* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Trojan Horse
Asynchronous Transfer Mode wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Computer network wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Airborne Networking wikipedia , lookup
Wireless security wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
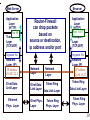
Network tap wikipedia , lookup
Computer security wikipedia , lookup
Deep packet inspection wikipedia , lookup
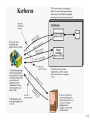
Distributed firewall wikipedia , lookup
Internet protocol suite wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Objectives of Data Security (relative to unauthorized persons) Privacy - not readable • Permanent - not alterable (can't edit, delete) • Reliable - (changes detectable) But the data must be accessible to persons authorized to: • Read, edit, add, delete Probably over a network, possibly over the Internet. 1 Attacks, Services, and Mechanisms * Security Attack: Any action that compromises the security of information. * Security Mechanism: A mechanism that is designed to detect, prevent, or recover from a security attack. * Security Service: A service that enhances the security of data processing systems and information transfers. A security service makes use of one or more security mechanisms. 2 3 4 Security Services * Confidentiality (privacy) * Authentication (who created or sent the data) * Integrity (has not been altered) * Non-repudiation (the order is final) * Access control (prevent misuse of resources) * Availability (permanence, non-erasure) - Denial of Service Attacks - Virus that deletes files 5 Viruses, Worms, and Trojan Horses Virus - code that copies itself into other programs Payload - harmful things it does, after it has had time to spread. Worm - a program that replicates itself across the network (usually riding on email messages or attached documents (e.g., macro viruses). Trojan Horse - instructions in an otherwise good program that cause bad things to happen (sending your data or password to an attacker over the net). Logic Bomb - malicious code that activates on an event (e.g., date). Trap Door (or Back Door) - undocumented entry point written into code for debugging that can allow unwanted users. 6 Virus Protection Have a well-known virus protection program, configured to scan disks and downloads automatically for known viruses. Do not execute programs (or "macro's") from unknown sources (e.g., PS files, HyperCard files, MS Office documents, Java, ...), if you can help it. Avoid the most common operating systems and email programs, if possible. 7 Password Gathering Look under keyboard, telephone etc. Look in the Rolodex under “X” and “Z” Call up pretending to from “micro-support,” and ask for it. “Snoop” a network and watch the plaintext passwords go by. Tap a phone line - but this requires a very special modem. Use a “Trojan Horse” program to record key stokes. 8 The Stages of a Network Intrusion 1. Scan the network to: • locate which IP addresses are in use, • what operating system is in use, • what TCP or UDP ports are “open” (being listened to by Servers). 2. Run “Exploit” scripts against open ports 3. Get access to Shell program which is “suid” (has “root” privileges). 4. Download from Hacker Web site special versions of systems files that will let Cracker have free access in the future without his cpu time or disk storage space being noticed by auditing programs. 5. Use IRC (Internet Relay Chat) to invite friends to the feast. 9 Browser Web Server Application Layer (HTTP) Port 80 Transport Layer (TCP,UDP) Segment No. Network Layer (IP) IP Address 130.207.22.5 E'net Data Link Layer Ethernet Phys. Layer Router-Firewall can drop packets based on source or destination, ip address and/or port Network Layer Network Layer Token Ring E'net Data Link Layer Data Link Layer E'net Phys. Layer Token Ring Phys. Layer Application Layer (HTTP) Port 31337 Transport Layer (TCP,UDP) Segment No. Network Layer (IP) IP Address 24.88.15.22 Token Ring Data-Link Layer Token Ring Phys. Layer 10 Policy No outside Web access. Firewall Setting Drop all outgoing packets to any IP, Port 80 Outside connections to Public Web Server Only. Drop all incoming TCP SYN packets to any IP except 130:207:244.203, port 80 Prevent Web-Radios from eating up the available bandwidth. Drop all incoming UDP packets - except DNS and Router Broadcasts. Prevent your network from being used for a Smuft DoS attack. Drop all ICMP packets going to a “broadcast” address (130.207.255.255 or 130.207.0.0). Prevent your network from being tracerouted or scanned. Drop all incoming ICMP, UDP, or TCP echorequest packets, drop all packets with TTL < 5. 11 PGP (Pretty Good Privacy) -> GPG From "PGP Freeware for MacOS, User's Guide" Version 6.5, Network Associates, Inc., www.pgp.com 12 Access Control Today almost all systems are protected only by a simple password that is typed in, or sent over a network in the clear.Techniques for guessing passwords: 1. Try default passwords. 2. Try all short words, 1 to 3 characters long. 3. Try all the words in an electronic dictionary(60,000). 4. Collect information about the user’s hobbies, family names, birthday, etc. 5. Try user’s phone number, social security number, street address, etc. 6. Try all license plate numbers (123XYZ). Prevention: Enforce good password selection (c0p31an6) 13 Kerberos 14