSID broadcasting is disabled. • When you disable broadcasting, you must configure each wireless client with the exact name of the ...
Chapter 5 Protection of Information Assets
... Best practices for logon IDs and passwords • Passwords should be a minimum of 8 characters • Passwords should be a combination of alpha, numeric, upper and lower case and special ...
... Best practices for logon IDs and passwords • Passwords should be a minimum of 8 characters • Passwords should be a combination of alpha, numeric, upper and lower case and special ...
Cyber Solutions for NEI 08-09 Whitepaper 119 KB
... The SecurityST Active Directory user and management functions can be used to limit functions for operators while enabling security functions for administrative users only. There is physical partitioning in the network levels between the Control Network (UDH) and the Supervisory Network (PDH). In add ...
... The SecurityST Active Directory user and management functions can be used to limit functions for operators while enabling security functions for administrative users only. There is physical partitioning in the network levels between the Control Network (UDH) and the Supervisory Network (PDH). In add ...
Operating System Security Fundamentals
... Authentication Methods (continued) Digital certificates: digital passport that identifies and verifies holder of certificate Digital token (security token): Small electronic device Displays a number unique to the token holder; used with the holder’s PIN as a password Uses a different password each ...
... Authentication Methods (continued) Digital certificates: digital passport that identifies and verifies holder of certificate Digital token (security token): Small electronic device Displays a number unique to the token holder; used with the holder’s PIN as a password Uses a different password each ...
TEL2813/IS2820 Security Management
... All Internet Control Message Protocol (ICMP) data should be denied Telnet (terminal emulation) access to all internal servers from the public networks should be blocked When Web services are offered outside the firewall, HTTP traffic should be handled by some form of proxy access or DMZ architecture ...
... All Internet Control Message Protocol (ICMP) data should be denied Telnet (terminal emulation) access to all internal servers from the public networks should be blocked When Web services are offered outside the firewall, HTTP traffic should be handled by some form of proxy access or DMZ architecture ...
slides
... Only the owner can grant/revoke read access to/from other users. The creator is the owner of the object. Membership of the three administrative roles cannot change. This policy can be enforced by imposing a cardinality constraint of 1 on OWN_O and of 0 on PARENT_O and PARENTwithGRANT_O. This policy ...
... Only the owner can grant/revoke read access to/from other users. The creator is the owner of the object. Membership of the three administrative roles cannot change. This policy can be enforced by imposing a cardinality constraint of 1 on OWN_O and of 0 on PARENT_O and PARENTwithGRANT_O. This policy ...
Securing Distribution Automation
... management, to our knowledge there are none that have been designed to meet the requirements of distributed field devices. Typical enterprise password management systems are designed to support devices such as routers and switches on standard enterprise networks. They generally are not designed to m ...
... management, to our knowledge there are none that have been designed to meet the requirements of distributed field devices. Typical enterprise password management systems are designed to support devices such as routers and switches on standard enterprise networks. They generally are not designed to m ...
Slide 1
... Facial geometry identifies a user based on the profile and characteristics of the face. A retina scan identifies an individual by using the blood vessel pattern at the back of the eyeball. A retinal scan is a very secure form of evidence used in high-security companies and government agencies. Whe ...
... Facial geometry identifies a user based on the profile and characteristics of the face. A retina scan identifies an individual by using the blood vessel pattern at the back of the eyeball. A retinal scan is a very secure form of evidence used in high-security companies and government agencies. Whe ...
Lecture1
... this protocol. Its designers aimed primarily at a client–server model, and it provides mutual authentication — both the user and the server verify each other's identity. Kerberos protocol messages are protected against eavesdropping and replay attacks. 0 Kerberos builds on symmetric key cryptography ...
... this protocol. Its designers aimed primarily at a client–server model, and it provides mutual authentication — both the user and the server verify each other's identity. Kerberos protocol messages are protected against eavesdropping and replay attacks. 0 Kerberos builds on symmetric key cryptography ...
PowerPoint Presentation - IF-MAP
... – Faster response = stronger security – Less expense due to automation ...
... – Faster response = stronger security – Less expense due to automation ...
Access control
_before_allowing_a_driver_to_enter_the_gate_at_U.S._Fleet_Activities_Sasebo,_Japan.jpg?width=300)
In the fields of physical security and information security, access control is the selective restriction of access to a place or other resource. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.Locks and login credentials are two analogous mechanisms of access control.