ICT Security
... package which protects the user from spyware, whilst surfing the internet, scans for spam emails, protects against phishing and provides a firewall. Organisations will need to decide how much of this protection is done centrally or on each individual PC. Laptops that are used outside of the organisa ...
... package which protects the user from spyware, whilst surfing the internet, scans for spam emails, protects against phishing and provides a firewall. Organisations will need to decide how much of this protection is done centrally or on each individual PC. Laptops that are used outside of the organisa ...
Chapter 9
... When traffic meets a filter that is defined in the policy, the security parameters much then be negotiated. The SA is what is agreed upon. Internet Key Exchange (IKE) – an algorithm used to generate the secret keys agreed upon in the SA. ...
... When traffic meets a filter that is defined in the policy, the security parameters much then be negotiated. The SA is what is agreed upon. Internet Key Exchange (IKE) – an algorithm used to generate the secret keys agreed upon in the SA. ...
Information Assurance Presentation
... gained access to an asset. modification - some unauthorized party tampers ...
... gained access to an asset. modification - some unauthorized party tampers ...
Presentation Title
... This presentation, including any supporting materials, is owned by Gartner, Inc. and/or its affiliates and is for the sole use of the intended Gartner audience or other authorized recipients. This presentation may contain information that is confidential, proprietary or otherwise legally protected, ...
... This presentation, including any supporting materials, is owned by Gartner, Inc. and/or its affiliates and is for the sole use of the intended Gartner audience or other authorized recipients. This presentation may contain information that is confidential, proprietary or otherwise legally protected, ...
Crypto in data security
... • The science of codes and passwords • Need to prove the identity of the sender and the recipient • The message In the meantime • Should not change the content of the message to make sure ...
... • The science of codes and passwords • Need to prove the identity of the sender and the recipient • The message In the meantime • Should not change the content of the message to make sure ...
DOCSpec
... Evaluate the three in 4 areas: databases, security, web services, and parallel processing/multi-threading. GOAL: To determine in which areas J2EE or .NET is better suited to be used. Also to determine in which areas CORBA can be beneficial. ...
... Evaluate the three in 4 areas: databases, security, web services, and parallel processing/multi-threading. GOAL: To determine in which areas J2EE or .NET is better suited to be used. Also to determine in which areas CORBA can be beneficial. ...
Chapter 14 Network Security - Northern Arizona University
... thrown away. • There are strict regulations that should be followed to control the disposal of computer components. • The system administrator is responsible for developing a policy based on environmental and safety guidelines for hardware that no longer works. • To view some examples of the disposa ...
... thrown away. • There are strict regulations that should be followed to control the disposal of computer components. • The system administrator is responsible for developing a policy based on environmental and safety guidelines for hardware that no longer works. • To view some examples of the disposa ...
Chapter 14 Network Security
... thrown away. • There are strict regulations that should be followed to control the disposal of computer components. • The system administrator is responsible for developing a policy based on environmental and safety guidelines for hardware that no longer works. • To view some examples of the disposa ...
... thrown away. • There are strict regulations that should be followed to control the disposal of computer components. • The system administrator is responsible for developing a policy based on environmental and safety guidelines for hardware that no longer works. • To view some examples of the disposa ...
security threats: a guide for small and medium
... passwords may not be changed (especially if not documented) thus leaving a backdoor for the exemployee. A startup company called JournalSpace 4 was caught with no backups when their former system administrator decided to wipe out the main database. This proved to be disastrous for the company which ...
... passwords may not be changed (especially if not documented) thus leaving a backdoor for the exemployee. A startup company called JournalSpace 4 was caught with no backups when their former system administrator decided to wipe out the main database. This proved to be disastrous for the company which ...
Types of Surveillance Technology Currently Used by Governments
... In contrast, in the works are efforts to create a new layer of identity Focusing on the user, the new system would not require multiple online IDs, but would be characterized by a single sign-on The system, called an “open security,” would be more secure and trustworthy, reducing theft, fraud, and a ...
... In contrast, in the works are efforts to create a new layer of identity Focusing on the user, the new system would not require multiple online IDs, but would be characterized by a single sign-on The system, called an “open security,” would be more secure and trustworthy, reducing theft, fraud, and a ...
Chapter 1 THE INFORMATION AGE IN WHICH YOU LIVE Changing
... Social Security Administration Social service agencies Department of Motor Vehicles ...
... Social Security Administration Social service agencies Department of Motor Vehicles ...
Information Security and its Implications on Everyday
... Technology isn’t perfect Probably won’t change significantly for the next 10 years E-crime on the rise “Genuine, widespread awareness of information security issues is the only practical way to counter attacks targeting computer users” http://www.noticebored.com/ It’s not easy, but a lot can be done ...
... Technology isn’t perfect Probably won’t change significantly for the next 10 years E-crime on the rise “Genuine, widespread awareness of information security issues is the only practical way to counter attacks targeting computer users” http://www.noticebored.com/ It’s not easy, but a lot can be done ...
