D`Amo - softfarm
... Federal Information Processing Standard (FIPS) is a set of standards required by the United States Federal Government for use in computer systems used by government agencies and contractors. • Well-known FIPS standards include the Data Encryption Standard (DES) and the Advanced Encryption Standard ( ...
... Federal Information Processing Standard (FIPS) is a set of standards required by the United States Federal Government for use in computer systems used by government agencies and contractors. • Well-known FIPS standards include the Data Encryption Standard (DES) and the Advanced Encryption Standard ( ...
networkworld - Sift Security
... analyst to continue with the investigation and take it to its conclusion. Actions can include things like opening a ticket or adding an IP address to a block list. Now let's take a more detailed look at how an analyst can conduct an investigation using the graph data structure. The investigators wou ...
... analyst to continue with the investigation and take it to its conclusion. Actions can include things like opening a ticket or adding an IP address to a block list. Now let's take a more detailed look at how an analyst can conduct an investigation using the graph data structure. The investigators wou ...
Hacker Ethics presentation
... information IS property According to United Kingdom, with the Criminal Damage Act of 1971. – Offender in the UK was convicted of property damage even though the property was not tangible and the damage could only be determined by the machine. ...
... information IS property According to United Kingdom, with the Criminal Damage Act of 1971. – Offender in the UK was convicted of property damage even though the property was not tangible and the damage could only be determined by the machine. ...
Network and Systems Security
... Legal threats – Copyright infringements, DoS attacks, hacking attempts, Unacceptable content Wastes valuable resources – Staff time, bandwidth Bad PR ...
... Legal threats – Copyright infringements, DoS attacks, hacking attempts, Unacceptable content Wastes valuable resources – Staff time, bandwidth Bad PR ...
Network Security Chapter 14
... 7. ____ involves determining the damage that would result from an attack and the likelihood that the vulnerability is a risk to the organization. a. Risk assessment c. Vulnerability appraisal b. Risk mitigation d. Asset identification ...
... 7. ____ involves determining the damage that would result from an attack and the likelihood that the vulnerability is a risk to the organization. a. Risk assessment c. Vulnerability appraisal b. Risk mitigation d. Asset identification ...
Are Clouds Secure? - San Francisco Bay Area ISSA Chapter
... • All five are “open” and deal with authentication, but…. ...
... • All five are “open” and deal with authentication, but…. ...
Document
... Identities / access to system or network data source: http://markn.ca/2011/whaling/ ...
... Identities / access to system or network data source: http://markn.ca/2011/whaling/ ...
Power Point Slides - Organization of American States
... preparedness for natural or man-made disasters •Based on a bio-incident scenario which takes place at an airport. Three Stages. Debriefs include recommendations for strengthening CIP and resilience •Partners: PAHO; Interpol; UN; US DHHS; FEMA; CDC •TTXs for Ports: discuss vulnerabilities; responsibi ...
... preparedness for natural or man-made disasters •Based on a bio-incident scenario which takes place at an airport. Three Stages. Debriefs include recommendations for strengthening CIP and resilience •Partners: PAHO; Interpol; UN; US DHHS; FEMA; CDC •TTXs for Ports: discuss vulnerabilities; responsibi ...
Module F - Columbus State University
... to be privileged to know about, or at least take seriously. Computers around the world are systematically being victimized by rampant hacking. This hacking is not only widespread, but is being executed so flawlessly that the attackers compromise a system, steal everything of value and completely era ...
... to be privileged to know about, or at least take seriously. Computers around the world are systematically being victimized by rampant hacking. This hacking is not only widespread, but is being executed so flawlessly that the attackers compromise a system, steal everything of value and completely era ...
18_DataCenter_Security_Overview
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
18_DataCenter_Security_Overview
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
Distributed System Concepts and Architectures
... “Cluster Security with NVisionCC:Process Monitoring by Leveraging Emergent Properties”, ...
... “Cluster Security with NVisionCC:Process Monitoring by Leveraging Emergent Properties”, ...
PowerPoint Presentation - IF-MAP
... • More Informed Sensors – Sensors can tune by role and other things – Should reduce false alarms ...
... • More Informed Sensors – Sensors can tune by role and other things – Should reduce false alarms ...
Basic Marketing, 16e
... AdAware at www.lavasoftUSA.com The Cleaner at www.moosoft.com Trojan First Aid Kit (TFAK) at www.wilders.org Check it out before you download at www.spychecker.com ...
... AdAware at www.lavasoftUSA.com The Cleaner at www.moosoft.com Trojan First Aid Kit (TFAK) at www.wilders.org Check it out before you download at www.spychecker.com ...
SECURITY
... “Identify the risk then either accept it, or reduce it or insure against it.” “Security does not have to be perfect but risks have to be manageable.” “Outsource to experts!” ...
... “Identify the risk then either accept it, or reduce it or insure against it.” “Security does not have to be perfect but risks have to be manageable.” “Outsource to experts!” ...
Harvard SEAS Information Security Office Services Overview
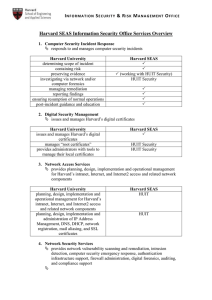
... regulatory/policy compliance review IT risk assessments vendor/service provider compliance review firewall rule analysis post-incident remediation guidance research data security ...
... regulatory/policy compliance review IT risk assessments vendor/service provider compliance review firewall rule analysis post-incident remediation guidance research data security ...
CIS 203 Artificial Intelligence
... implementation. With that being said, Network Security is a very important topic and extremely practical. Fortune 500 companies and other large companies rely heavily on Network Security to protect their confidential information and also to keep their computer networks from failing. A poor network s ...
... implementation. With that being said, Network Security is a very important topic and extremely practical. Fortune 500 companies and other large companies rely heavily on Network Security to protect their confidential information and also to keep their computer networks from failing. A poor network s ...
William Stallings, Cryptography and Network Security 5/e
... of a resource Data Confidentiality –protection of data from unauthorized disclosure Data Integrity - assurance that data received is as sent by an authorized entity Non-Repudiation - protection against denial by one of the parties in a communication Availability – resource accessible/usable ...
... of a resource Data Confidentiality –protection of data from unauthorized disclosure Data Integrity - assurance that data received is as sent by an authorized entity Non-Repudiation - protection against denial by one of the parties in a communication Availability – resource accessible/usable ...
Network Security Management.pdf
... The costs of having a security vulnerability and taking actions to close it are high. Using a tool to help in these tasks will reduce errors, saves costs by eliminating redundant actions, streamlines actions by prioritizing between multiple bugs and actions. It also gives you a chance to plan ahead ...
... The costs of having a security vulnerability and taking actions to close it are high. Using a tool to help in these tasks will reduce errors, saves costs by eliminating redundant actions, streamlines actions by prioritizing between multiple bugs and actions. It also gives you a chance to plan ahead ...
... how something in such sphere becomes a threat. Seeking to contribute to the debate, this study analyses the securitization discourses of Brazil and of the United States from Hansen and Nissenbaum’s (2009) theorization about the existence of a specific sector for cybersecurity. To comprehend the secu ...