download
... may be actively and maliciously trying to circumvent any protective measures you put in place ...
... may be actively and maliciously trying to circumvent any protective measures you put in place ...
Presentation Prepared By: Raghda Zahran
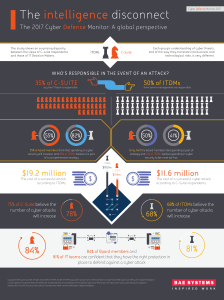
... Information security is not just a paperwork drill…there are dangerous adversaries out there capable of launching serious attacks on our information systems that can result in severe or catastrophic damage to the nation’s critical information infrastructure and ultimately threaten our economic and ...
... Information security is not just a paperwork drill…there are dangerous adversaries out there capable of launching serious attacks on our information systems that can result in severe or catastrophic damage to the nation’s critical information infrastructure and ultimately threaten our economic and ...
Chapter 10: Electronic Commerce Security
... What are some steps a company can take to thwart cybercriminals from within a business? Is a computer with anti-virus software protected from viruses? Why or why not? What are the differences between encryption and authentication? Discuss the role of administration in implementing a security ...
... What are some steps a company can take to thwart cybercriminals from within a business? Is a computer with anti-virus software protected from viruses? Why or why not? What are the differences between encryption and authentication? Discuss the role of administration in implementing a security ...
Open resource
... Establish working relationship and rapport with State and local area CISOs in the region represented Coordinate with Federal personnel within region to integrate cyber security response and assessment perspectives (i.e., with PSAs, FEMA, Federal LE, etc) Coordinate cyber and communications incident ...
... Establish working relationship and rapport with State and local area CISOs in the region represented Coordinate with Federal personnel within region to integrate cyber security response and assessment perspectives (i.e., with PSAs, FEMA, Federal LE, etc) Coordinate cyber and communications incident ...
practice
... Cyber attacks : Form part to the national team formulating cyber security policy and laws ( Draft stage) Developed Cyber Security framework and Cyber Security Response Plan. Carry out vulnerability assessments to ensure corrective action is taken. Scan the international, Regional and National ...
... Cyber attacks : Form part to the national team formulating cyber security policy and laws ( Draft stage) Developed Cyber Security framework and Cyber Security Response Plan. Carry out vulnerability assessments to ensure corrective action is taken. Scan the international, Regional and National ...
Networking and System Administration (NaSA) Bachelor of Science in
... Computer Systems Administrator ...
... Computer Systems Administrator ...
Lecture 3.1 - Host
... We begin by briefly reviewing the major components of a modern operating system (O.S.). At the lowest level of the system is the BIOS (Basic Input Output System). The BIOS is responsible for testing I/O devices and loading the operating system. Surprisingly many computers do not protect their BIOS s ...
... We begin by briefly reviewing the major components of a modern operating system (O.S.). At the lowest level of the system is the BIOS (Basic Input Output System). The BIOS is responsible for testing I/O devices and loading the operating system. Surprisingly many computers do not protect their BIOS s ...
20121101
... • Karl F. Lutzen – Certified Information Systems Security Professional (CISSP) – S&T Information Security Officer – Instructor for CS 362 ...
... • Karl F. Lutzen – Certified Information Systems Security Professional (CISSP) – S&T Information Security Officer – Instructor for CS 362 ...
Real Systems - e
... Real Systems™ has created software and implemented numerous public and private modern information systems enabling further development of information society. The main customers of the company are central public institutions, large private companies and law enforcement organizations. Company’s portf ...
... Real Systems™ has created software and implemented numerous public and private modern information systems enabling further development of information society. The main customers of the company are central public institutions, large private companies and law enforcement organizations. Company’s portf ...
Computer Security: Principles and Practice, 1/e
... and reporting it so that corrective action can be taken. ...
... and reporting it so that corrective action can be taken. ...
PSWG Closed Door Proposal - Western Electricity Coordinating
... Security guidelines and diagrams Security incidents Counter threat methods Security probe techniques and methods used by external security consultants to test for the ability to penetrate, compromise, and/or disrupt critical cyber assets Potential and existing security vulnerabilities that have not ...
... Security guidelines and diagrams Security incidents Counter threat methods Security probe techniques and methods used by external security consultants to test for the ability to penetrate, compromise, and/or disrupt critical cyber assets Potential and existing security vulnerabilities that have not ...
