Document
... Utah Dept. of Health hacked, over 500,000 700,000 affected and the number’s growing April 9, 2012 - Marjorie Cortez provides an update on a breach that started out bad enough last week, and just got a lot worse: Some 280,000 people had their Social Security numbers listed in state health data stolen ...
... Utah Dept. of Health hacked, over 500,000 700,000 affected and the number’s growing April 9, 2012 - Marjorie Cortez provides an update on a breach that started out bad enough last week, and just got a lot worse: Some 280,000 people had their Social Security numbers listed in state health data stolen ...
ppt
... • Goal – limit attacker’s possibilities by creating layers of hindrance (e.g. access) • Administrative controls should be part of security policy ...
... • Goal – limit attacker’s possibilities by creating layers of hindrance (e.g. access) • Administrative controls should be part of security policy ...
Staff ID Cards Poster
... Information Security Information Security Adviser: Ext. 47100 http://intranet/infosec/ ...
... Information Security Information Security Adviser: Ext. 47100 http://intranet/infosec/ ...
19-DS-05-2016_OZGUR
... Dr. Ferhat Ozgur Catak [email protected] TÜBİTAK BİLGEM Cyber Security Institute Role: Senior Researcher Proposal activity: • SEC-17-BES-2017: Architectures and organizations, big data and data analytics for customs risk management of the international goods supply chain trade movements • S ...
... Dr. Ferhat Ozgur Catak [email protected] TÜBİTAK BİLGEM Cyber Security Institute Role: Senior Researcher Proposal activity: • SEC-17-BES-2017: Architectures and organizations, big data and data analytics for customs risk management of the international goods supply chain trade movements • S ...
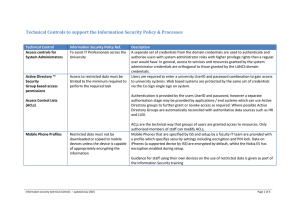
Technical Controls to support the Information
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
... Furthermore, when a user connects to the network, the PASS system makes an informed decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With thi ...
HSARPA Cyber Security R&D
... The Internet serves a significant underlying role in many of the Nation’s critical infrastructures ...
... The Internet serves a significant underlying role in many of the Nation’s critical infrastructures ...
Chapter 4
... 38. The formulation of program policy in the ____________________ document establishes the overall information security environment. 39. In an organization, a(n) ____________________ security policy provides detailed, targeted guidance to instruct all the members in the use of technology-based syste ...
... 38. The formulation of program policy in the ____________________ document establishes the overall information security environment. 39. In an organization, a(n) ____________________ security policy provides detailed, targeted guidance to instruct all the members in the use of technology-based syste ...
FEARLESS - Cyber Security Research and Education Institute
... Computer/Information Security, Network Security, Data and Applications Security, Digital Forensics, Cryptography, Data Privacy, Secure Web Services, Secure Cloud Computing, Hardware Security, CISSP Modules ...
... Computer/Information Security, Network Security, Data and Applications Security, Digital Forensics, Cryptography, Data Privacy, Secure Web Services, Secure Cloud Computing, Hardware Security, CISSP Modules ...
Introduction - Computer Science
... Security attacks Security services Methods of Defense A model for Internetwork Security Internet standards and RFCs ...
... Security attacks Security services Methods of Defense A model for Internetwork Security Internet standards and RFCs ...
PROTECTING INFORMATION RESOURCES
... it to determine insurance premiums and interest rates, do pre-employment screening, etc. It turns out that scammers have been posing as small businesses to improperly access data about individuals. The scammers would open accounts with ChoicePoint masquerading as small businesses and then improperly ...
... it to determine insurance premiums and interest rates, do pre-employment screening, etc. It turns out that scammers have been posing as small businesses to improperly access data about individuals. The scammers would open accounts with ChoicePoint masquerading as small businesses and then improperly ...
Network Security - University of Hull
... Entities themselves encompass other entities – Collection or Containment Security involves: Physical Changes – Commissioning Operational Procedure – What they do Structure – Interrelations ...
... Entities themselves encompass other entities – Collection or Containment Security involves: Physical Changes – Commissioning Operational Procedure – What they do Structure – Interrelations ...
Siveillance Vantage
... to operations. Role-based responsibilities of operators and a flexible web-based client concept support central as well as decentralized organizations and processes. Advanced operations management In addition to the pure display of alarms and incidents, each signal can be associated with defined act ...
... to operations. Role-based responsibilities of operators and a flexible web-based client concept support central as well as decentralized organizations and processes. Advanced operations management In addition to the pure display of alarms and incidents, each signal can be associated with defined act ...
Importance of SETA programs
... implement, or operate security programs * by developing skills and knowledge so that users can perform their jobs more securely * by improving awareness of the need to protect system resources ...
... implement, or operate security programs * by developing skills and knowledge so that users can perform their jobs more securely * by improving awareness of the need to protect system resources ...
