Security
... (b) Login rejected after name entered (c) Login rejected after name and password typed ...
... (b) Login rejected after name entered (c) Login rejected after name and password typed ...
Hosting Solution for ShowGo Trade Show
... Software’s data hosting is much lower than having the client store the data. Also, with economies of scale, our support team can manage and maintain client’s connection and data at a lower cost than their internal IT department. Lower costs equals better value. ...
... Software’s data hosting is much lower than having the client store the data. Also, with economies of scale, our support team can manage and maintain client’s connection and data at a lower cost than their internal IT department. Lower costs equals better value. ...
Open Source Software
... Principal Licenses • GPL – Allows anyone to use and modify it, but if modified versions are distributed, the source code for the modifications must also be distributed. Special rules for libraries • BSD – does not even have this restriction. Credit must be given to the original authors; you can't p ...
... Principal Licenses • GPL – Allows anyone to use and modify it, but if modified versions are distributed, the source code for the modifications must also be distributed. Special rules for libraries • BSD – does not even have this restriction. Credit must be given to the original authors; you can't p ...
View File
... one of the most famous security models implemented as mandatory policies on system has two key policies: no read up (simple security property) – a subject can only read/write an object if the current security level of the subject dominates (>=) the classification of the object ...
... one of the most famous security models implemented as mandatory policies on system has two key policies: no read up (simple security property) – a subject can only read/write an object if the current security level of the subject dominates (>=) the classification of the object ...
Resume - KreativeKorp
... MCCM III: Developed a database client program to manage material related to my works of fiction and present the material in an accessible manner. Work & Volunteer Experience Information Technology volunteer; Napa Valley College; July 7, 2010 – December 18, 2010 Installed and repaired computer equi ...
... MCCM III: Developed a database client program to manage material related to my works of fiction and present the material in an accessible manner. Work & Volunteer Experience Information Technology volunteer; Napa Valley College; July 7, 2010 – December 18, 2010 Installed and repaired computer equi ...
Document
... The performance of your computer depends on how you use it. Despite the speed and the type microprocessor installed in your computer, you may find that the computer seems to respond slower (or not at all). This could be a result of many issues such as: ...
... The performance of your computer depends on how you use it. Despite the speed and the type microprocessor installed in your computer, you may find that the computer seems to respond slower (or not at all). This could be a result of many issues such as: ...
SUMMARY OF THE SYLLABUS FOR THE RE-EXAM IN COMP
... The performance of your computer depends on how you use it. Despite the speed and the type microprocessor installed in your computer, you may find that the computer seems to respond slower (or not at all). This could be a result of many issues such as: ...
... The performance of your computer depends on how you use it. Despite the speed and the type microprocessor installed in your computer, you may find that the computer seems to respond slower (or not at all). This could be a result of many issues such as: ...
Cyber Security I
... A process occurs when a task is executed. Keeping processes separate prevents the failure of one process from negatively impacting another. ...
... A process occurs when a task is executed. Keeping processes separate prevents the failure of one process from negatively impacting another. ...
Talk Abstracts - CSEE Research Day 2008
... civilization and try to understand where we are going tomorrow. It will argue that while we have become very good in quickly connecting an entity with another entity world-wide as long as the former knows the address of the latter, current technology for taking the message or service from one indivi ...
... civilization and try to understand where we are going tomorrow. It will argue that while we have become very good in quickly connecting an entity with another entity world-wide as long as the former knows the address of the latter, current technology for taking the message or service from one indivi ...
Access Control, Operations Security, and Computer Forensics
... E-mail monitoring • Inform users that all e-mail is being monitored by displaying log-on banner – Banner should state: logging on to system consents user to being monitored. Unauthorized access is prohibited. Subject to prosecution. ...
... E-mail monitoring • Inform users that all e-mail is being monitored by displaying log-on banner – Banner should state: logging on to system consents user to being monitored. Unauthorized access is prohibited. Subject to prosecution. ...
Remote Domain Security Awareness Training
... Set up your computer for automatic software and OS updates Disable Java Scripting and Flash in your web browser Use Firewall software Don't install or download unknown programs to your computer. Never open an email from a stranger Choose strong password for accounts Use browser other than IE ...
... Set up your computer for automatic software and OS updates Disable Java Scripting and Flash in your web browser Use Firewall software Don't install or download unknown programs to your computer. Never open an email from a stranger Choose strong password for accounts Use browser other than IE ...
PowerPoint 簡報
... reveal certain inherent weaknesses within the target host. – These might be key factors in implementing an actual compromise of the target's security. ...
... reveal certain inherent weaknesses within the target host. – These might be key factors in implementing an actual compromise of the target's security. ...
Architecting High-Security Systems for Multilateral
... defective operating systems which could be attacked. Even standalone hypervisors consist of a vast quantity of highly specialised code which is likely to contain errors that are exploitable by an attacker. While policies for controlling the information flow between Virtual Machines (VMs) may exist i ...
