Chapter 24 - William Stallings, Data and Computer
... is a driving need for users and organizations to be able to: ...
... is a driving need for users and organizations to be able to: ...
Fundamentals of Computer Security
... constitute the largest threat to the computer systems security[2]. Traditional methods (such as identification and authentication, access restriction, etc.) do not solve this problem Drawbacks; among them are ...
... constitute the largest threat to the computer systems security[2]. Traditional methods (such as identification and authentication, access restriction, etc.) do not solve this problem Drawbacks; among them are ...
Workstar iGuard
... fingerprint verification (such as after office hours or during weekends and holidays). 2. Access Rights: When you can easily and conveniently assign different access rights to your employees, you can plan your security better and maximize the effectiveness of the human resources . And with the built ...
... fingerprint verification (such as after office hours or during weekends and holidays). 2. Access Rights: When you can easily and conveniently assign different access rights to your employees, you can plan your security better and maximize the effectiveness of the human resources . And with the built ...
Protecting Valuable Physical Assets in a High Traffic Setting
... locks and all employees have been issued keys. The system has been in place for 18 months now and we're very happy with it. We have plans to build the system out to include perimeter ...
... locks and all employees have been issued keys. The system has been in place for 18 months now and we're very happy with it. We have plans to build the system out to include perimeter ...
Security Considerations for Health Care Organizations
... Presentation is for educational purposes only and does not constitute legal advice. If you require legal advice, you should consult with an attorney. ...
... Presentation is for educational purposes only and does not constitute legal advice. If you require legal advice, you should consult with an attorney. ...
Operating System Security
... fewest objects needed for successful work – The system backup program may be allowed to bypass read restrictions on files, but it would not have the ability to modify files. – Need to Know” ...
... fewest objects needed for successful work – The system backup program may be allowed to bypass read restrictions on files, but it would not have the ability to modify files. – Need to Know” ...
it user svq – level 2
... Know what type of security breaches can occur at work: o Unauthorised use of a system without damage to data; o Unauthorised removal or copying of data or code from a system; o Damage to or destruction of physical system assets and environment; o Damage to or destruction of data or code inside or ou ...
... Know what type of security breaches can occur at work: o Unauthorised use of a system without damage to data; o Unauthorised removal or copying of data or code from a system; o Damage to or destruction of physical system assets and environment; o Damage to or destruction of data or code inside or ou ...
Security strategy
... information technology assets. This will cover the physical configuration, software, and information handling and user practices. All organisations suffer from breaches of security. These can range from innocent attempts to access restricted resources to deliberate and prolonged attempts on computer ...
... information technology assets. This will cover the physical configuration, software, and information handling and user practices. All organisations suffer from breaches of security. These can range from innocent attempts to access restricted resources to deliberate and prolonged attempts on computer ...
Network Access Control
... or "robot," is a program that is installed by an intruder, so that the machine takes actions automatically, as programmed by the intruder and at times specified by the intruder who put the bot there. Date (Timezone=UTC) ...
... or "robot," is a program that is installed by an intruder, so that the machine takes actions automatically, as programmed by the intruder and at times specified by the intruder who put the bot there. Date (Timezone=UTC) ...
A threat can be any person, object, or event that, if realized, could
... networks from authorized network users, inadvertently opening doors for intruders. Incorrectly configured APs: Radio waves broadcast by wireless base stations are relatively powerful, and residential neighbors or adjacent businesses may connect to each other's wireless networks. Many APs are initial ...
... networks from authorized network users, inadvertently opening doors for intruders. Incorrectly configured APs: Radio waves broadcast by wireless base stations are relatively powerful, and residential neighbors or adjacent businesses may connect to each other's wireless networks. Many APs are initial ...
Document
... (hardware token) in addition to something you know (username + password) Over 1700 employees currently using ArchPass to access these systems ...
... (hardware token) in addition to something you know (username + password) Over 1700 employees currently using ArchPass to access these systems ...
William Stallings, Cryptography and Network Security 3/e
... • use an application specific gateway / proxy • has full access to protocol – user requests service from proxy – proxy validates request as legal – then actions request and returns result to user ...
... • use an application specific gateway / proxy • has full access to protocol – user requests service from proxy – proxy validates request as legal – then actions request and returns result to user ...
