Pan-Oston Company, a Houchens Industries Employee Owned
... Ensures that all computers and associated equipment are operational at all times Monitors hardware systems using operating systems and executes daily backups Performance duties associated with batch processing of jobs and distributes appropriate reports Solves commonly occurring operations problems ...
... Ensures that all computers and associated equipment are operational at all times Monitors hardware systems using operating systems and executes daily backups Performance duties associated with batch processing of jobs and distributes appropriate reports Solves commonly occurring operations problems ...
Trojan Horse
... 1. Scan the network to: • locate which IP addresses are in use, • what operating system is in use, • what TCP or UDP ports are “open” (being listened to by Servers). 2. Run “Exploit” scripts against open ports 3. Get access to Shell program which is “suid” (has “root” ...
... 1. Scan the network to: • locate which IP addresses are in use, • what operating system is in use, • what TCP or UDP ports are “open” (being listened to by Servers). 2. Run “Exploit” scripts against open ports 3. Get access to Shell program which is “suid” (has “root” ...
cisco.camre.ac.uk
... sizes, from those which only cover viruses, trojans and worms to comprehensive integrated security suites that interact with a firewall and the operation system. Anti-virus checking system are only as good as the databases (dictionaries/dat files) ensure these are kept up to data AV software runs in ...
... sizes, from those which only cover viruses, trojans and worms to comprehensive integrated security suites that interact with a firewall and the operation system. Anti-virus checking system are only as good as the databases (dictionaries/dat files) ensure these are kept up to data AV software runs in ...
BUS 352 Week 4 Discussion 2 (Security components)
... Your businesses network border is the point where your organizations managed network interfaces with un-trusted networks. From a defense in depth perspective, the network perimeter encompasses every point where the internal network is connected to networks and hosts that are not managed by the organ ...
... Your businesses network border is the point where your organizations managed network interfaces with un-trusted networks. From a defense in depth perspective, the network perimeter encompasses every point where the internal network is connected to networks and hosts that are not managed by the organ ...
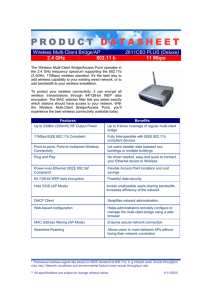
Wireless Multi-Client Bridge/AP 2611CB3 PLUS (Deluxe) 2.4 GHz
... To protect your wireless connectivity, it can encrypt all wireless transmissions through 64/128-bit WEP data encryption. The MAC address filter lets you select exactly which stations should have access to your network. With the Wireless Multi-Client Bridge/Access Point, you'll experience the best wi ...
... To protect your wireless connectivity, it can encrypt all wireless transmissions through 64/128-bit WEP data encryption. The MAC address filter lets you select exactly which stations should have access to your network. With the Wireless Multi-Client Bridge/Access Point, you'll experience the best wi ...
Basic Network Concepts
... between two points, and since the quickest path between two points may change over time as a function of network traffic and other factors), the packets that make up a particular data stream may not all take the same route. • Furthermore, they may not arrive in the order they were sent, if they even ...
... between two points, and since the quickest path between two points may change over time as a function of network traffic and other factors), the packets that make up a particular data stream may not all take the same route. • Furthermore, they may not arrive in the order they were sent, if they even ...
Network Tomography Based on Flow Level Measurements
... Restricted power supply Battery, DoS, selfish node ...
... Restricted power supply Battery, DoS, selfish node ...
The Internet and the World Wide Web
... 128.195.4.228 http://whatismyipaddress.com/ Originally, the first 8 bits specified the network, and the remaining 24 bits designated the computer on that network New version of IP (v6) has 64 bit addresses http://www.nytimes.com/2011/02/15/technology/15internet.html? scp=1&sq=internet%20addresses&st ...
... 128.195.4.228 http://whatismyipaddress.com/ Originally, the first 8 bits specified the network, and the remaining 24 bits designated the computer on that network New version of IP (v6) has 64 bit addresses http://www.nytimes.com/2011/02/15/technology/15internet.html? scp=1&sq=internet%20addresses&st ...
