Looking into Windows
... they are no longer able to satisfy compliance requirements if they remain with W indows XP. With so much personal and private data now stored on servers, data security is a very significant concern. Lack of independent software vendor support Many software vendors no longer support their products t ...
... they are no longer able to satisfy compliance requirements if they remain with W indows XP. With so much personal and private data now stored on servers, data security is a very significant concern. Lack of independent software vendor support Many software vendors no longer support their products t ...
Computer Ethics
... available only to those who rightfully have access to it •Integrity -- information should be modified only by those who are authorized to do so •Availability -- information should be accessible to those who need it when they need it ...
... available only to those who rightfully have access to it •Integrity -- information should be modified only by those who are authorized to do so •Availability -- information should be accessible to those who need it when they need it ...
Antivirus Software
... Limit access to services that are not disabled Use a firewall if you’re connected to the Internet Disable networking protocols that are not used Review services related to remote access and networking, and remove any that are non-essential ...
... Limit access to services that are not disabled Use a firewall if you’re connected to the Internet Disable networking protocols that are not used Review services related to remote access and networking, and remove any that are non-essential ...
PROTECTING INFORMATION RESOURCES
... • Provides a secure “tunnel” through the Internet – For transmitting messages and data via a private network ...
... • Provides a secure “tunnel” through the Internet – For transmitting messages and data via a private network ...
Security Architectures
... – Does not address confidentiality – Does not address control management nor provide a way to change classification levels ...
... – Does not address confidentiality – Does not address control management nor provide a way to change classification levels ...
PowerPoint
... The file system browser of a computer functions virtually the same, regardless of whether you are using a PC or a Mac. ...
... The file system browser of a computer functions virtually the same, regardless of whether you are using a PC or a Mac. ...
security
... – Key security: steal the key and the code can be broken – Every time the key is transferred there is risk of it being intercepted – The same key may be shared by too many people ...
... – Key security: steal the key and the code can be broken – Every time the key is transferred there is risk of it being intercepted – The same key may be shared by too many people ...
Applied Cybersecurity
... The majority of the course (about 75%) is geared toward participants at the decision-making level who need a broad overview, rather than those who are already deeply immersed in the technical aspects of cybersecurity (software development, digital forensics, etc.), although both groups will find the ...
... The majority of the course (about 75%) is geared toward participants at the decision-making level who need a broad overview, rather than those who are already deeply immersed in the technical aspects of cybersecurity (software development, digital forensics, etc.), although both groups will find the ...
Quality Attributes of Web Software Applications – Jeff Offutt
... Most of the software now resides on separate computers rather than the web server Client -> web server -> application ...
... Most of the software now resides on separate computers rather than the web server Client -> web server -> application ...
doc - RPI
... access to a valid user’s account and acts disruptively, Dr. Szymanski uses probabilistic state finite automata (PSFA), mathematical models of computations augmented with probabilities. They detect anomalies, or variations from the norm. The system stores information about the normal user’s frequent ...
... access to a valid user’s account and acts disruptively, Dr. Szymanski uses probabilistic state finite automata (PSFA), mathematical models of computations augmented with probabilities. They detect anomalies, or variations from the norm. The system stores information about the normal user’s frequent ...
Security Considerations for Health Care Organizations
... Presentation is for educational purposes only and does not constitute legal advice. If you require legal advice, you should consult with an attorney. ...
... Presentation is for educational purposes only and does not constitute legal advice. If you require legal advice, you should consult with an attorney. ...
Chapter 1 THE INFORMATION AGE IN WHICH YOU LIVE Changing
... removes or quarantines computer viruses 2. Anti-spyware and anti-adware software 3. Spam protection software – identifies and marks and/or deletes Spam 4. Anti-phishing software – lets you know when phishing attempts are being made 5. Firewall – hardware and/or software that protects a computer or n ...
... removes or quarantines computer viruses 2. Anti-spyware and anti-adware software 3. Spam protection software – identifies and marks and/or deletes Spam 4. Anti-phishing software – lets you know when phishing attempts are being made 5. Firewall – hardware and/or software that protects a computer or n ...