Artificial Intelligence for Cyber Security (AICS)
... systems by the cyber security community. One promising approach to mitigate this problem is to build models of human behavior and enable formal reasoning about how human beings interact with cyber systems. Game theory, in particular, has been used to model human behavior and leveraging game-theoreti ...
... systems by the cyber security community. One promising approach to mitigate this problem is to build models of human behavior and enable formal reasoning about how human beings interact with cyber systems. Game theory, in particular, has been used to model human behavior and leveraging game-theoreti ...
Overview of Operating Systems Security Features
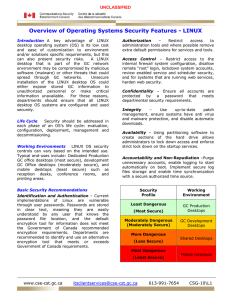
... Overview of Operating Systems Security Features - LINUX Introduction A key advantage of LINUX desktop operating system (OS) is its low cost and ease of customization to environment and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the G ...
... Overview of Operating Systems Security Features - LINUX Introduction A key advantage of LINUX desktop operating system (OS) is its low cost and ease of customization to environment and/or solutions specific requirements, but this can also present security risks. A LINUX desktop that is part of the G ...
Alice and Bob Get Physical: Insights into Physical Layer Security
... Although conventional cryptographic security mechanisms are essential to the overall problem of securing wireless networks, these techniques do not directly leverage the unique properties of the wireless domain to address security threats. The properties of the wireless medium are a powerful source ...
... Although conventional cryptographic security mechanisms are essential to the overall problem of securing wireless networks, these techniques do not directly leverage the unique properties of the wireless domain to address security threats. The properties of the wireless medium are a powerful source ...
Privacy Legislation Update $1.7 Million Civil Penalty for a
... Detecting a Breach Due to the rapidly evolving nature of the information security threat spectrum, it is important that organisations also include breach detection capabilities within their environment. This should include: ...
... Detecting a Breach Due to the rapidly evolving nature of the information security threat spectrum, it is important that organisations also include breach detection capabilities within their environment. This should include: ...
PPT - pantherFILE
... utilize any otherwise idle machines. • Worms infiltrate computers usually by exploiting holes in the security of networked systems. • Worms usually attack programs that are already running. – The attack might result in creation of new processes, after which a worm can run independently, and self-pro ...
... utilize any otherwise idle machines. • Worms infiltrate computers usually by exploiting holes in the security of networked systems. • Worms usually attack programs that are already running. – The attack might result in creation of new processes, after which a worm can run independently, and self-pro ...
Virtual Cyber Security Lab - Celtic-Plus
... Develops ICT software solutions for more than 200 global operators ...
... Develops ICT software solutions for more than 200 global operators ...
Certifications authenticate Blancco´s high standards
... and Nordic customers are using the best data erasure solution available. ...
... and Nordic customers are using the best data erasure solution available. ...
Slides
... Oil and Gas Pipeline Systems Critical Manufacturing Systems Intelligent Transportation Systems Military Systems Communication Systems ...
... Oil and Gas Pipeline Systems Critical Manufacturing Systems Intelligent Transportation Systems Military Systems Communication Systems ...
Open ended challenge rationale
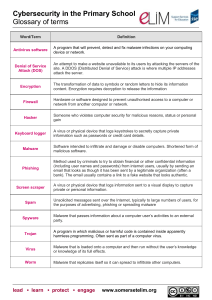
... Method used by criminals to try to obtain financial or other confidential information (including user names and passwords) from internet users, usually by sending an email that looks as though it has been sent by a legitimate organization (often a bank). The email usually contains a link to a fake w ...
... Method used by criminals to try to obtain financial or other confidential information (including user names and passwords) from internet users, usually by sending an email that looks as though it has been sent by a legitimate organization (often a bank). The email usually contains a link to a fake w ...
Shawn Bracken - CISSP103 Chester StMenlo Park, CA 94025
... Supported HP-UX Trusted Systems secure accounting/auditing and kernel configuration Our team was the 3rd layer support known as "backline" which handled the more difficult and time-consuming calls. Most customers were large production systems requiring high uptime. 1997 to 1998, Network Securi ...
... Supported HP-UX Trusted Systems secure accounting/auditing and kernel configuration Our team was the 3rd layer support known as "backline" which handled the more difficult and time-consuming calls. Most customers were large production systems requiring high uptime. 1997 to 1998, Network Securi ...