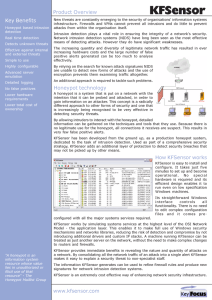
Factsheet - KFSensor
... New threats are constantly emerging to the security of organisations' information systems infrastructure. Firewalls and VPNs cannot prevent all intrusions and do little to prevent attacks from within the organisation itself. Intrusion detection plays a vital role in ensuring the integrity of a netwo ...
... New threats are constantly emerging to the security of organisations' information systems infrastructure. Firewalls and VPNs cannot prevent all intrusions and do little to prevent attacks from within the organisation itself. Intrusion detection plays a vital role in ensuring the integrity of a netwo ...
TNS03%20Introduction%20to%20Network%20Security
... Appears to be benign (良好) software but secretly downloading a virus or other malware. For a Trojan horse to spread, you must invite these programs onto your computers. For example, by opening an email attachment or downloading and running a file from the Internet. ...
... Appears to be benign (良好) software but secretly downloading a virus or other malware. For a Trojan horse to spread, you must invite these programs onto your computers. For example, by opening an email attachment or downloading and running a file from the Internet. ...
10.2 BASIC E-COMMERCE SECURITY ISSUES AND LANDSCAPE
... Drivers for EC security management: The laws and regulations with which organizations must comply. The conduct of global EC. Information assets have become critical to the operation of many businesses. New and faster information technologies are shared throughout organizations. The complexit ...
... Drivers for EC security management: The laws and regulations with which organizations must comply. The conduct of global EC. Information assets have become critical to the operation of many businesses. New and faster information technologies are shared throughout organizations. The complexit ...
Chapter 1 Study Outline
... Scanning computer systems for weaknesses in configurations or patch levels will help an organization identify potential entry points for intruders. ...
... Scanning computer systems for weaknesses in configurations or patch levels will help an organization identify potential entry points for intruders. ...
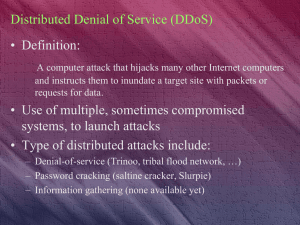
Distributed Denial of Service (DDoS)
... • Use intrusion detection tools to detect specific packet attacks • Check for Trojan horse and zombie code – Network vulnerability scans – Host vulnerability scans – Antivirus ...
... • Use intrusion detection tools to detect specific packet attacks • Check for Trojan horse and zombie code – Network vulnerability scans – Host vulnerability scans – Antivirus ...
ch 5 - sm.luth.se
... A process is an important unit of control for the OS and for the security. A process consists of: • Executable code. • Data. • The execution context. Processes communicate with each other through primitives provided by the OS, IPC. Less secure because of the context switch between processes. Expensi ...
... A process is an important unit of control for the OS and for the security. A process consists of: • Executable code. • Data. • The execution context. Processes communicate with each other through primitives provided by the OS, IPC. Less secure because of the context switch between processes. Expensi ...
Understanding and Installing Firewalls
... number of major internet security breaches which occurred in the late 1980s: Clifford Stoll's discovery of German spies tampering with his system. Bill Cheswick's "Evening with Berferd" 1992 in which he set up a simple electronic jail to observe an attacker. In 1988, an employee at the NASA Ames Res ...
... number of major internet security breaches which occurred in the late 1980s: Clifford Stoll's discovery of German spies tampering with his system. Bill Cheswick's "Evening with Berferd" 1992 in which he set up a simple electronic jail to observe an attacker. In 1988, an employee at the NASA Ames Res ...
US SAFE WEB Act - Higher Education Compliance Alliance
... improve enforcement regarding privacy and security breaches among other consumer protection matters. The Federal Trade Commission has brought law enforcement actions against a variety of entities across a broad spectrum of industries who have failed to implement reasonable and appropriate security m ...
... improve enforcement regarding privacy and security breaches among other consumer protection matters. The Federal Trade Commission has brought law enforcement actions against a variety of entities across a broad spectrum of industries who have failed to implement reasonable and appropriate security m ...
CS5038: The Electronic Society - Homepages | The University of
... • How to implement? – Technological enforcement? – Policy enforcement? • What are the barriers? • The major problem, identified by extensive empirical study (structured interviews, etc.) is a social one: – Bankers don’t like being embarrassed in front of clients, , losing face and maybe losing busin ...
... • How to implement? – Technological enforcement? – Policy enforcement? • What are the barriers? • The major problem, identified by extensive empirical study (structured interviews, etc.) is a social one: – Bankers don’t like being embarrassed in front of clients, , losing face and maybe losing busin ...
2001-10-11-AIC-SecurityForEducation
... child be exposed to harm due to a failure in the existing system? ...
... child be exposed to harm due to a failure in the existing system? ...