Securing the Network - Austin Community College
... Sophisticated attack tools and open networks continue to generate an increased need for network security policies and infrastructure to protect organizations from internally and externally based attacks. Organizations must balance network security needs against ebusiness processes, legal issues, and ...
... Sophisticated attack tools and open networks continue to generate an increased need for network security policies and infrastructure to protect organizations from internally and externally based attacks. Organizations must balance network security needs against ebusiness processes, legal issues, and ...
WHAT IS EC SECURITY? - Joseph H. Schuessler, PhD
... Understand the importance and scope of security of information systems for EC. Describe the major concepts and terminology of EC security. Learn about the major EC security threats, vulnerabilities, and technical attacks. Understand Internet fraud, phishing, and spam. Describe the information assura ...
... Understand the importance and scope of security of information systems for EC. Describe the major concepts and terminology of EC security. Learn about the major EC security threats, vulnerabilities, and technical attacks. Understand Internet fraud, phishing, and spam. Describe the information assura ...
INFORMATION SYSTEMS ENGINEERING
... The tracks offered represent related groups of courses that are relevant for students with interests in the selected areas. Students are required to choose a track to follow and to take at least three courses from the selected track. The tracks are presented as an aid to students in planning their c ...
... The tracks offered represent related groups of courses that are relevant for students with interests in the selected areas. Students are required to choose a track to follow and to take at least three courses from the selected track. The tracks are presented as an aid to students in planning their c ...
Introduction to Information Security Chapter N
... Identify and understand the threats posed to information security Identify and understand the more common attacks associated with those threats ...
... Identify and understand the threats posed to information security Identify and understand the more common attacks associated with those threats ...
Chapter. 01
... For some Computer Security is controlling access to hardware, software and data of a computerized system. A large measure of computer security is simply keeping the computer system's information secure. In broader terms, computer security can be thought of as the protection of the computer and its r ...
... For some Computer Security is controlling access to hardware, software and data of a computerized system. A large measure of computer security is simply keeping the computer system's information secure. In broader terms, computer security can be thought of as the protection of the computer and its r ...
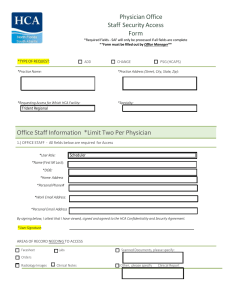
Physician Office Staff Security Access Form Office Staff Information
... I will not disclose or discuss any Confidential Information with others, including friends or family, who do not have a need to know it. I will not take media or documents containing Confidential Information home with me unless specifically authorized to do so as part of my job. 8. I will not publis ...
... I will not disclose or discuss any Confidential Information with others, including friends or family, who do not have a need to know it. I will not take media or documents containing Confidential Information home with me unless specifically authorized to do so as part of my job. 8. I will not publis ...
www.itgovernance.co.uk/training
... People are your weakest link – Strengthen awareness to improve the robustness of your ISMS Training aids are a tool for getting general staff involved in discussing and understanding the sometimes complex data security issues which might impinge on how they work – and to do so in a low impact, low p ...
... People are your weakest link – Strengthen awareness to improve the robustness of your ISMS Training aids are a tool for getting general staff involved in discussing and understanding the sometimes complex data security issues which might impinge on how they work – and to do so in a low impact, low p ...
Addressing security threats and vulnerabilities
... Dial-in via phone lines Hacking through security controls Internet ...
... Dial-in via phone lines Hacking through security controls Internet ...
HUNTING-AS-A-SERVICE By Accenture, Powered by Endgame
... of money into infrastructure security technology and resources, organizations have fallen far short of gaining control over cyber threats. Today, most security monitoring approaches are alert-driven and reactive. Operators wait for evidence of a breach before security analysts take action. This appr ...
... of money into infrastructure security technology and resources, organizations have fallen far short of gaining control over cyber threats. Today, most security monitoring approaches are alert-driven and reactive. Operators wait for evidence of a breach before security analysts take action. This appr ...
Access Security Requirements
... Access Security Requirements We must work together to protect the privacy and information of consumers. The following information security measures are designed to reduce unauthorized access to consumer information. It is your responsibility to implement these controls. If you do not understand thes ...
... Access Security Requirements We must work together to protect the privacy and information of consumers. The following information security measures are designed to reduce unauthorized access to consumer information. It is your responsibility to implement these controls. If you do not understand thes ...
TIM158-2013-Lectures 10-11
... 3. Compile and enforce an enterprise-wide policy for network firewalls and proxies that will prevent unauthorized downloads from Web sites both known or suspected to harbor spyware. 4. Provide users with passwords to access desktop computers, make sure they can only access systems with those passwor ...
... 3. Compile and enforce an enterprise-wide policy for network firewalls and proxies that will prevent unauthorized downloads from Web sites both known or suspected to harbor spyware. 4. Provide users with passwords to access desktop computers, make sure they can only access systems with those passwor ...
Network Infrastructure Security
... retrieval of programs and data used by a group of people. LAN software and practices also need to provide for the security of these programs and data. ...
... retrieval of programs and data used by a group of people. LAN software and practices also need to provide for the security of these programs and data. ...