* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Local Area Networks
Parallel port wikipedia , lookup
Wireless security wikipedia , lookup
Net neutrality law wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
TCP congestion control wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Airborne Networking wikipedia , lookup
Computer network wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Network tap wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Distributed firewall wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
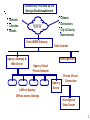
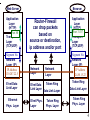
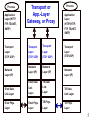
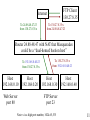
Computer System Evolution Central Data Processing System: - with directly attached peripherals (card reader, magnetic tapes, line printer). Local Area Networks: - connects PC’s (in “terminal emulation” mode), remote terminals (next building) and mini-computers. Premises Network: - connects LANs and LAN-attached devices to each other. Enterprise-wide Network: - leased data lines (T1, DS-3) connect various offices. Internet Connectivity: - initially for email, now for Web access, e-commerce, ... . Makes the world accessible, but now the world also has access to you. 1 Connectivity Provided by the Georgia Backbone Network • Schools • Libraries • Kiosks WWW • Citizens • Contractors • City & County Governments State WWW Gateway State Internet Agency Gateway & Web Server Other Agencies Agency Virtual Private Network LANs at Agency Offices across Georgia Agency Server Private Virtual Connection Non-Agency State Server 2 Agency Firewall -- Protects Protects Agency Agency Subnets Subnets from Unwanted Connections Subnet 1 Subnet 2 Gateway WAN Gateway Firewalls (and many routers) can reject: • Packets with certain source and destination addresses • Packets with certain high-level protocols (UDP, Telnet) Proxy Servers - for specific applications • Email messages assembled and inspected, then passed to internal email server machine. Prevent Cyber Loafing - Exploring the Internet for fun. 3 Browser Web Server Application Layer (HTTP) Port 80 Transport Layer (TCP,UDP) Segment No. Network Layer (IP) IP Address 130.207.22.5 E'net Data Link Layer Ethernet Phys. Layer Router-Firewall can drop packets based on source or destination, ip address and/or port Network Layer Network Layer Token Ring E'net Data Link Layer Data Link Layer E'net Phys. Layer Token Ring Phys. Layer Application Layer (HTTP) Port 31337 Transport Layer (TCP,UDP) Segment No. Network Layer (IP) IP Address 24.88.15.22 Token Ring Data-Link Layer Token Ring Phys. Layer 4 Process Application Layer (HTTP, FTP, TELNET, SMTP) Transport or App.-Layer Gateway, or Proxy Transport Transport Layer Layer (TCP, UDP) (TCP, UDP) Network Network Layer (IP) Layer (IP) E'net Data TR Data E'net Data Link Layer Link Link Layer Layer E'net Phys. Layer E'net Phys. TR Phys. Layer Layer Transport Layer (TCP, UDP) Network Layer (IP) Process Application Layer (HTTP(HTTP, FTP, TELNET, SMTP) Transport Layer (TCP,UDP) Network Layer (IP) TR Data Link Layer TR Phys. Layer 5 Policy No outside Web access. Firewall Setting Drop all outgoing packets to any IP, Port 80 Outside connections to Public Web Server Only. Drop all incoming TCP SYN packets to any IP except 130:207:244.203, port 80 Prevent Web-Radios from eating up the available bandwidth. Drop all incoming UDP packets - except DNS and Router Broadcasts. Prevent your network from being used for a Smuft DoS attack. Drop all ICMP packets going to a “broadcast” address (130.207.255.255 or 130.207.0.0). Prevent your network from being tracerouted or scanned. Drop all incoming ICMP, UDP, or TCP echorequest packets, drop all packets with TTL < 5. 6 Firewall Attacks Firewall Defense IP Internal-Address Spoofing. Drop all incoming packets with local address. Source Routing (External Spoof). Drop all IP packets with Source-Routing Option. Tiny Fragment Attacks. Drop all incoming packets with small offset. 2nd-Fragment Probes. Assemble IP fragments (hard work). SYN-ACK Probes. Be “Stateful” -keep track of TCP outgoing SYN packets (start of all TCP connections) (hard work). 7 A Firewall is a single point that a Network Administrator can control, even if individual computers are managed by workers or departments. ------Over half of corporate computer misfeasance is caused by employees who are already behind the main firewall. Solution 1 - isolate subnets with firewalls (usually routers or Ethernet switches with “filter” capabilities). Protect Finance from Engineering. Solution 2 - implement “IP Chains” to limit access to individual computers at the lowest protocol level possible, to specific hosts and subnets. 8 IP Chains /etc/hosts.deny ALL:ALL /etc/hosts.allow in.telnetd: 199.77.146 24.88.154.17 in.ftpd: 199.77.146.19 199.77.146.102 UNIX and Linux computers allow network contact to be limited to individual hosts or subnets (199.77.146 means 199.77.146.any). Above, telnet connection is available to all on the 199.77.146.0 subnet, and a single off-subnet host, 24.88.154.17 FTP service is available to only to two local hosts, .19 and .102. The format for each line is “daemon:host-list” 9 Router Setup with Network Address Translation (NAT) Addresses 10.0.0.0 and 192.168.0.0 reserved for private networks. FTP Client 130.27.8.35 Internet To 24.88.48.47:23 from 130.27.8.35:x To 130.27.8.35:x from 24.88.48.47:23 Router 24.88.48.47 with NAT that Masquerades could be a “dual-homed bastion host” To 192.168.0.40:23 from 130.27.8.35:x Host 192.168.0.10 Web Server port 80 Host 192.168.0.20 To 130.27.8.35:x from 192.168.0.40:23 Host 192.168.0.30 Host 192.168.0.40 FTP Server port 23 Note: x is a high port number, 1024-65,535 11 Web Host 130.27.8.35 Internet To 24.88.48.47:x from 130.27.8.35:80 To 130.27.8.35:80 from 24.88.48.47:x Router 24.88.48.47 with NAT that Masquerades To 192.168.0.20:x from 130.27.8.35:80 Host 192.168.0.10 Web Server port 80 Web Client 192.168.0.20 To 130.27.8.35:80 from 192.168.0.20:x Host 192.168.0.30 Host 192.168.0.40 FTP Server port 23 12