Ch06-Firewalls
... 1. The client connects to the server via a TCP session. 2. The client and server exchange information on administrative details, such as supported encryption methods and their protocol version, each choosing a set of protocols that the other supports. 3. The client and server initiate a secret-key e ...
... 1. The client connects to the server via a TCP session. 2. The client and server exchange information on administrative details, such as supported encryption methods and their protocol version, each choosing a set of protocols that the other supports. 3. The client and server initiate a secret-key e ...
Multimedia Application Production
... Appear to be harmless programs When they run, install programs on the computer that can be harmful Worm Acts as a free agent, replicating itself numerous times in an effort to overwhelm systems Succeeding with Technology ...
... Appear to be harmless programs When they run, install programs on the computer that can be harmful Worm Acts as a free agent, replicating itself numerous times in an effort to overwhelm systems Succeeding with Technology ...
monitor
... • Control Framework: A control framework is a set of controls that protects data within the IT infrastructure of a business or other entity. • Framework: an arrangement of parts that provides a form, or structure, to the whole. ...
... • Control Framework: A control framework is a set of controls that protects data within the IT infrastructure of a business or other entity. • Framework: an arrangement of parts that provides a form, or structure, to the whole. ...
6 - Department of Accounting and Information Systems ACIS | Pamplin
... Installing Internetwork connections requires leased lines or other data channels; these connections are usually secured under requirements of formal service agreement When individuals seek to connect to organization’s network, more flexible option must be provided Options such as virtual priva ...
... Installing Internetwork connections requires leased lines or other data channels; these connections are usually secured under requirements of formal service agreement When individuals seek to connect to organization’s network, more flexible option must be provided Options such as virtual priva ...
2012 Bond Planning Technology Project Update
... student use, additional software tools, and improved data analysis capabilities Significant investment in Computer & Devices Additional investment in educational technology innovation ...
... student use, additional software tools, and improved data analysis capabilities Significant investment in Computer & Devices Additional investment in educational technology innovation ...
Resume - OPResume.com
... Provided exceptional customer service and technical support for internal and external voice and data product customers. Troubleshoot hardware and software issues and identify network/applications issues. Provide detailed information on how to set up/configure data and voice products as well as assis ...
... Provided exceptional customer service and technical support for internal and external voice and data product customers. Troubleshoot hardware and software issues and identify network/applications issues. Provide detailed information on how to set up/configure data and voice products as well as assis ...
SANDS CORP CYBER JOB
... The SOC cyber security analyst, Level 1 is a member of the cyber security operations team and works closely with the other members of the cyber security team in support of a comprehensive cyber security program. This role is an entry level analyst that is responsible for monitoring various cyber sec ...
... The SOC cyber security analyst, Level 1 is a member of the cyber security operations team and works closely with the other members of the cyber security team in support of a comprehensive cyber security program. This role is an entry level analyst that is responsible for monitoring various cyber sec ...
Managing the Digital Firm
... 1. Achieving a sensible balance between too little control and too much. ...
... 1. Achieving a sensible balance between too little control and too much. ...
C06.InformationSecur.. - SIUE Computer Science
... are stored in a safe place to guard against data loss. With the advent of cloud computing, users are storing increasing amounts of data on Internet servers. E-mail, calendars, documents, photos, and other data are being saved in services provided by Google, Yahoo!, Microsoft, Flickr, Facebook, and o ...
... are stored in a safe place to guard against data loss. With the advent of cloud computing, users are storing increasing amounts of data on Internet servers. E-mail, calendars, documents, photos, and other data are being saved in services provided by Google, Yahoo!, Microsoft, Flickr, Facebook, and o ...
ISi-L - BSI
... between computers, though. Language (e.g. voice over IP) and multi-media contents (e.g. internet TV) are increasingly being transmitted using a standardised IP infrastructure. Another basic protocol is the Internet Control Message ICMP that provides functions for controlling the flow of data. For ex ...
... between computers, though. Language (e.g. voice over IP) and multi-media contents (e.g. internet TV) are increasingly being transmitted using a standardised IP infrastructure. Another basic protocol is the Internet Control Message ICMP that provides functions for controlling the flow of data. For ex ...
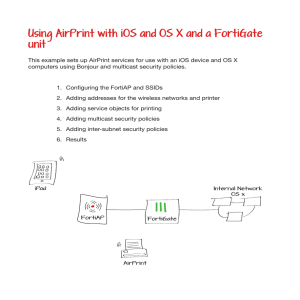
Using AirPrint with iOS and OS X and a FortiGate unit
... from WLAN1 and WLAN2 for iOS devices. For the first policy, set Incoming Interface to WLAN1, Source Address to the SSID1 IP, Outgoing Interface to WLAN2, and Destination Address to Bonjour. For the second policy, set Incoming Interface to WLAN2, Source Address to the SSID2 IP, Outgoing Interface to ...
