Final bits of OS - Department of Computer Science
... • Hardware included on most commercial chips these days • Used by many systems and applications: ...
... • Hardware included on most commercial chips these days • Used by many systems and applications: ...
Designing Trusted Operating Systems Operating Systems
... Chapter 5 – Designing Trusted Operating Systems ...
... Chapter 5 – Designing Trusted Operating Systems ...
Information Security in Real Business
... Configured Software is Downloaded from Ford Installed on Cars for Diagnostic Testing ...
... Configured Software is Downloaded from Ford Installed on Cars for Diagnostic Testing ...
Computer Systems Security
... Originally, backdoors were used by developers as a legitimate way of accessing an application, but soon after they were implemented by attackers who would use backdoors to make changes to operating systems, websites, and network devices Quite often, it is installed via a Trojan horse ...
... Originally, backdoors were used by developers as a legitimate way of accessing an application, but soon after they were implemented by attackers who would use backdoors to make changes to operating systems, websites, and network devices Quite often, it is installed via a Trojan horse ...
Windows XP - British Columbia Institute of Technology
... • Processor runs one process for short period of time, then switches to next process, and so on… (pre-emptive) – As processor executes billions of instructions per second, it appears many processes are running at same time. – With multi-core processors this becomes even easier ...
... • Processor runs one process for short period of time, then switches to next process, and so on… (pre-emptive) – As processor executes billions of instructions per second, it appears many processes are running at same time. – With multi-core processors this becomes even easier ...
Word
... Provides the interface for storage devices and _____________________________________ on those devices - in charge of formatting disks - creates sectors and clusters - creates F.A.T. or V.T.O.C. - sends message when disk is full or there is some other problem with writing data to the disk ...
... Provides the interface for storage devices and _____________________________________ on those devices - in charge of formatting disks - creates sectors and clusters - creates F.A.T. or V.T.O.C. - sends message when disk is full or there is some other problem with writing data to the disk ...
Operating Systems - Personal Web Server
... execution environments for applications for other operating systems. Portability It means that the operating system can be ported to a variety of different machines Robustness It means that the ideal operating system can provide protection from accidental or deliberate damage by user programme U ...
... execution environments for applications for other operating systems. Portability It means that the operating system can be ported to a variety of different machines Robustness It means that the ideal operating system can provide protection from accidental or deliberate damage by user programme U ...
Detecting drive-by-downloads using human
... Most approaches to detecting drive-bydownloads focus only on server-side solutions or browser security We can use the user’s input to validate each download when it occurs ...
... Most approaches to detecting drive-bydownloads focus only on server-side solutions or browser security We can use the user’s input to validate each download when it occurs ...
security_6
... cyber-criminals who use email, popup messages or an imitation or copy of an existing legitimate webpage to trick users into providing sensitive personal information such as credit card numbers, bank account numbers, and passwords. ...
... cyber-criminals who use email, popup messages or an imitation or copy of an existing legitimate webpage to trick users into providing sensitive personal information such as credit card numbers, bank account numbers, and passwords. ...
Tobias Herber (530) 723-6691
... - Created custom solution for legacy apps using Windows XP Mode - Set up IT infrastructure in new building, including a dual server rack, 12 physical servers, patch panel, managed/unmanaged switches, UPS, NAS, and wireless AP's September 2012 – June 2013 Computer Pros of Malibu, LLC Repair Technicia ...
... - Created custom solution for legacy apps using Windows XP Mode - Set up IT infrastructure in new building, including a dual server rack, 12 physical servers, patch panel, managed/unmanaged switches, UPS, NAS, and wireless AP's September 2012 – June 2013 Computer Pros of Malibu, LLC Repair Technicia ...
URL-Encoded Form Data is Not Valid Error
... Note: At this time, Software Answers is recommending 6, 000 as the setting. This 6,000 setting should not expose the vulnerability Microsoft has corrected and should allow screens with large amounts of data to save without error. Although we are recommending 6,000, it may be necessary for some custo ...
... Note: At this time, Software Answers is recommending 6, 000 as the setting. This 6,000 setting should not expose the vulnerability Microsoft has corrected and should allow screens with large amounts of data to save without error. Although we are recommending 6,000, it may be necessary for some custo ...
