Information security in a youth organisation?
... The information security policy is one solution • to ensure security on the three criteria (CID) • that is not limited to computers • for all information and resources ...
... The information security policy is one solution • to ensure security on the three criteria (CID) • that is not limited to computers • for all information and resources ...
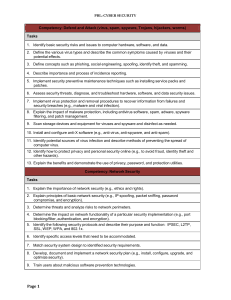
Competency: Defend and Attack (virus, spam, spyware - FBLA-PBL
... 7. Distinguish between public key encryption and digital signatures. 8. Describe cryptographic protocols and applications, like digital cash, password-authenticated key agreement, multi-party key agreement, and time stamping service. Competency: Authentication Tasks 1. Describe authentication proces ...
... 7. Distinguish between public key encryption and digital signatures. 8. Describe cryptographic protocols and applications, like digital cash, password-authenticated key agreement, multi-party key agreement, and time stamping service. Competency: Authentication Tasks 1. Describe authentication proces ...
Symbolic Honeynets for Gathering Cyber
... providing a high-interaction vulnerable HMI that interfaces with actual robotic hardware running ROS. ...
... providing a high-interaction vulnerable HMI that interfaces with actual robotic hardware running ROS. ...
Preventing Social Engineering
... Never disclose passwords Limit IT Information disclosed Limit information in auto-reply emails Escort guests in sensitive areas Question people you don't know Talk to employees about security Centralize reporting of suspicious behavior ...
... Never disclose passwords Limit IT Information disclosed Limit information in auto-reply emails Escort guests in sensitive areas Question people you don't know Talk to employees about security Centralize reporting of suspicious behavior ...
Incident Response: Six Steps for Managing Cyber Breaches
... This is where your proactive sensitive data auditing against a predefined baseline of where your data is and should be stored can save you significant time. With the data map in hand, you are two giant steps closer to knowing which data was the likely target of the malware. The ability to scope the ...
... This is where your proactive sensitive data auditing against a predefined baseline of where your data is and should be stored can save you significant time. With the data map in hand, you are two giant steps closer to knowing which data was the likely target of the malware. The ability to scope the ...
PowerPoint Presentation - Lead
... • Is the process of preventing and detecting unauthorized use of your computer • Prevention measures help you to stop unauthorized users from accessing any part of your computer system. • Detection helps you to determine whether or not someone attempted to break into your system, if they were succes ...
... • Is the process of preventing and detecting unauthorized use of your computer • Prevention measures help you to stop unauthorized users from accessing any part of your computer system. • Detection helps you to determine whether or not someone attempted to break into your system, if they were succes ...
Information Assurance Awareness, Training, Education at the U.S.
... • People are still tricked into disclosing their passwords ...
... • People are still tricked into disclosing their passwords ...
Computer and Information Security
... • Attacking is becoming so common and easy – there are books clearly explaining how to launch them • Security and attacks are a perpetual cat-and-mouse play. The only way to avoid attacks is to keep up-to-date with latest trends and stay ahead of malicious netizens ...
... • Attacking is becoming so common and easy – there are books clearly explaining how to launch them • Security and attacks are a perpetual cat-and-mouse play. The only way to avoid attacks is to keep up-to-date with latest trends and stay ahead of malicious netizens ...
Cyber Risks of Manufacturers Limiting the Risk Factors of
... Employers should encourage their employees to break up any routine tasks during the workday by taking a walk or doing a few quick stretches. Each employee should also ensure that his or her workstation is suited for his or her individual needs. For more information on MSDs and preventing workplace i ...
... Employers should encourage their employees to break up any routine tasks during the workday by taking a walk or doing a few quick stretches. Each employee should also ensure that his or her workstation is suited for his or her individual needs. For more information on MSDs and preventing workplace i ...
Threat Briefing - (AFCEA) Ottawa Chapter
... Identity & Access Management ‘Halt! Step forward and be recognized’. This form of identity confirmation to grant access to the fortification is the basic foundation for today’s Identity and Access Management problem. This session will discuss fundamental concepts to ensure system access is granted o ...
... Identity & Access Management ‘Halt! Step forward and be recognized’. This form of identity confirmation to grant access to the fortification is the basic foundation for today’s Identity and Access Management problem. This session will discuss fundamental concepts to ensure system access is granted o ...
Computer Science, MSCS - Northeastern University
... Computer Science, MSCS Northeastern University’s Master of Science in Computer Science is designed to prepare students for a variety of careers in computer science. The program combines both computing and important application domains—enabling you to increase your broad-based knowledge in the field ...
... Computer Science, MSCS Northeastern University’s Master of Science in Computer Science is designed to prepare students for a variety of careers in computer science. The program combines both computing and important application domains—enabling you to increase your broad-based knowledge in the field ...
Current IT Security Threats
... instructions provided in spear phishing emails, leading to empty bank accounts, compromise of systems around the world, compromise of contractors, industrial espionage and much more. Best defenses: This is the most challenging risk. Security awareness training is important but is definitely not suff ...
