* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download STUXNET - Clemson
Survey
Document related concepts
Transcript
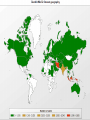
CPSC 420 : COMPUTER SECURITY PRINCIPLES MALWARE : Somya Verma Sharad Sharma STUXNET STUXNET A highly sophisticated computer worm that has spread through Iran, Indonesia and India was built to destroy operations at one target: possibly Iran's Bushehr nuclear reactor Prototype encountered in June 2009 Identified correctly in July 2010 The world’s first known cyber super weapon designed specifically to destroy a real-world target • • • • • • • • • • • • A study of the spread of Stuxnet by Symantec showed that the main affected countries were: China 6,000,000 (unconfirmed) Iran 62,867 Indonesia 13,336 India 6,552 United States 2,913 Australia 2,436 Britain 1,038 Malaysia 1,013 Pakistan 993 Finland 7 Germany 5 Stuxnet: It is BIG! • Exploited four zero day vulnerabilities of Windows(3/4 are now patched) • Large Size • Written in different programming languages • Digitally signed • Can update itself • Possibly took India's INSAT-4B Satellite out of action • Target oriented weapon Nation-State Behind Stuxnet! Operations: • Targets Siemens Software Systems (SCADA) • Finds out the PLC device • Injects Code Removal & Precautionary Measures: • Siemens has released a detection and removal tool for Stuxnet. • Be up to date and vigilante for patches. Other recommendations should also be standard fare for securing any IT environment: • Don’t allow people to use servers and mission-critical systems for web browsing, email, etc. • Enforce a high level of security for contractors and support vendors, both locally and remotely. • Remove or restrict access to shared network folders. • Only allow secure remote access methods, do not allow credentials to be transmitted in clear text. • Segment your network, separate systems from each other and use ACL’s to restrict traffic between zones. Israel Behind Stuxnet ? “MYRTUS”: Refers to Myrtle tree, or Hadassah in Hebrew (Jewish Queen) OR "My RTUs" — a management feature of SCADA Number 19790509 : refers to 19 May 09, the execution date of Habib Elghanian Iranian reaction With over 30,000 IP Addresses affected (and increasing) Iran is baffled and bluntly blames The United States Of America and Israel Moreover, three new versions of the virus have been recorded when attempts to clean the infected computers failed Cyber Warfare: Cold War Doctrines Needed for Cyber Warfare (October 15th) At the recent RSA Europe conference held in London, former US Homeland Security secretary Michael Chertoff has called on countries to develop doctrines to deal with cyber warfare in the same way cold war doctrines were developed for nuclear conflict. He told delegates at the conference that over 100 countries are now actively involved in cyber espionage and cyber attacks and that clear rules of engagement need to be defined. While stating that countries should be able to respond to cyber attacks "with overwhelming force," he added countries need not "respond to virtual attacks with real attacks but I do think it's important to define when and how it might be appropriate to respond. Everyone needs to understand to rules of the game." Acknowledging that attribution of attacks is difficult Mr Chertoff posited that countries that are victims of persistent attacks against their critical infrastructure should be permitted to incapacitate the platform used as the source of the attack, regardless of who is controlling the attack. Questions? • Why use Windows OS for Nuclear Power Plants? • Why hook these plants to the internet? • Who can be behind the Stuxnet Virus?