Basic Marketing, 16e
... your own personal possessions, and not to be observed without your consent Dimensions of privacy ...
... your own personal possessions, and not to be observed without your consent Dimensions of privacy ...
IT ESSENTIALS V. 4.1 Module 9 Fundamental Security 9.1 Explain
... Escort all visitors Lock your computer when you leave your desk Do not let anyone follow you through a door that requires an access card Randomly opens TCP ports, typing up network equipment with large amount of false requests, causing sessions to be denied to others Gains access to resources on dev ...
... Escort all visitors Lock your computer when you leave your desk Do not let anyone follow you through a door that requires an access card Randomly opens TCP ports, typing up network equipment with large amount of false requests, causing sessions to be denied to others Gains access to resources on dev ...
System Administration
... Hardware and Software as Infrastructure Capital resources are referred to as infrastructure and have the following characteristics: – Service to a large and diverse set of users. – Costs that are difficult t allocate to individual users. – Recurring need for new capital expenditures. – Significant ...
... Hardware and Software as Infrastructure Capital resources are referred to as infrastructure and have the following characteristics: – Service to a large and diverse set of users. – Costs that are difficult t allocate to individual users. – Recurring need for new capital expenditures. – Significant ...
Input- any data or instructions entered into the memory of a computer
... Input- any data or instructions entered into the memory of a computer. Input consists of either data or instructions. Instructions can be in the form of: programs-series of instructions which tells a computer what to do, commands- users issue commands and user responses- an instruction a user issues ...
... Input- any data or instructions entered into the memory of a computer. Input consists of either data or instructions. Instructions can be in the form of: programs-series of instructions which tells a computer what to do, commands- users issue commands and user responses- an instruction a user issues ...
Design and Implementation of Security Operating System based on
... Classical security model BLP is improved to get IBLP. The overall design scheme and modularized implementation of a secure system for trusted computing. Experiment result to show effectiveness and feasibility of their system. ...
... Classical security model BLP is improved to get IBLP. The overall design scheme and modularized implementation of a secure system for trusted computing. Experiment result to show effectiveness and feasibility of their system. ...
ROOTKIT VIRUS
... system in order to conceal the altering of files, or processes being executed by the third party without the user's knowledge. ...
... system in order to conceal the altering of files, or processes being executed by the third party without the user's knowledge. ...
JRA1.4 AAs in eduGAIN
... with existing architectures (to simplify technical adoption of such a solution by all the participants to the federation). ● Leverage the existing federations in building the reciprocal trust, needed to guarantee security. ...
... with existing architectures (to simplify technical adoption of such a solution by all the participants to the federation). ● Leverage the existing federations in building the reciprocal trust, needed to guarantee security. ...
UAE Online Child Safety Awareness Campaign
... person and ask permission before going Think before you post, the Internet never forgets… Be protective of your personal information Trustworthy Computing ...
... person and ask permission before going Think before you post, the Internet never forgets… Be protective of your personal information Trustworthy Computing ...
E-Surveillance and User Privacy
... persons reasonable expectation of privacy. • In 1968 Congress codified the requirements to obtain court authority for interception of oral and wire communication • In 1986 this Act was amended to include ...
... persons reasonable expectation of privacy. • In 1968 Congress codified the requirements to obtain court authority for interception of oral and wire communication • In 1986 this Act was amended to include ...
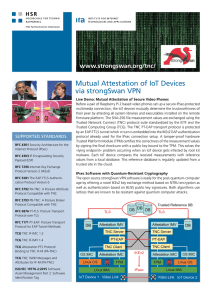
Mutual Attestation of IoT Devices via strongSwan VPN
... their peer by attesting all system libraries and executables installed on the remote firmware platform. The SHA-256 file measurement values are exchanged using the Trusted Network Connect (TNC) protocol suite standardized by the IETF and the Trusted Computing Group (TCG). The TNC PT-EAP transport pr ...
... their peer by attesting all system libraries and executables installed on the remote firmware platform. The SHA-256 file measurement values are exchanged using the Trusted Network Connect (TNC) protocol suite standardized by the IETF and the Trusted Computing Group (TCG). The TNC PT-EAP transport pr ...
PDF file that opens in a new window
... —— is a collection of facts in raw form that becomes information after processing. ...
... —— is a collection of facts in raw form that becomes information after processing. ...