6_HighTechBridge_WSIS_2015_IK
... Cost of the global cybercrime is about $445 billion per year, a 33% percent growth - Center for Strategic and International Studies (CSIS) and McAfee Companies experience in average 2 successful attacks per week – Ponemon Institute and Hewlett-Packard Cybercrime is rising significantly in Euro ...
... Cost of the global cybercrime is about $445 billion per year, a 33% percent growth - Center for Strategic and International Studies (CSIS) and McAfee Companies experience in average 2 successful attacks per week – Ponemon Institute and Hewlett-Packard Cybercrime is rising significantly in Euro ...
Future of Cyber Security and the Issue of Cyber warfare: A
... NCSD - National Cyber Security Division, which is a division of the Office of Cyber Security & Communications, within the United StatesDepartment of Homeland Security's Directorate for National Protection and Programs. To protect the cyber infrastructure, NCSD has identified two overarching objectiv ...
... NCSD - National Cyber Security Division, which is a division of the Office of Cyber Security & Communications, within the United StatesDepartment of Homeland Security's Directorate for National Protection and Programs. To protect the cyber infrastructure, NCSD has identified two overarching objectiv ...
"O brave new world, that has such people in`t
... 50,000 employees, it needs to think about data security with 50,000 people," said Germano. Erect firewalls and pigeon-hole information on a "need to know" basis. Beef up password protection by requiring less predictable codes and storing employee and customer information in an encrypted fashion. ...
... 50,000 employees, it needs to think about data security with 50,000 people," said Germano. Erect firewalls and pigeon-hole information on a "need to know" basis. Beef up password protection by requiring less predictable codes and storing employee and customer information in an encrypted fashion. ...
Position: Senior IA/Security Specialist, (Computer Network Defense
... • B.S. in a Computer Information Systems or related Degree Program • Secret Clearance with SSBI or TS/SCI with SSBI ...
... • B.S. in a Computer Information Systems or related Degree Program • Secret Clearance with SSBI or TS/SCI with SSBI ...
Global Challenges
... Following the World Summit on the Information Society (WSIS), Heads of States and world leaders entrusted ITU to take the lead in coordinating international efforts as the sole Facilitator of Action Line C5, "Building confidence and security in the use of ICTs". Resolutions from PP, WTSA, WTDC call ...
... Following the World Summit on the Information Society (WSIS), Heads of States and world leaders entrusted ITU to take the lead in coordinating international efforts as the sole Facilitator of Action Line C5, "Building confidence and security in the use of ICTs". Resolutions from PP, WTSA, WTDC call ...
Cyber ShockWave exposed missing links in US security
... Finally, we must recognize that everyone is a combatant in the world of cyber warfare. Civilians are on the front lines because our personal communications and network systems are the conduits for Internet warfare. This means that the responsibility for cybersecurity must be a joint effort involving ...
... Finally, we must recognize that everyone is a combatant in the world of cyber warfare. Civilians are on the front lines because our personal communications and network systems are the conduits for Internet warfare. This means that the responsibility for cybersecurity must be a joint effort involving ...
john p. carlin - AFCEA International
... employees responsible for protecting the nation against terrorism, espionage, and cyber and other national security threats. Prior to assuming his role in the NSD, Mr. Carlin served as Chief of Staff and Senior Counsel to Robert S. Mueller, III, former director of the FBI, where he helped lead the F ...
... employees responsible for protecting the nation against terrorism, espionage, and cyber and other national security threats. Prior to assuming his role in the NSD, Mr. Carlin served as Chief of Staff and Senior Counsel to Robert S. Mueller, III, former director of the FBI, where he helped lead the F ...
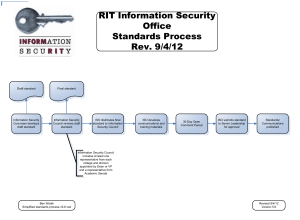
Enter Title in Docm Properties
... bug-fixes. Depending on your skill level, this will evolve into leading a team to develop new product modules for the Tofino Industrial Security Solution product line. You should be a good team player that works well on joint development efforts, as this is a multifaceted project. You should also un ...
... bug-fixes. Depending on your skill level, this will evolve into leading a team to develop new product modules for the Tofino Industrial Security Solution product line. You should be a good team player that works well on joint development efforts, as this is a multifaceted project. You should also un ...
SMALL FIRMS CYBERSECURITY GUIDANCE
... larger organizations ($1,564 and $371, respectively) due to cyber attacks.2 The SEC and FINRA have also begun examinations of cybersecurity preparedness among broker-dealers. As a result, it is crucial for small financial firms to take proper cybersecurity measures - measures to protect all computin ...