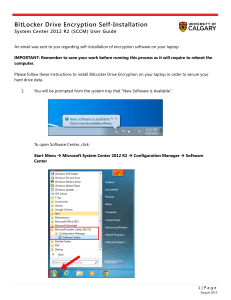
BitLocker Drive Encryption Self
... System Center 2012 R2 (SCCM) User Guide An email was sent to you regarding self-installation of encryption software on your laptop. IMPORTANT: Remember to save your work before running this process as it will require to reboot the computer. Please follow these instructions to install BitLocker Drive ...
... System Center 2012 R2 (SCCM) User Guide An email was sent to you regarding self-installation of encryption software on your laptop. IMPORTANT: Remember to save your work before running this process as it will require to reboot the computer. Please follow these instructions to install BitLocker Drive ...
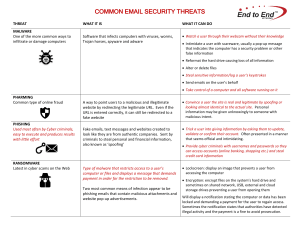
COMMON EMAIL SECURITY THREATS
... locked and demanding a payment for the user to regain access. Sometimes the notification states that authorities have detected illegal activity and the payment is a fine to avoid prosecution. ...
... locked and demanding a payment for the user to regain access. Sometimes the notification states that authorities have detected illegal activity and the payment is a fine to avoid prosecution. ...
Implementing Security for Electronic Commerce
... IN case of downloaded software containing a digital ID, it identifies the software publisher, i.e., it assures that the holder of the software is a trusted name. A certification authority (CA) issues a digital certificate to an organization or an individual when provided with required information. A ...
... IN case of downloaded software containing a digital ID, it identifies the software publisher, i.e., it assures that the holder of the software is a trusted name. A certification authority (CA) issues a digital certificate to an organization or an individual when provided with required information. A ...
Security and Ethical Challenges
... The IT executives in the case all note that outbound monitoring and management technologies are only part of an overall strategy, and not their primary defense – What should the other components of this strategy be? – Which weight would you give to human and technological factors? ...
... The IT executives in the case all note that outbound monitoring and management technologies are only part of an overall strategy, and not their primary defense – What should the other components of this strategy be? – Which weight would you give to human and technological factors? ...
A Technical Introduction to NGSCB Security Summit East 2003
... The machine owner sets policy to control which forms of attestation each agent or group of agents can use Secure communications agent provides higher-level services to agent developers Open a secure channel to a service using a secure session key Respond to an attestation challenge from the service ...
... The machine owner sets policy to control which forms of attestation each agent or group of agents can use Secure communications agent provides higher-level services to agent developers Open a secure channel to a service using a secure session key Respond to an attestation challenge from the service ...
small business software
... ARTECO-SERVER Small Business is compatible with ONVIF ™ devices and integrates hundreds of cameras from the leading brands on the market. The system can view live/recorded video, as well as analyze video from cameras in full Megapixel resolution. It supports the most advanced encoding: H.264, MJPEG, ...
... ARTECO-SERVER Small Business is compatible with ONVIF ™ devices and integrates hundreds of cameras from the leading brands on the market. The system can view live/recorded video, as well as analyze video from cameras in full Megapixel resolution. It supports the most advanced encoding: H.264, MJPEG, ...
... POIT does not assume any liability for a user’s personally owned computer/device. Users must install all software themselves on their computer/device. POIT can only help configure software after the software is installed and working normally. POIT cannot assume liability for installing software on p ...
Form 140-1
... Think always of your own personal safety. Protect your privacy, as well as the privacy of others. ...
... Think always of your own personal safety. Protect your privacy, as well as the privacy of others. ...
http://www.facebook.com/ManagedServiceE Twitter
... analyse multiple alternatives, such as in a chess game. Grid computing appears promising for three reasons: 1. The ability to make cost-effective use of a defined amount of computer resources. 2. As a means of solving problems that can only be approached with an enormous amount of computing power. 3 ...
... analyse multiple alternatives, such as in a chess game. Grid computing appears promising for three reasons: 1. The ability to make cost-effective use of a defined amount of computer resources. 2. As a means of solving problems that can only be approached with an enormous amount of computing power. 3 ...
Fundamentals of Computer Security
... Client/Server Security A client initiates an access to an object through the ...
... Client/Server Security A client initiates an access to an object through the ...