* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Skating on Stilts
Cross-site scripting wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Unix security wikipedia , lookup
Airport security wikipedia , lookup
Cyberwarfare wikipedia , lookup
Cyberattack wikipedia , lookup
Wireless security wikipedia , lookup
Distributed firewall wikipedia , lookup
Cyber-security regulation wikipedia , lookup
International cybercrime wikipedia , lookup
Social engineering (security) wikipedia , lookup
Security-focused operating system wikipedia , lookup
Mobile security wikipedia , lookup
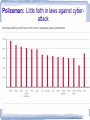
In the Crossfire International Cooperation and Computer Crime Stewart Baker 1815 1816 Waterloo Mt. Tambora 1817 th 6 century BC Stability and speed B Stability A C Speed What Point B Looks Like Stability and speed B Stability A C Speed What Point C Looks Like Summary • Attacks are already heavy • Adoption of security measures lags • The many roles of governments – Regulator – Policeman – Attacker 1. Attacks are already heavy • 60% reported theft-of-service cyberattacks – Low: Germany, UK (42%) – High: India (83%), Brazil (77%), France (76%) • 29% reported multiple large-scale denial of service attacks each month, and nearly two-thirds of those reported an impact on operations – High: France (60%), India (50%) • 89% report infection with viruses or other malware • 70+% report a wide range of other attacks – E.g., phishing and pharming. • More sophisticated attacks like DNS poisoning or SQL injection are less common, but still widespread – more than half of respondents report these attacks 2. Adoption of security measures lags behind the threat • Basic, key security measures are not widely adopted – Fewer than 60% patched and updated software on a regular schedule – User name and password the most common form of login/authentication – more than three-quarters of SCADA/ICS systems are connected to an IP network or the Internet • nearly half of those admitted that these connections create unresolved security issues • Security measure adoption rates vary widely by country Security measure adoption rate More than two dozen different security measures -- technologies, policies and procedures •Encryption for – •Security Information and Event Management tools • Online transmission to network •Network access control measures • Laptop hard drives •Intrusion prevention systems • Individual emails • Data in databases •Database security and access controls • Data while in network storage •Data leak prevention tools • Tapes, portable media •Intrusion detection systems •Authentication by – •Firewalls to public network • User name and password •Firewalls between systems • Token •Application whitelisting • Biometrics •Role and activity anomaly detection •Regular patches and updates •Standardized desktop •Threat information sharing •Use threat monitoring service •Restrict or ban USB sticks China leads in adopting security measures 3. The many roles of governments • Regulators – Regulation seen as generally positive • 74% have implemented new measures as a result of regulation • 58% say regulation has “sharpened policy and improved security” • 28% say it has “diverted resources from improving security to recording/reporting incidents or other forms of compliance” – Audit frequency varies widely • Policemen – Widespread skepticism about governments’ ability to protect networks • Attackers, infiltrators and adversaries Regulator: auditing to enforce compliance varies widely Policeman: Little faith in laws against cyberattack Attacker: 60% believe governments are already attacking their country Attacker: Many report government-style attacks •Half report “stealthy infiltration by high-level adversary … like in Ghostnet” •Half report DDOS attacks by “high-level adversaries” including governments: Attacker: United States and China are most feared; Russia is third China the outlier • Chinese executives report -– Uniquely close cooperation with officials – High levels of regulation and auditing – Very robust confidence in government – Much higher adoption of security measures • China is taking concerted steps to bolster its industries’ defenses • Are the steps effective? – Chinese companies report low to average levels of attack and damage – China does appear better protected than other large developing countries, such as India and Brazil