Junior Enlisted - Cyber Security
... Reported Operational Directive (OpDir) compliance for all Headquarters Marine Corps assets to include offsite locations (1200 workstations, 2500 users), and developed POA&Ms resulting in 97% compliance Assisted Marine Corps Network Operations and Security Center to prepare for Command Cyber Readines ...
... Reported Operational Directive (OpDir) compliance for all Headquarters Marine Corps assets to include offsite locations (1200 workstations, 2500 users), and developed POA&Ms resulting in 97% compliance Assisted Marine Corps Network Operations and Security Center to prepare for Command Cyber Readines ...
Skating on Stilts
... • 74% have implemented new measures as a result of regulation • 58% say regulation has “sharpened policy and improved security” • 28% say it has “diverted resources from improving security to recording/reporting incidents or other forms of compliance” ...
... • 74% have implemented new measures as a result of regulation • 58% say regulation has “sharpened policy and improved security” • 28% say it has “diverted resources from improving security to recording/reporting incidents or other forms of compliance” ...
Uniqua Consulting Gmbh - Data Mining Analyst
... The successful candidate will work in a dynamic team of talented analysts that enjoy the opportunity to work in a young organization with very high potential. He or she will analyze and characterize data to help protect networks from an ever present threat and to give business meaning to specific co ...
... The successful candidate will work in a dynamic team of talented analysts that enjoy the opportunity to work in a young organization with very high potential. He or she will analyze and characterize data to help protect networks from an ever present threat and to give business meaning to specific co ...
This Article argues that intellectual property law stifles critical
... vulnerabilities. Researchers who discover flaws often face legal threats based on IP claims if they reveal findings to anyone other than the software’s vendor. Externalities and network effects cause vendors’ incentives to diverge from those that are socially optimal. Unlike previous scholarship, th ...
... vulnerabilities. Researchers who discover flaws often face legal threats based on IP claims if they reveal findings to anyone other than the software’s vendor. Externalities and network effects cause vendors’ incentives to diverge from those that are socially optimal. Unlike previous scholarship, th ...
Systems Security
... The basic computer infrastructure, ranging from consumer desktops to business servers are under continual attack from a variety of miscreants (or “hackers”) for both fun and monetary gain. The design of computer systems have allowed many vulnerabilities to exist and the attacks exploit these vulnera ...
... The basic computer infrastructure, ranging from consumer desktops to business servers are under continual attack from a variety of miscreants (or “hackers”) for both fun and monetary gain. The design of computer systems have allowed many vulnerabilities to exist and the attacks exploit these vulnera ...
it user svq – level 2
... o Access control devices (e.g. locks, biometric controls, CCTV); o Limiting visibility of data (e.g. by positioning of monitors, using encryption); o Shielding (e.g. cable screening, Faraday cages); ...
... o Access control devices (e.g. locks, biometric controls, CCTV); o Limiting visibility of data (e.g. by positioning of monitors, using encryption); o Shielding (e.g. cable screening, Faraday cages); ...
Security
... or causing a normal process to change its behavior and create a breach, is a common goal of crackers. In fact, even most nonprogram security events have as their goal causing a program threat. For example, while it is useful to log in to a system without authorization, it is quite a lot more useful ...
... or causing a normal process to change its behavior and create a breach, is a common goal of crackers. In fact, even most nonprogram security events have as their goal causing a program threat. For example, while it is useful to log in to a system without authorization, it is quite a lot more useful ...
Preface
... science. Many people regard the “Communication Theory and Secrecy Systems” paper, by Claude Shannon in 1949, as the foundation of modern cryptology. However, at that time, cryptographic research was mostly restricted to government agencies and the military. That situation gradually changed with the ...
... science. Many people regard the “Communication Theory and Secrecy Systems” paper, by Claude Shannon in 1949, as the foundation of modern cryptology. However, at that time, cryptographic research was mostly restricted to government agencies and the military. That situation gradually changed with the ...
SANDS CORP CYBER JOB
... Minimum of three years hands on experience configuring and working with Information Technology Systems is preferred. Excellent problem solving skills, ability to triage and resolve critical technical issues. Current, relative industry certifications preferred. Must be able to work collaboratively wi ...
... Minimum of three years hands on experience configuring and working with Information Technology Systems is preferred. Excellent problem solving skills, ability to triage and resolve critical technical issues. Current, relative industry certifications preferred. Must be able to work collaboratively wi ...
Srini Devadas, MIT Computer Science and Artificial Intelligence Lab
... Against: Techniques are never going to protect against all attacks and therefore detection, diagnosis and recovery techniques are a necessity and a better investment of ...
... Against: Techniques are never going to protect against all attacks and therefore detection, diagnosis and recovery techniques are a necessity and a better investment of ...
Glenbriar TakeStock! - Glenbriar Technologies Inc.
... • Increasing cyber-threat sophistication and complexity • Greater vulnerabilities due to increasing use of mobile devices and cloud services • Increased awareness of economic costs of cyber-threats ...
... • Increasing cyber-threat sophistication and complexity • Greater vulnerabilities due to increasing use of mobile devices and cloud services • Increased awareness of economic costs of cyber-threats ...