... from WLAN1 and WLAN2 for iOS devices. For the first policy, set Incoming Interface to WLAN1, Source Address to the SSID1 IP, Outgoing Interface to WLAN2, and Destination Address to Bonjour. For the second policy, set Incoming Interface to WLAN2, Source Address to the SSID2 IP, Outgoing Interface to ...
module_70
... client connects to a SOCKS proxy server. The proxy server connects to the application server on behalf of the client, and relays data between the client and the application server. For the application server, the proxy server is the ...
... client connects to a SOCKS proxy server. The proxy server connects to the application server on behalf of the client, and relays data between the client and the application server. For the application server, the proxy server is the ...
Important Concepts.
... X.800 divides services into five categories and includes 14 specific services. 1. Authentication – It is concerned with assuring that a communication is authentic. ...
... X.800 divides services into five categories and includes 14 specific services. 1. Authentication – It is concerned with assuring that a communication is authentic. ...
Factsheet - KFSensor
... files and it comes preconfigured with all the major systems services required. KFSensor works by simulating systems services at the highest level of the OSI Network Model - the application layer. This enables it to make full use of Windows security mechanisms and networks libraries, reducing the ris ...
... files and it comes preconfigured with all the major systems services required. KFSensor works by simulating systems services at the highest level of the OSI Network Model - the application layer. This enables it to make full use of Windows security mechanisms and networks libraries, reducing the ris ...
Combat a range of potential data leakage threats with these ultra
... Solution: Unidirectional data flow is enforced by hardware “data diodes” so data isolation doesn’t rely on software integrity. Threat: Malicious modification of microprocessor software causing data to leak between ports. Solution: Microprocessors are one-time programmable and soldered on the board. ...
... Solution: Unidirectional data flow is enforced by hardware “data diodes” so data isolation doesn’t rely on software integrity. Threat: Malicious modification of microprocessor software causing data to leak between ports. Solution: Microprocessors are one-time programmable and soldered on the board. ...
Lecture 11
... failures, and other system events Application event logs record events that applications request be recorded Security event log records security-critical events such as logging in and out, system file accesses, and other events ...
... failures, and other system events Application event logs record events that applications request be recorded Security event log records security-critical events such as logging in and out, system file accesses, and other events ...
Lecture 10
... failures, and other system events Application event logs record events that applications request be recorded Security event log records security-critical events such as logging in and out, system file accesses, and other events ...
... failures, and other system events Application event logs record events that applications request be recorded Security event log records security-critical events such as logging in and out, system file accesses, and other events ...
Lecture 10
... failures, and other system events Application event logs record events that applications request be recorded Security event log records security-critical events such as logging in and out, system file accesses, and other events ...
... failures, and other system events Application event logs record events that applications request be recorded Security event log records security-critical events such as logging in and out, system file accesses, and other events ...
Operating System Security Fundamentals
... • Main component of operating system security environment • Operating system core utilities • Used to gain access to the OS and its features • Include ...
... • Main component of operating system security environment • Operating system core utilities • Used to gain access to the OS and its features • Include ...
Accepable Use and User Policies - Information Systems and Internet
... http://www.information-security-policies-and-standards.com ...
... http://www.information-security-policies-and-standards.com ...
Chapter 4
... Plug and Play (PnP) — A service that allows the Windows operating system to automatically detect new hardware when it is installed on a computer. security vulnerability — A weakness or flaw in an information system that could be exploited to cause harm. slot time — The amount of time that a de ...
... Plug and Play (PnP) — A service that allows the Windows operating system to automatically detect new hardware when it is installed on a computer. security vulnerability — A weakness or flaw in an information system that could be exploited to cause harm. slot time — The amount of time that a de ...
abstract - Chennaisunday.com
... security might be the ability to provide trust and confidence to transactions over the Internet. To accommodate the scale of transactions across the Internet, some of ...
... security might be the ability to provide trust and confidence to transactions over the Internet. To accommodate the scale of transactions across the Internet, some of ...
Are Clouds Secure? - San Francisco Bay Area ISSA Chapter
... • Existing aspects of information security which are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor rehash unchanged practices ...
... • Existing aspects of information security which are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor rehash unchanged practices ...
Are Clouds Secure?
... • Existing aspects of information security which are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor rehash unchanged practices ...
... • Existing aspects of information security which are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor rehash unchanged practices ...