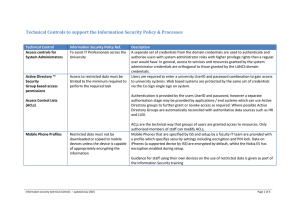
Technical Controls to support the Information
... decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With this capability users obtain the correct level of access that their computer/device is ...
... decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With this capability users obtain the correct level of access that their computer/device is ...
Example: Data Mining for the NBA - The University of Texas at Dallas
... more limited than the original one). When a full-functionality application is affected by attacks or newly discovered vulnerabilities, these alternative design and implementations based on different ATIs provide secure critical ...
... more limited than the original one). When a full-functionality application is affected by attacks or newly discovered vulnerabilities, these alternative design and implementations based on different ATIs provide secure critical ...
Chapter 2: Attackers and Their Attacks
... buffer of temporary memory. If a misconfigured OS or program allows for more information than was intended into the stack, then malicious code can be inserted into the stack and executed. ...
... buffer of temporary memory. If a misconfigured OS or program allows for more information than was intended into the stack, then malicious code can be inserted into the stack and executed. ...
Data Confidentiality
... • program claims to do one thing but instead does damage when you run it – delete files, erase hard disk ...
... • program claims to do one thing but instead does damage when you run it – delete files, erase hard disk ...
DPI as a means of access segregation in a corporate
... Each rule equals one user group in domain; Fast access granting – no need to change device config; Easy access recertification; ...
... Each rule equals one user group in domain; Fast access granting – no need to change device config; Easy access recertification; ...
Security
... The Biba Model • Principles to guarantee integrity of data 1. Simple integrity principle ...
... The Biba Model • Principles to guarantee integrity of data 1. Simple integrity principle ...
Security - Glasnost
... The Biba Model • Principles to guarantee integrity of data 1. Simple integrity principle ...
... The Biba Model • Principles to guarantee integrity of data 1. Simple integrity principle ...
Module 2
... alone computers that are not part of a domain or when you are authenticating to a server using an IP address. • It also acts a fallback authentication if it cannot complete Kerberos authentication such as being blocked by a firewall. • NTLM uses a challenge-response mechanism for authentication, in ...
... alone computers that are not part of a domain or when you are authenticating to a server using an IP address. • It also acts a fallback authentication if it cannot complete Kerberos authentication such as being blocked by a firewall. • NTLM uses a challenge-response mechanism for authentication, in ...
Collaborative Filtering
... • Use approximation of ratings to make predictions against a regression model • Apply to situations where rating vectors have large Euclidean distances but very high Similarity Computation scores ...
... • Use approximation of ratings to make predictions against a regression model • Apply to situations where rating vectors have large Euclidean distances but very high Similarity Computation scores ...
Sujoy Sinha Roy - Cyber Security at IIT Kanpur
... attacks. Of several candidates, lattice-based public-key cryptography is the most promising one. We investigated implementation aspects of lattice-based post-quantum public key schemes whose security is based on the hardness of the ring-LWE problem. These cryptographic schemes perform arithmetic ope ...
... attacks. Of several candidates, lattice-based public-key cryptography is the most promising one. We investigated implementation aspects of lattice-based post-quantum public key schemes whose security is based on the hardness of the ring-LWE problem. These cryptographic schemes perform arithmetic ope ...
Chapter 5 - Department of Computer Science and Information Systems
... If communication is sensitive additional measures must be taken to protect the data ...
... If communication is sensitive additional measures must be taken to protect the data ...
The Applications Perspective
... • “Theory” and “Experiment” have been two traditional pillars of scientific research; “Simulation” has been added as the third pillar • To do for other engineering what VLSI has achieved • Abstraction layers missing: hence HPC • Non-linearity & quantum mechanics: hence HPC ...
... • “Theory” and “Experiment” have been two traditional pillars of scientific research; “Simulation” has been added as the third pillar • To do for other engineering what VLSI has achieved • Abstraction layers missing: hence HPC • Non-linearity & quantum mechanics: hence HPC ...
