Introduction to IT Security - Virginia Alliance for Secure Computing
... This is not the most obvious means, nor is it the one against which the most solid defense has been installed.” (Pflegger) ...
... This is not the most obvious means, nor is it the one against which the most solid defense has been installed.” (Pflegger) ...
APT-Tactics
... We detail the typical intentions of an attacker and the tools and processes they would leverage to attain these goals. Lastly, the course presents key approaches to detect and terminate the process of an APT, and the infrastructure required for effective incident response. ...
... We detail the typical intentions of an attacker and the tools and processes they would leverage to attain these goals. Lastly, the course presents key approaches to detect and terminate the process of an APT, and the infrastructure required for effective incident response. ...
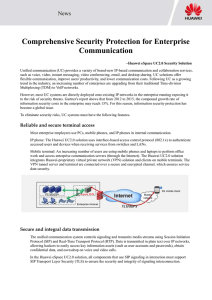
Comprehensive Security Protection for
... such as voice, video, instant messaging, video conferencing, email, and desktop sharing. UC solutions offer flexible communication, improve users' productivity, and lower communication costs. Following UC as a growing trend in the industry, an increasing number of enterprises are upgrading from thei ...
... such as voice, video, instant messaging, video conferencing, email, and desktop sharing. UC solutions offer flexible communication, improve users' productivity, and lower communication costs. Following UC as a growing trend in the industry, an increasing number of enterprises are upgrading from thei ...
TrendMicro Titanium - A New Concept in Security by Ira Wilsker
... The Parental Controls, System Tuner, and other features can be accessed by clicking on the Tools button. Some of the other features accessible in this manner are a Secure Erase utility, Data Theft Prevention, Trend Micro Vault, and a Free Tool Center. The Parental Controls utility is intended to pro ...
... The Parental Controls, System Tuner, and other features can be accessed by clicking on the Tools button. Some of the other features accessible in this manner are a Secure Erase utility, Data Theft Prevention, Trend Micro Vault, and a Free Tool Center. The Parental Controls utility is intended to pro ...
WelcometoCISandCybercorps
... Secure System Administration and Certification: Provisioning, procurement and installation of network, hardware and software systems for mission critical enterprises. System configuration, integration and maintenance. Incident handling and response. Methodologies and standards for system testing, ve ...
... Secure System Administration and Certification: Provisioning, procurement and installation of network, hardware and software systems for mission critical enterprises. System configuration, integration and maintenance. Incident handling and response. Methodologies and standards for system testing, ve ...
HIPAA Security Standards
... There are several types of firewall techniques: • Packet filter: Looks at each packet entering or leaving the network and accepts or rejects it based on user-defined rules. Packet filtering is fairly effective and transparent to users, but it is difficult to configure. In addition, it is susceptible ...
... There are several types of firewall techniques: • Packet filter: Looks at each packet entering or leaving the network and accepts or rejects it based on user-defined rules. Packet filtering is fairly effective and transparent to users, but it is difficult to configure. In addition, it is susceptible ...
D1S1_TSV404_Course_Intro_2011_v1
... ■ Organization has not established its own baseline configurations ■ Although NSA/DISA established a gold standard, may be too much for some installations and breaks applications ■ Baseline configurations are a mandatory control under CM-2 of NIST SP 800-53 ...
... ■ Organization has not established its own baseline configurations ■ Although NSA/DISA established a gold standard, may be too much for some installations and breaks applications ■ Baseline configurations are a mandatory control under CM-2 of NIST SP 800-53 ...
Naval Postgraduate School
... 3. Curriculum Requirements: All of the following courses are part of the sponsor-approved curriculum and must be completed or validated by all USN students. Non-USN students are required to complete these courses unless directed by their sponsoring service or agency: Completed ___CS3030 Fundamentals ...
... 3. Curriculum Requirements: All of the following courses are part of the sponsor-approved curriculum and must be completed or validated by all USN students. Non-USN students are required to complete these courses unless directed by their sponsoring service or agency: Completed ___CS3030 Fundamentals ...
STUXNET - Clemson
... With over 30,000 IP Addresses affected (and increasing) Iran is baffled and bluntly blames The United States Of America and Israel ...
... With over 30,000 IP Addresses affected (and increasing) Iran is baffled and bluntly blames The United States Of America and Israel ...
Types of Encryption Algorithms
... 1. Contamination of internal database via actions of cooperating companies 2. Service delays/denial for intranet traffic due to Internet/ISP problems 3. Compromise or delay of intranet traffic due to crypto mismanagement 4. Compromise of internal traffic patterns ...
... 1. Contamination of internal database via actions of cooperating companies 2. Service delays/denial for intranet traffic due to Internet/ISP problems 3. Compromise or delay of intranet traffic due to crypto mismanagement 4. Compromise of internal traffic patterns ...
Operating Systems 4
... manager into allowing a process to access main memory cells outside its allotted area. Or may try to trick the file manager into retrieving files whose access should be ...
... manager into allowing a process to access main memory cells outside its allotted area. Or may try to trick the file manager into retrieving files whose access should be ...
Security and Privacy in Sensor Networks: Research Challenges
... Security v.s. robustness, fault tolerance, resiliency Security is not a black/white world, it is progressive We must secure entire networked system, not just an individual component Solutions must be robust/adapt to new threats as much as possible ...
... Security v.s. robustness, fault tolerance, resiliency Security is not a black/white world, it is progressive We must secure entire networked system, not just an individual component Solutions must be robust/adapt to new threats as much as possible ...