... defective operating systems which could be attacked. Even standalone hypervisors consist of a vast quantity of highly specialised code which is likely to contain errors that are exploitable by an attacker. While policies for controlling the information flow between Virtual Machines (VMs) may exist i ...
Security - UTRGV Faculty Web
... website in another country can go through a third country’s proxy server. There are websites dedicated to provide and hourly updated list of free anonymous proxy server sites.” Abraham, John. “A Proxy Server for ...
... website in another country can go through a third country’s proxy server. There are websites dedicated to provide and hourly updated list of free anonymous proxy server sites.” Abraham, John. “A Proxy Server for ...
Firewall
... • imposes security by limiting which such connections are allowed • once created usually relays traffic without examining contents • typically used when trust internal users by allowing general outbound connections • SOCKS commonly used for this ...
... • imposes security by limiting which such connections are allowed • once created usually relays traffic without examining contents • typically used when trust internal users by allowing general outbound connections • SOCKS commonly used for this ...
Victims who were Hacked PowerPoint Presentation
... What Is An Anti-Virus Software? A software designed to be used on your computer to find, treat, remove and keep malwares away. It will keep all your computer data safe! ...
... What Is An Anti-Virus Software? A software designed to be used on your computer to find, treat, remove and keep malwares away. It will keep all your computer data safe! ...
Attestation
... Music file is encrypted. TCG prevents anyone from getting music file in the clear. Can anti-virus companies block virus without ever seeing its code in the clear? ...
... Music file is encrypted. TCG prevents anyone from getting music file in the clear. Can anti-virus companies block virus without ever seeing its code in the clear? ...
Lec.4.Communication software and the internet
... communicate is called a computer network. • This involves installing network cards in each computer. • Each computer is then connected through cabling to a central device called a hub. • The most commonly used protocol for establishing and maintaining communication across a network is called TCP/IP ...
... communicate is called a computer network. • This involves installing network cards in each computer. • Each computer is then connected through cabling to a central device called a hub. • The most commonly used protocol for establishing and maintaining communication across a network is called TCP/IP ...
ch 5 - sm.luth.se
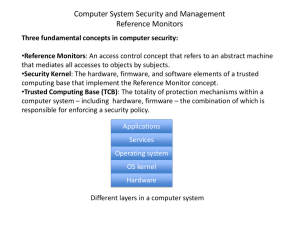
... Three fundamental concepts in computer security: •Reference Monitors: An access control concept that refers to an abstract machine that mediates all accesses to objects by subjects. •Security Kernel: The hardware, firmware, and software elements of a trusted computing base that implement the Referen ...
... Three fundamental concepts in computer security: •Reference Monitors: An access control concept that refers to an abstract machine that mediates all accesses to objects by subjects. •Security Kernel: The hardware, firmware, and software elements of a trusted computing base that implement the Referen ...
What is Trusted Computing and Digital Rights Management
... What are the risks associated with Trusted Computing and Digital Rights Management? DRM can adversely affect the full usability of documents. Information providers can encumber documents with restrictions and conditions imposed by the provider. For example, providers can set a document to become un ...
... What are the risks associated with Trusted Computing and Digital Rights Management? DRM can adversely affect the full usability of documents. Information providers can encumber documents with restrictions and conditions imposed by the provider. For example, providers can set a document to become un ...
Computer Components
... that has been prerecorded with data that gives instructions (BIOS or basic input/output system) used to check the computer system’s components to make sure they are working and to activate the essential software that controls the processing function when the computer is turned on or booted ...
... that has been prerecorded with data that gives instructions (BIOS or basic input/output system) used to check the computer system’s components to make sure they are working and to activate the essential software that controls the processing function when the computer is turned on or booted ...
Document
... Incorporates Google Chrome as user interface (UI) User does not have to worry about drivers or software updates ...
... Incorporates Google Chrome as user interface (UI) User does not have to worry about drivers or software updates ...
Asia-Pacific Regional Forum on Mainstreaming ICT Accessibility for
... • The purpose of GPII is to ensure that everyone who faces accessibility barriers due to disability, literacy, or aging, regardless of economic resources, can access and use the Internet and all its information, communities, and services for education, employment, daily living, civic participation, ...
... • The purpose of GPII is to ensure that everyone who faces accessibility barriers due to disability, literacy, or aging, regardless of economic resources, can access and use the Internet and all its information, communities, and services for education, employment, daily living, civic participation, ...
EnvisionManager System Software System control, monitoring and management
... management and monitoring software tool. It provides users with full visibility of the lighting and energy management system status and performance, while enabling simple local or global system adjustments. ...
... management and monitoring software tool. It provides users with full visibility of the lighting and energy management system status and performance, while enabling simple local or global system adjustments. ...