Secure Deduplication with Efficient and Reliable
... encryption practical is to efficiently and reliably manage a huge number of convergent keys. The first attempt to formally address the problem of achieving efficient and reliable key management in secure Deduplication. We first introduce a baseline approach in which each user holds an independent ma ...
... encryption practical is to efficiently and reliably manage a huge number of convergent keys. The first attempt to formally address the problem of achieving efficient and reliable key management in secure Deduplication. We first introduce a baseline approach in which each user holds an independent ma ...
Time-saving Tools for the Overworked MicroStation User
... • Survey CAD managers and design team leaders • Get in communication with clients/contractors and understand what you need and want from each other • Implement the solution that covers the most bases • Accept that it is a changing process • Don’t limit yourself to initial cost in assessing ROI • Les ...
... • Survey CAD managers and design team leaders • Get in communication with clients/contractors and understand what you need and want from each other • Implement the solution that covers the most bases • Accept that it is a changing process • Don’t limit yourself to initial cost in assessing ROI • Les ...
Operating System Security Fundamentals
... Quick Quiz ____________________ is a process that decides whether users are permitted to perform the functions they request. A. Identification B. Authentication C. Authorization D. Verification _____________________________ allows you to sign on once to a server (host machine) and then not have to ...
... Quick Quiz ____________________ is a process that decides whether users are permitted to perform the functions they request. A. Identification B. Authentication C. Authorization D. Verification _____________________________ allows you to sign on once to a server (host machine) and then not have to ...
ppt
... In traditional systems development... • interactions between components are too rigidly defined • organisational structure is not captured well ...
... In traditional systems development... • interactions between components are too rigidly defined • organisational structure is not captured well ...
Paul Hardy - Curriculum Vitae
... ArcGIS for the 9.2 release. Before that I spent 28 years (1975-2003) at Laser-Scan Ltd, a world-renowned supplier of leading-edge solutions for digital mapping, charting, GIS, and spatial databases. During this time, I held following roles: Principal Consultant - Consultant and presenter, providin ...
... ArcGIS for the 9.2 release. Before that I spent 28 years (1975-2003) at Laser-Scan Ltd, a world-renowned supplier of leading-edge solutions for digital mapping, charting, GIS, and spatial databases. During this time, I held following roles: Principal Consultant - Consultant and presenter, providin ...
Before You Begin: Assign Information Classification
... 4. Gather Data from the Computer Third-party software, such as anti-virus and anti- ...
... 4. Gather Data from the Computer Third-party software, such as anti-virus and anti- ...
Information Systems and Networks
... access, abuse, or fraud is not limited to a single location but can occur at any access point in the network Security refers to the policies, procedures, and technical measures used to prevent unauthorized access, alteration, theft, or physical damage to information systems. Controls are methods, po ...
... access, abuse, or fraud is not limited to a single location but can occur at any access point in the network Security refers to the policies, procedures, and technical measures used to prevent unauthorized access, alteration, theft, or physical damage to information systems. Controls are methods, po ...
Slide 1
... Scheduled planned maintenance still occurs Systems are not protected against natural or human-caused calamity Service available in four different levels Business requirement determines level of HA service ...
... Scheduled planned maintenance still occurs Systems are not protected against natural or human-caused calamity Service available in four different levels Business requirement determines level of HA service ...
Approach - Northwestern University Information Technology
... Scheduled planned maintenance still occurs Systems are not protected against natural or human-caused calamity Service available in four different levels Business requirement determines level of HA service ...
... Scheduled planned maintenance still occurs Systems are not protected against natural or human-caused calamity Service available in four different levels Business requirement determines level of HA service ...
Mod_7-Ch11
... Digital Certificates • In cryptography, a public key certificate (also known as a digital certificate or identity certificate) is an electronic document used to prove ownership of a public key. • The certificate includes information about the key, information about its owner's identity, • A Digital ...
... Digital Certificates • In cryptography, a public key certificate (also known as a digital certificate or identity certificate) is an electronic document used to prove ownership of a public key. • The certificate includes information about the key, information about its owner's identity, • A Digital ...