Emsisoft Internet Security
... small businesses, who frequently travel beyond their home network and who want something simple-yet-intelligent that will keep their information secure, no matter where they go. ...
... small businesses, who frequently travel beyond their home network and who want something simple-yet-intelligent that will keep their information secure, no matter where they go. ...
Computer security - University of London International Programmes
... This course deals with the more technical means of making a computing system secure. This process starts with defining the proper security requirements, which are usually stated as a security policy. Security models formalise those policies and may serve as a reference to check the correctness of an ...
... This course deals with the more technical means of making a computing system secure. This process starts with defining the proper security requirements, which are usually stated as a security policy. Security models formalise those policies and may serve as a reference to check the correctness of an ...
Bandura® Releases REACT™ Software to Integrate Internal
... security technology, today introduced the REACT™ software product that allows customers to integrate real‐time threat information from their own network into the PoliWall® security appliance, providing a critical element of secure network architecture. PoliWall is an in‐line appliance (physical ...
... security technology, today introduced the REACT™ software product that allows customers to integrate real‐time threat information from their own network into the PoliWall® security appliance, providing a critical element of secure network architecture. PoliWall is an in‐line appliance (physical ...
Cyber-Terrorism
... • Australian Government’s objective – to create a trusted and secure electronic operating environment • The E-Security National Agenda • Joint Operating Arrangement ...
... • Australian Government’s objective – to create a trusted and secure electronic operating environment • The E-Security National Agenda • Joint Operating Arrangement ...
Beyond Data Breach Cyber Trends and Exposures â Mr. Jason Kelly
... Contamination of Third Party Data by any unauthorized software, computer code or virus Denial of access to third party data Theft of an access code from the Company's premises Destruction, modification, corruption, damage or deletion of Data Physical theft of the Company's hardware Data disclosure d ...
... Contamination of Third Party Data by any unauthorized software, computer code or virus Denial of access to third party data Theft of an access code from the Company's premises Destruction, modification, corruption, damage or deletion of Data Physical theft of the Company's hardware Data disclosure d ...
About EICTA - Baltic IT&T Review
... break-in; company received a ransom demand of £10 million. (Apr’01) A system administrator, angered by his diminished role in a thriving defense manufacturing firm whose computer network he alone had developed and managed, centralized the software that supported the company’s manufacturing processes ...
... break-in; company received a ransom demand of £10 million. (Apr’01) A system administrator, angered by his diminished role in a thriving defense manufacturing firm whose computer network he alone had developed and managed, centralized the software that supported the company’s manufacturing processes ...
2001-09-07-AIC-SecurityForEducation
... • Use one-to-one NAT for externally accessible hosts or special clients (or where you have room) • Use many-to-one (PAT, IP Masquerading, overloaded nat) for client access to the Internet • NAT can break a lot of software, so be aware of address translation issues –anything that requires a host-to-h ...
... • Use one-to-one NAT for externally accessible hosts or special clients (or where you have room) • Use many-to-one (PAT, IP Masquerading, overloaded nat) for client access to the Internet • NAT can break a lot of software, so be aware of address translation issues –anything that requires a host-to-h ...
systemsprinciples2
... – To know what we need to be protected from – Mechanisms that can implement many policies ...
... – To know what we need to be protected from – Mechanisms that can implement many policies ...
diebold nixdorf software terminal security intrusion protection
... or are covertly installed on self-service environments. In fact, reports on new variants of ATM malware are published every few months. Recently, security experts discovered that the infamous Ploutus malware is back, joining the hundreds of other malware such as WannaCry affecting terminals worldwid ...
... or are covertly installed on self-service environments. In fact, reports on new variants of ATM malware are published every few months. Recently, security experts discovered that the infamous Ploutus malware is back, joining the hundreds of other malware such as WannaCry affecting terminals worldwid ...
The Top Ten of Security
... – The “reading room” for SANS, a large computer security training organization. ...
... – The “reading room” for SANS, a large computer security training organization. ...
Data Mining BS/MS Project
... Clusters are shown as different colors in this visual, anomaly detection identifies the outliers (axes/instances for this graph are not specified in the paper) ...
... Clusters are shown as different colors in this visual, anomaly detection identifies the outliers (axes/instances for this graph are not specified in the paper) ...
CS 494/594 Computer and Network Security - UTK-EECS
... Access control: the prevention of unauthorized use of a resource Data confidentiality: the protection of data from unauthorized disclosure Data integrity: the assurance that data received are exactly as sent by an authorized entity (i.e., contain no modification, insertion, deletion, or replay). Non ...
... Access control: the prevention of unauthorized use of a resource Data confidentiality: the protection of data from unauthorized disclosure Data integrity: the assurance that data received are exactly as sent by an authorized entity (i.e., contain no modification, insertion, deletion, or replay). Non ...
CS 494/594 Computer and Network Security - UTK-EECS
... Access control: the prevention of unauthorized use of a resource Data confidentiality: the protection of data from unauthorized disclosure Data integrity: the assurance that data received are exactly as sent by an authorized entity (i.e., contain no modification, insertion, deletion, or replay). Non ...
... Access control: the prevention of unauthorized use of a resource Data confidentiality: the protection of data from unauthorized disclosure Data integrity: the assurance that data received are exactly as sent by an authorized entity (i.e., contain no modification, insertion, deletion, or replay). Non ...