New Law Requires Businesses in California to Report Electronic Break-Ins
... By Polly Dinkel and Heather Kirlin In the wake of a security breach at one of its own data centers, the State of California has enacted legislation that requires businesses to disclose computer security breaches. The stimulus for the legislation occurred in April 2002, when California’s Steven P. Te ...
... By Polly Dinkel and Heather Kirlin In the wake of a security breach at one of its own data centers, the State of California has enacted legislation that requires businesses to disclose computer security breaches. The stimulus for the legislation occurred in April 2002, when California’s Steven P. Te ...
Breach Detection in Healthcare
... access to patient records to do their jobs. However, how do we know someone else cannot gain unauthorized access to these files? Protecting those files is vital and a lot of attention, effort and technology is put into it. Challenge 1: Security awareness is not in the DNA Healthcare organizations ar ...
... access to patient records to do their jobs. However, how do we know someone else cannot gain unauthorized access to these files? Protecting those files is vital and a lot of attention, effort and technology is put into it. Challenge 1: Security awareness is not in the DNA Healthcare organizations ar ...
Why Cryptography is Harder Than It Looks
... • A good system balances actual failures against potential failures • Non-invasive attacks CAN be totally prevented • Targeted attacks can only be withstood up to a point • The problems with cryptography are not in the algorithms and protocols, but the implementation – Weakness are found at human in ...
... • A good system balances actual failures against potential failures • Non-invasive attacks CAN be totally prevented • Targeted attacks can only be withstood up to a point • The problems with cryptography are not in the algorithms and protocols, but the implementation – Weakness are found at human in ...
Zero day timebomb infographic3
... https://www.vmware.com/radius/five-things-to-come-for-security/ http://searchsecurity.techtarget.com/tip/Six-ways-to-improve-endpoint-device-security http://www.baesystems.com/en/cybersecurity/article/new-research-reveals-business-disconnect-in-defending-againstcyber-attacks https://www.avecto.com/r ...
... https://www.vmware.com/radius/five-things-to-come-for-security/ http://searchsecurity.techtarget.com/tip/Six-ways-to-improve-endpoint-device-security http://www.baesystems.com/en/cybersecurity/article/new-research-reveals-business-disconnect-in-defending-againstcyber-attacks https://www.avecto.com/r ...
Federal Bio
... Mr. Crane is located in Washington, DC where works for the Department of Homeland Security. Previously Mr. Crane was a Senior Information Security Consultant with Foundstone, a wholly owned subsidiary of McAfee, Inc. There he created and led the Information Security Management program. Service line ...
... Mr. Crane is located in Washington, DC where works for the Department of Homeland Security. Previously Mr. Crane was a Senior Information Security Consultant with Foundstone, a wholly owned subsidiary of McAfee, Inc. There he created and led the Information Security Management program. Service line ...
John L. Nunziato, Vice President , SOSSEC, Inc., is involved in
... executing every aspect of business development/operations of the System of Systems Security (SOSSEC) corporation and consortium. SOSSEC is a broad based consortium comprised of a diverse group of 70+ innovative, high-tech traditional and non-traditional contractors, academic institutions and non-pro ...
... executing every aspect of business development/operations of the System of Systems Security (SOSSEC) corporation and consortium. SOSSEC is a broad based consortium comprised of a diverse group of 70+ innovative, high-tech traditional and non-traditional contractors, academic institutions and non-pro ...
ICBA Encourages Consumers to Protect their Data during Cyber
... in ensuring their customers’ financial information is not being used improperly. These banks have established protocols to protect customers’ financial information from data breaches.” You can learn more about Cyber Security Awareness Month by visiting the Stay Safe Online website. Online resources ...
... in ensuring their customers’ financial information is not being used improperly. These banks have established protocols to protect customers’ financial information from data breaches.” You can learn more about Cyber Security Awareness Month by visiting the Stay Safe Online website. Online resources ...
Introduction - Personal Web Pages
... – In CA, there is a webpage listing all people that donate to Proposition 8 ballot measure ...
... – In CA, there is a webpage listing all people that donate to Proposition 8 ballot measure ...
Connecting the dots in Cyber Security Regional Workshop on Cyber Security Policies
... Kalachinkov, Moroccan Agent Secret ...
... Kalachinkov, Moroccan Agent Secret ...
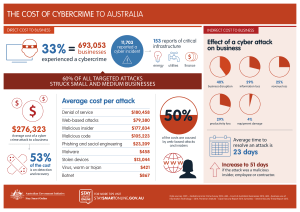
the cost of cybercrime to australia $276323
... Data sources: PWC – Global Economic Crime Survey 2014; ABS – Count of Australian Businesses 2014; ABS – Business use of Information Technology – 2014; Ponemon Institute – Cyber Security Report 2014; Symantec – Internet Security Threat Report 2015. ...
... Data sources: PWC – Global Economic Crime Survey 2014; ABS – Count of Australian Businesses 2014; ABS – Business use of Information Technology – 2014; Ponemon Institute – Cyber Security Report 2014; Symantec – Internet Security Threat Report 2015. ...
Proposed Part 73 Fuel Cycle Facility Security Rulemaking
... NRC Office of Nuclear Security and Incident Response Fuel Cycle Information Exchange Conference June 8, 2011 ...
... NRC Office of Nuclear Security and Incident Response Fuel Cycle Information Exchange Conference June 8, 2011 ...