Cybersecurity Chapter 3 Test Review
... Sara, a security technician, has been asked to design a solution which will enable external users to have access to a Web server, while keeping the internal network unaffected by this access. Which of the following would BEST meet this objective? Place the Web server on a VLAN Place the Web server i ...
... Sara, a security technician, has been asked to design a solution which will enable external users to have access to a Web server, while keeping the internal network unaffected by this access. Which of the following would BEST meet this objective? Place the Web server on a VLAN Place the Web server i ...
Lecture 8 - Bhecker.com
... private and one public. The keys are mathematically related so that data encrypted with one key can be decrypted using only the other key • Message integrity: The ability to be certain that the message being sent arrives at the proper destination without being copied or changed ...
... private and one public. The keys are mathematically related so that data encrypted with one key can be decrypted using only the other key • Message integrity: The ability to be certain that the message being sent arrives at the proper destination without being copied or changed ...
Network Perimeter Defense
... • New processes are being transformed into electronic forms • New vulnerabilities and patches emerge • Event logs must be analyzed • Appropriate actions must be taken • Etc. ...
... • New processes are being transformed into electronic forms • New vulnerabilities and patches emerge • Event logs must be analyzed • Appropriate actions must be taken • Etc. ...
佛教孔仙洲紀念中學
... computing applications, such as word processing, photo-editing, e-mail and Internet access. Personal computers used as a client on a network are called workstations. There are two major categories of personal computers: desktop computers and notebook computers. A notebook computer, also called lapto ...
... computing applications, such as word processing, photo-editing, e-mail and Internet access. Personal computers used as a client on a network are called workstations. There are two major categories of personal computers: desktop computers and notebook computers. A notebook computer, also called lapto ...
File
... – Spyware is the name given to a variety of harmful programs that secretly install themselves on a computer without the user's consent. Once installed, this spyware software gathers information about the user, everything from personal data to Internet browsing habits. ...
... – Spyware is the name given to a variety of harmful programs that secretly install themselves on a computer without the user's consent. Once installed, this spyware software gathers information about the user, everything from personal data to Internet browsing habits. ...
Session 1 Framework
... • Create an archive of original media, configuration files, and security-related patches for all router and host operating systems and application software versions • Ensure that backup tools and procedures are working • Create a database of contact information • Select and install tools to use when ...
... • Create an archive of original media, configuration files, and security-related patches for all router and host operating systems and application software versions • Ensure that backup tools and procedures are working • Create a database of contact information • Select and install tools to use when ...
Lecture21 - The University of Texas at Dallas
... network events in order to discover the source of security attacks or other problem incidents. Network forensics systems can be one of two kinds: "Catch-it-as-you-can" systems, in which all packets passing through a certain traffic point are captured and written to storage with analysis being done ...
... network events in order to discover the source of security attacks or other problem incidents. Network forensics systems can be one of two kinds: "Catch-it-as-you-can" systems, in which all packets passing through a certain traffic point are captured and written to storage with analysis being done ...
Guide to Firewalls and Network Security with Intrusion Detection and
... Add complexity Require that you install and/or maintain a variety of firewalls ...
... Add complexity Require that you install and/or maintain a variety of firewalls ...
Chapter 1. Introduction to Data Communications
... redundant network that duplicates every network component, but in a different location. • Generally speaking, preventing disasters is difficult. The most fundamental principle is to decentralize the network resources. • Other steps depend on the type of disaster to be prevented. ...
... redundant network that duplicates every network component, but in a different location. • Generally speaking, preventing disasters is difficult. The most fundamental principle is to decentralize the network resources. • Other steps depend on the type of disaster to be prevented. ...
Chapter 1
... A system's Trust Model consists of the software and data upon which the system depends for system security. ...
... A system's Trust Model consists of the software and data upon which the system depends for system security. ...
Attacks and Mitigations
... – payload : malicious code carried by attack vectors -- spyware, Trojan-horses, dialers, destructive code and other malware. Some attacks deliver multiple payloads (warheads). – For example, worms attack through the network connection to get in. That's just the first step. Worms usually carry an ins ...
... – payload : malicious code carried by attack vectors -- spyware, Trojan-horses, dialers, destructive code and other malware. Some attacks deliver multiple payloads (warheads). – For example, worms attack through the network connection to get in. That's just the first step. Worms usually carry an ins ...
ACCEPTABLE USE POLICY Customer is expected to
... TeliaSonera agrees to use reasonable efforts to notify Customer of any violations of the AUP and to give Customer an opportunity to correct any violations before taking action, provided that TeliaSonera shall reserve the right to suspend or block Service in cases where TeliaSonera believes that its ...
... TeliaSonera agrees to use reasonable efforts to notify Customer of any violations of the AUP and to give Customer an opportunity to correct any violations before taking action, provided that TeliaSonera shall reserve the right to suspend or block Service in cases where TeliaSonera believes that its ...
LSD1518 - Control Cloud Data Access Privilege
... schemes based on the attribute-based encryption have been proposed to secure the cloud storage. However, most work focuses on the data contents privacy and the access control, while less attention is paid to the privilege control and the identity privacy. In this paper, we present a semi-anonymous p ...