CH04-CompSec2e - MCST-CS
... Access Control Requirements reliable input support for fine and coarse specifications least privilege separation of duty open and closed policies policy combinations and conflict resolution administrative policies dual control ...
... Access Control Requirements reliable input support for fine and coarse specifications least privilege separation of duty open and closed policies policy combinations and conflict resolution administrative policies dual control ...
LSD1518 - Control Cloud Data Access Privilege
... schemes based on the attribute-based encryption have been proposed to secure the cloud storage. However, most work focuses on the data contents privacy and the access control, while less attention is paid to the privilege control and the identity privacy. In this paper, we present a semi-anonymous p ...
... schemes based on the attribute-based encryption have been proposed to secure the cloud storage. However, most work focuses on the data contents privacy and the access control, while less attention is paid to the privilege control and the identity privacy. In this paper, we present a semi-anonymous p ...
Network Security Overview
... Reconnaissance is the unauthorized discovery and mapping of systems, services, or vulnerabilities. It is also called information gathering. In most cases, it precedes an actual access or DoS attack. The malicious intruder typically ping-sweeps the target network first to determine what IP addresses ...
... Reconnaissance is the unauthorized discovery and mapping of systems, services, or vulnerabilities. It is also called information gathering. In most cases, it precedes an actual access or DoS attack. The malicious intruder typically ping-sweeps the target network first to determine what IP addresses ...
business computer and network check list
... from temporary files. It does not have unnecessary programs slowing it down . The internet connection is reliable and does not go down I have a second internet connection for 100% up time I have clean power. Power surges and sudden outages will not damage my servers and essential network equipment. ...
... from temporary files. It does not have unnecessary programs slowing it down . The internet connection is reliable and does not go down I have a second internet connection for 100% up time I have clean power. Power surges and sudden outages will not damage my servers and essential network equipment. ...
IT ESSENTIALS V. 4.1 Module 9 Fundamental Security 9.1 Explain
... Which wireless security protocol was created by Cisco? What do virus, spyware, and adware detection programs look for? What are the code patterns called? ...
... Which wireless security protocol was created by Cisco? What do virus, spyware, and adware detection programs look for? What are the code patterns called? ...
Identity-Based Security
... Aruba’s identity-based security solution dramatically improves network security by eliminating excess privilege on the network while also providing identity-based auditing of activity. Traditional fixed networks can only apply access rights to ports or VLANs. Mobile users and devices, by definition, ...
... Aruba’s identity-based security solution dramatically improves network security by eliminating excess privilege on the network while also providing identity-based auditing of activity. Traditional fixed networks can only apply access rights to ports or VLANs. Mobile users and devices, by definition, ...
SO 2.4.4 - Broadband for all
... notably for the enlarged Europe in line with the eEurope objectives. - a European consolidated approach for standardized solutions, regulation, best practices and introduction of low-cost end user and access network equipment. ...
... notably for the enlarged Europe in line with the eEurope objectives. - a European consolidated approach for standardized solutions, regulation, best practices and introduction of low-cost end user and access network equipment. ...
View File
... • use an application specific gateway / proxy • has full access to protocol – user requests service from proxy – proxy validates request as legal – then actions request and returns result to user ...
... • use an application specific gateway / proxy • has full access to protocol – user requests service from proxy – proxy validates request as legal – then actions request and returns result to user ...
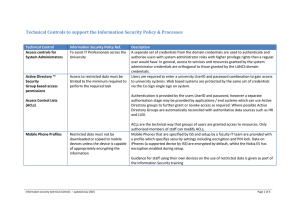
Technical Controls to support the Information
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
L16_Security
... • An unauthorized party not only gains access but tampers with an asset • Changing values in a data file • Altering a program so that it performs differently • Modifying the content of messages being transmitted in a network ...
... • An unauthorized party not only gains access but tampers with an asset • Changing values in a data file • Altering a program so that it performs differently • Modifying the content of messages being transmitted in a network ...
Access control
_before_allowing_a_driver_to_enter_the_gate_at_U.S._Fleet_Activities_Sasebo,_Japan.jpg?width=300)
In the fields of physical security and information security, access control is the selective restriction of access to a place or other resource. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization.Locks and login credentials are two analogous mechanisms of access control.