... larger organizations ($1,564 and $371, respectively) due to cyber attacks.2 The SEC and FINRA have also begun examinations of cybersecurity preparedness among broker-dealers. As a result, it is crucial for small financial firms to take proper cybersecurity measures - measures to protect all computin ...
Cybersecurity for Asset Managers: Shielding Your Firm
... To become more cyber resilient, firms should not only incorporate perimeter security, but also implement business risk/reward decision making, cyber risk management and control techniques throughout their business processes. They should also secure buy-in from the organization’s leadership. Creating ...
... To become more cyber resilient, firms should not only incorporate perimeter security, but also implement business risk/reward decision making, cyber risk management and control techniques throughout their business processes. They should also secure buy-in from the organization’s leadership. Creating ...
National Initiative For Cybersecurity Education (NICE)
... Analyze and identify best practices to help organizations recruit and retain cybersecurity professionals. Evaluate the professionalization of the cybersecurity workforce. ...
... Analyze and identify best practices to help organizations recruit and retain cybersecurity professionals. Evaluate the professionalization of the cybersecurity workforce. ...
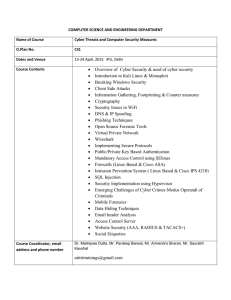
• Overview of Cyber Security & need of cyber security • Introduction
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
new zealand`s cyber security strategy
... • Increasing use of internet and digital systems • Cyber threats increasing and more sophisticated – no international borders • Threats to: - individuals - government-held information - businesses and intellectual property - critical national infrastructure ...
... • Increasing use of internet and digital systems • Cyber threats increasing and more sophisticated – no international borders • Threats to: - individuals - government-held information - businesses and intellectual property - critical national infrastructure ...
Maritime Cyber Vulnerabilities in the Energy Domain
... In 2013, 40% of cyber attacks were directed at energy infrastructure. Challenges to energy industry cyber security can be broken down into 2 major categories. • Protecting the equipment that generates energy • Preventing the attackers to access to system database ...
... In 2013, 40% of cyber attacks were directed at energy infrastructure. Challenges to energy industry cyber security can be broken down into 2 major categories. • Protecting the equipment that generates energy • Preventing the attackers to access to system database ...
Applied Cybersecurity
... best protect their enterprises. In this course, experts from academia, the military, and industry share their knowledge to give participants the principles, the state of the practice, and strategies for the future. Sessions will address information security, ethical and legal practices, and mitigati ...
... best protect their enterprises. In this course, experts from academia, the military, and industry share their knowledge to give participants the principles, the state of the practice, and strategies for the future. Sessions will address information security, ethical and legal practices, and mitigati ...
Cybersecurity - Queen`s Wiki
... • Microsoft reports the ransomware attack rate in Canada is 4x higher than any other country • A recent Anti-Phishing Working Group study states there are more phishing attacks “than at any other time in history” with incidents rising by a massive 250% in 2016. ...
... • Microsoft reports the ransomware attack rate in Canada is 4x higher than any other country • A recent Anti-Phishing Working Group study states there are more phishing attacks “than at any other time in history” with incidents rising by a massive 250% in 2016. ...
10 years APCERT - Conferences
... IT System Environment Risks/ Technology Evolves Intellectual Property ...
... IT System Environment Risks/ Technology Evolves Intellectual Property ...
Online dating Virtual gaming Twitter LinkedIn Facebook Google +
... • Cybersecurity Information Sharing Act of 2012 – Feinstein/Mikulski Bill S.2102 ...
... • Cybersecurity Information Sharing Act of 2012 – Feinstein/Mikulski Bill S.2102 ...
One Team, One Fight
... Deputy Under Secretary for Cybersecurity and Communications Department of Homeland Security ...
... Deputy Under Secretary for Cybersecurity and Communications Department of Homeland Security ...
Interagency Cybersecurity Forum Launched; NRC Chairman Allison Macfarlane Chairs Inaugural Meeting
... NRC Chairman Allison Macfarlane Chairs Inaugural Meeting On Friday Oct. 10, 2014, senior leaders from independent and executive branch regulatory agencies launched the interagency Cybersecurity Forum for Independent and Executive Branch Agencies. The Forum’s objectives are to enhance communication, ...
... NRC Chairman Allison Macfarlane Chairs Inaugural Meeting On Friday Oct. 10, 2014, senior leaders from independent and executive branch regulatory agencies launched the interagency Cybersecurity Forum for Independent and Executive Branch Agencies. The Forum’s objectives are to enhance communication, ...