... schemes based on the attribute-based encryption have been proposed to secure the cloud storage. However, most work focuses on the data contents privacy and the access control, while less attention is paid to the privilege control and the identity privacy. In this paper, we present a semi-anonymous p ...
Virtual Cyber Security Lab - Celtic-Plus
... 48 years experience, first and largest private telecom and software development company in Turkey ...
... 48 years experience, first and largest private telecom and software development company in Turkey ...
Operating System for the K computer
... The K computer, which is composed of a large number of hardware components, is a system required by various users to perform lengthy computations and it needs to be highly robust. In relation to hardware failures, for example, it is important to have reliability, availability and serviceability (RAS ...
... The K computer, which is composed of a large number of hardware components, is a system required by various users to perform lengthy computations and it needs to be highly robust. In relation to hardware failures, for example, it is important to have reliability, availability and serviceability (RAS ...
Indian Institute of Science Uses LiveBroadcast to Mark One Hundred
... The committee chose Tata Communications’ LiveBroadcast™ solution. The service was especially appropriate for the institute because it eliminated the need for expensive hardware and proprietary software and did not require users to download a special media player to view the live content, making it e ...
... The committee chose Tata Communications’ LiveBroadcast™ solution. The service was especially appropriate for the institute because it eliminated the need for expensive hardware and proprietary software and did not require users to download a special media player to view the live content, making it e ...
E-Commerce Security
... communications between applications. • A message is divided into pieces called packets. • Packets are numbered and may be transmitted by different routes. ...
... communications between applications. • A message is divided into pieces called packets. • Packets are numbered and may be transmitted by different routes. ...
Lecture 1 - WordPress.com
... Data Integrity - assurance that data received is as sent by an authorized entity Non-Repudiation - protection against denial by one of the parties in a communication Availability – resource accessible/usable ...
... Data Integrity - assurance that data received is as sent by an authorized entity Non-Repudiation - protection against denial by one of the parties in a communication Availability – resource accessible/usable ...
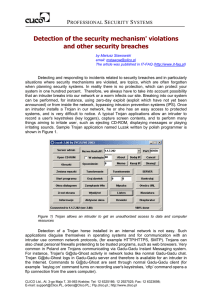
Detection of the security mechanism` violations and other
... detection break-ins (i.e. attacks resulting in unauthorized control over the system) and explaining security breaches. The analysis of events logged by IDP/IDS systems is difficult because Internet worms generate many attacks and therefore well-thought-of intruders' attacks can go unspotted. The ana ...
... detection break-ins (i.e. attacks resulting in unauthorized control over the system) and explaining security breaches. The analysis of events logged by IDP/IDS systems is difficult because Internet worms generate many attacks and therefore well-thought-of intruders' attacks can go unspotted. The ana ...
Beyond Data Breach Cyber Trends and Exposures â Mr. Jason Kelly
... commercial, institutional, and individual customers through one of the most extensive worldwide property-casualty networks of any insurer. In addition, AIG companies are leading providers of life insurance and retirement services in the United States. AIG common stock is listed on the New York Stock ...
... commercial, institutional, and individual customers through one of the most extensive worldwide property-casualty networks of any insurer. In addition, AIG companies are leading providers of life insurance and retirement services in the United States. AIG common stock is listed on the New York Stock ...
TECHNOLOGY-DRIVEN METRICS
... daily. Problem fixes are verified through additional scans. Vulnerability scanning tools (updated) for: wireless, server, endpoint, etc. Automated patch management tools notify via email when all systems have been patched. ...
... daily. Problem fixes are verified through additional scans. Vulnerability scanning tools (updated) for: wireless, server, endpoint, etc. Automated patch management tools notify via email when all systems have been patched. ...
(Big) Data? - Cloud Security Alliance
... Cloud Security Alliance (CSA) Big Data Working Group (BDWG) Initiatives 1: Data analytics for ...
... Cloud Security Alliance (CSA) Big Data Working Group (BDWG) Initiatives 1: Data analytics for ...
Hong Kong Polytechnic University (PolyU) Course: Associate of
... NOTE: Students may not be able to use all the unspecified credit awarded and will need to seek academic advice at enrolment. Application of Credit Exemption to UOW Courses/Majors: A further 72 credit points (equivalent to a year and a half of full-time study) will be required to complete the followi ...
... NOTE: Students may not be able to use all the unspecified credit awarded and will need to seek academic advice at enrolment. Application of Credit Exemption to UOW Courses/Majors: A further 72 credit points (equivalent to a year and a half of full-time study) will be required to complete the followi ...
Document
... daily. Problem fixes are verified through additional scans. Vulnerability scanning tools (updated) for: wireless, server, endpoint, etc. Automated patch management tools notify via email when all systems have been patched. ...
... daily. Problem fixes are verified through additional scans. Vulnerability scanning tools (updated) for: wireless, server, endpoint, etc. Automated patch management tools notify via email when all systems have been patched. ...