... instructions provided in spear phishing emails, leading to empty bank accounts, compromise of systems around the world, compromise of contractors, industrial espionage and much more. Best defenses: This is the most challenging risk. Security awareness training is important but is definitely not suff ...
Key To Personal Information Security
... client and server in a network, a very small space exists to handle the usually rapid "hand-shaking" exchange of messages that sets up a session. The session-establishing packets include a SYN field that identifies the sequence order. To cause this kind of attack, an attacker can send many packets, ...
... client and server in a network, a very small space exists to handle the usually rapid "hand-shaking" exchange of messages that sets up a session. The session-establishing packets include a SYN field that identifies the sequence order. To cause this kind of attack, an attacker can send many packets, ...
6.01 RCNET Module
... Security Plan Formal document that provides an overview of the security requirements for the information system and describes the security controls in place or planned for meeting those requirements. Security Policy Security policies define the objectives and constraints for the security program. Po ...
... Security Plan Formal document that provides an overview of the security requirements for the information system and describes the security controls in place or planned for meeting those requirements. Security Policy Security policies define the objectives and constraints for the security program. Po ...
Huntsman Security updates trail-blazing cyber security analytics and
... release of its enterprise-wide cyber defence technology. This update enhances the security analytic capabilities, expands the cloud integration connector and delivers increased response capabilities. “This new version builds on the existing capabilities we have in enterprise security analytics, mach ...
... release of its enterprise-wide cyber defence technology. This update enhances the security analytic capabilities, expands the cloud integration connector and delivers increased response capabilities. “This new version builds on the existing capabilities we have in enterprise security analytics, mach ...
Insider Threat and the Dark Web: Cyber Response Mini
... Crisis Management Executive that has a broad enterprise view of the organization and capable of making critical decisions while understanding impacts to the entire business. A dedicated Crisis Management Executive will result in incident management teams that are effective and not paralyzed with det ...
... Crisis Management Executive that has a broad enterprise view of the organization and capable of making critical decisions while understanding impacts to the entire business. A dedicated Crisis Management Executive will result in incident management teams that are effective and not paralyzed with det ...
OSI Security Architecture
... Aspects of Security • The OSI security architecture focuses on 3 aspects: security attacks, mechanisms, and services. 1. Security attack: Any action that compromises the security of information owned by an organization. 2. Security service: A processing or communication service that enhances the sec ...
... Aspects of Security • The OSI security architecture focuses on 3 aspects: security attacks, mechanisms, and services. 1. Security attack: Any action that compromises the security of information owned by an organization. 2. Security service: A processing or communication service that enhances the sec ...
security threats: a guide for small and medium
... Employees and end users within an organization may unknowingly introduce malware on the network when they run malicious executable code (EXE files). Sometimes they might receive an email with an attached worm or download spyware when visiting a malicious website. Alternatively, to get work done, emp ...
... Employees and end users within an organization may unknowingly introduce malware on the network when they run malicious executable code (EXE files). Sometimes they might receive an email with an attached worm or download spyware when visiting a malicious website. Alternatively, to get work done, emp ...
Information Systems and Networks
... and all of its users to share the same 40-bit encrypted password, which can be easily decrypted by hackers from a small amount of traffic Stronger encryption and authentication systems are ...
... and all of its users to share the same 40-bit encrypted password, which can be easily decrypted by hackers from a small amount of traffic Stronger encryption and authentication systems are ...
Network Security
... Outline of the Course • This chapter serves as an introduction to the entire course. The remainder of the book is organized into three parts: • Part One : Provides a concise survey of the cryptographic algorithms and protocols underlying network security applications, including encryption, hash fun ...
... Outline of the Course • This chapter serves as an introduction to the entire course. The remainder of the book is organized into three parts: • Part One : Provides a concise survey of the cryptographic algorithms and protocols underlying network security applications, including encryption, hash fun ...
presentation
... units in a manner that requires the user to have little or no knowledge of the unique characteristics of those units". ...
... units in a manner that requires the user to have little or no knowledge of the unique characteristics of those units". ...
secure operating system
... A secure operating system provides security mechanisms that ensure that the system's security goals are enforced despite the threats faced by the system. Systems that provide a high degree of assurance in enforcement have been called secure systems, or even more frequently “trusted” Systems. However ...
... A secure operating system provides security mechanisms that ensure that the system's security goals are enforced despite the threats faced by the system. Systems that provide a high degree of assurance in enforcement have been called secure systems, or even more frequently “trusted” Systems. However ...
Computer and Information Security
... • Deception – acceptance of false data • Disruption- interruption or prevention of correct operation • Usurpation- unauthorized control of some part of a system ...
... • Deception – acceptance of false data • Disruption- interruption or prevention of correct operation • Usurpation- unauthorized control of some part of a system ...
View File
... no read up (simple security property) – a subject can only read/write an object if the current security level of the subject dominates (>=) the classification of the object ...
... no read up (simple security property) – a subject can only read/write an object if the current security level of the subject dominates (>=) the classification of the object ...