Secure Network Routing: Ariadne and Skipchains
... – Rice: less than 1m with 50% error indoors – Place Lab: 15-30m with 50% error outdoors • Need (generally) at least 3 APs ...
... – Rice: less than 1m with 50% error indoors – Place Lab: 15-30m with 50% error outdoors • Need (generally) at least 3 APs ...
COMP10023 - UWS Mahara
... Note that by default one option is correct unless you are instructed to choose two. Two points for each question. When there are two correct options, one point for each correct option and zero points if more options are selected than required. Please circle your answer(s). ...
... Note that by default one option is correct unless you are instructed to choose two. Two points for each question. When there are two correct options, one point for each correct option and zero points if more options are selected than required. Please circle your answer(s). ...
Assignment # 3 - UNT Class Server
... based is used to keep a network secure. The primary goal of a firewall is to analyze all incoming traffic and to analyze the data packets to make sure they are not harmful. The firewall is like a bridge between the users network which assumed to be secure and also another network like the internet t ...
... based is used to keep a network secure. The primary goal of a firewall is to analyze all incoming traffic and to analyze the data packets to make sure they are not harmful. The firewall is like a bridge between the users network which assumed to be secure and also another network like the internet t ...
common network terms - Amazon Web Services
... processing system. Inputs are the signals or data received by the system, and outputs are the signals or data sent from it. IOS – Internetworking Operating System IOS Cisco operating system software that runs the switches and routers. IP Internet Protocol. The network layer protocol in the TCP/IP st ...
... processing system. Inputs are the signals or data received by the system, and outputs are the signals or data sent from it. IOS – Internetworking Operating System IOS Cisco operating system software that runs the switches and routers. IP Internet Protocol. The network layer protocol in the TCP/IP st ...
Security Resume - Kirubha Shankar Murugesan
... Constructed a network topology with firewalls, switches, VLANS and routers with proper subnet masking and IP addressing for a small firm consisting of four departments. Experience with networking protocols such as BGP, OSPF, etc. Network Security Tools and Algorithms(Python): Jan 2016 - Apr 2016 ...
... Constructed a network topology with firewalls, switches, VLANS and routers with proper subnet masking and IP addressing for a small firm consisting of four departments. Experience with networking protocols such as BGP, OSPF, etc. Network Security Tools and Algorithms(Python): Jan 2016 - Apr 2016 ...
Linux Networking
... immediately so the user doesn’t see a login prompt. The PPP (CHAP/PAP) authorization is built into the protocol. NAT (Network Address Translation) will allow the linux box to take packets from systems on an internal (nonroutable) address and translate those requests to the address of the router inte ...
... immediately so the user doesn’t see a login prompt. The PPP (CHAP/PAP) authorization is built into the protocol. NAT (Network Address Translation) will allow the linux box to take packets from systems on an internal (nonroutable) address and translate those requests to the address of the router inte ...
Common Computer Terminology - Mr-Johnsons
... Most operating systems use a GUI. Graphical User Interface (GUI):displays images and pictures that allow the user to interact with a computer easily. Example of an Operating System (Windows XP) ...
... Most operating systems use a GUI. Graphical User Interface (GUI):displays images and pictures that allow the user to interact with a computer easily. Example of an Operating System (Windows XP) ...
Networking
... and a physical address called a MAC address. Each NIC is given an address at the factory that is the device’s physical address or MAC address. No two NIC devices will ever have the same MAC address. ...
... and a physical address called a MAC address. Each NIC is given an address at the factory that is the device’s physical address or MAC address. No two NIC devices will ever have the same MAC address. ...
Presentation Slides
... By transmitting information through radio waves a Wireless LAN can make traditional security measure obsolete. ...
... By transmitting information through radio waves a Wireless LAN can make traditional security measure obsolete. ...
Proposal Presentation
... Product will be open source and will integrate several available technologies ...
... Product will be open source and will integrate several available technologies ...
Firewall Categorization Methods
... Either block or allow transmission of packets of information based on criteria such as port, IP address, and protocol Review the header, strip it off, and replace it with a new header before sending it to a specific location within the network ...
... Either block or allow transmission of packets of information based on criteria such as port, IP address, and protocol Review the header, strip it off, and replace it with a new header before sending it to a specific location within the network ...