Top 100 Network Security Tools
... This simple utility reads and writes data across TCP or UDP network connections. It is designed to be a reliable back-end tool that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and exploration tool, since it can create ...
... This simple utility reads and writes data across TCP or UDP network connections. It is designed to be a reliable back-end tool that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and exploration tool, since it can create ...
Distributed and Embedded Systems (DIES)
... (8) An RFID tag used to provide information about the product to which it is attached; ...
... (8) An RFID tag used to provide information about the product to which it is attached; ...
CIST 1601 Information Security Fundamentals
... It allows applications to access services or protocols to exchange data. Most programs, such as web browsers, interface with TCP/IP at this level. The most commonly used Application layer protocols are as follows: Hypertext Transfer Protocol is the protocol that is used by a web browser to communic ...
... It allows applications to access services or protocols to exchange data. Most programs, such as web browsers, interface with TCP/IP at this level. The most commonly used Application layer protocols are as follows: Hypertext Transfer Protocol is the protocol that is used by a web browser to communic ...
Employee Internet Use Monitoring and Filtering Policy
... that staff member, or self-help or health advice sites might identify a physical or mental health condition. By carrying out such activities using 1836 Technologies’s Internet access facilities, Staff consent to 1836 Technologies processing any sensitive personal data about them that may be revealed ...
... that staff member, or self-help or health advice sites might identify a physical or mental health condition. By carrying out such activities using 1836 Technologies’s Internet access facilities, Staff consent to 1836 Technologies processing any sensitive personal data about them that may be revealed ...
Incident Response and Honeypots
... • Reduce protection domain of attacker. • Problem: if defenders do not know what attacker is after, reduced protection domain may contain what the attacker is after. – Stoll created document that attacker d/led. – Download took several hours, during which the phone call was traced to Germany. ...
... • Reduce protection domain of attacker. • Problem: if defenders do not know what attacker is after, reduced protection domain may contain what the attacker is after. – Stoll created document that attacker d/led. – Download took several hours, during which the phone call was traced to Germany. ...
shuffling:improving data security in ad hoc networks based
... The work developed in [7] draws up the scenario of a group wishing to provide a secured session in a conference room without supporting any infrastructure. The approach describes that these is a Weak Password that the entire group will share (for example by writing it on a board). Then, each member ...
... The work developed in [7] draws up the scenario of a group wishing to provide a secured session in a conference room without supporting any infrastructure. The approach describes that these is a Weak Password that the entire group will share (for example by writing it on a board). Then, each member ...
Lecture12
... relationships between principals, transactions, and data items. As a short example, a user capable of certifying or creating a relation should not be able to execute the programs specified in that relation. 0 The model consists of two sets of rules: Certification Rules (C) and ...
... relationships between principals, transactions, and data items. As a short example, a user capable of certifying or creating a relation should not be able to execute the programs specified in that relation. 0 The model consists of two sets of rules: Certification Rules (C) and ...
Chapter 3 - Faculty Personal Homepage
... – Are updated with encrypted data every time the card is used – Used widely in Europe – Not widely used in the U.S. ...
... – Are updated with encrypted data every time the card is used – Used widely in Europe – Not widely used in the U.S. ...
LVRJ Case study
... Challenges: Limited visibility into user activity and controlling access to resources through ACLs and static IP addresses has gotten too complex to manage. Solution: Deploying the ConSentry Networks™ CS2400 Secure LAN Controller™ and InSight Manager™ to provide complete visibility into user activit ...
... Challenges: Limited visibility into user activity and controlling access to resources through ACLs and static IP addresses has gotten too complex to manage. Solution: Deploying the ConSentry Networks™ CS2400 Secure LAN Controller™ and InSight Manager™ to provide complete visibility into user activit ...
10.2 BASIC E-COMMERCE SECURITY ISSUES AND LANDSCAPE
... modification, or deletion of data or messages in transit. ...
... modification, or deletion of data or messages in transit. ...
Cyber Security Metrics
... No enterprise view of the risk profile exists to enable a robust and resilient cyber defense posture 1. Gather and correlate existing data on systems 2. Identify complete set of IT assets 3. Store and display information in central location Data is fused into a single picture of network devices base ...
... No enterprise view of the risk profile exists to enable a robust and resilient cyber defense posture 1. Gather and correlate existing data on systems 2. Identify complete set of IT assets 3. Store and display information in central location Data is fused into a single picture of network devices base ...
No Slide Title - ECE Users Pages - Georgia Institute of Technology
... • A Georgia Tech student uses their personal PC and a commercial ISP to do a port scan on a commercial web site. • A Georgia Tech student sends a “spoofed mail” from the school account that appears to come from another user. • A Georgia Tech student uses a school computer and password guessing softw ...
... • A Georgia Tech student uses their personal PC and a commercial ISP to do a port scan on a commercial web site. • A Georgia Tech student sends a “spoofed mail” from the school account that appears to come from another user. • A Georgia Tech student uses a school computer and password guessing softw ...
Computer and Information Security
... in severe disruption of services and losses • Systems connected by networks are more prone to attacks and also suffer more as a result of the ...
... in severe disruption of services and losses • Systems connected by networks are more prone to attacks and also suffer more as a result of the ...
Threats and Attacks
... § Mail bombing: also a DoS; attacker routes large quantities of e-mail to target § Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network § Social engineering: using social skills to convince p ...
... § Mail bombing: also a DoS; attacker routes large quantities of e-mail to target § Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network § Social engineering: using social skills to convince p ...
Incident Handling Applied Risk Management September 2002
... Step 5: Evaluation fool me once, shame on you ...
... Step 5: Evaluation fool me once, shame on you ...
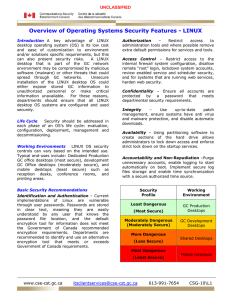
Overview of Operating Systems Security Features
... environment may be compromised by malicious software (malware) or other threats that could spread through GC networks. Unsecure installation of the LINUX desktop OS could either expose stored GC information to unauthorized personnel or make critical information unavailable. For these reasons, depart ...
... environment may be compromised by malicious software (malware) or other threats that could spread through GC networks. Unsecure installation of the LINUX desktop OS could either expose stored GC information to unauthorized personnel or make critical information unavailable. For these reasons, depart ...
Forrester: Email Marketing Vendor Wave
... • One of 12 providers capable of delivering on its vision for a centralized customer lifecycle marketing system • Noted for: ▸Messaging across digital channels ▸Messaging in context for different lifecycle phases ...
... • One of 12 providers capable of delivering on its vision for a centralized customer lifecycle marketing system • Noted for: ▸Messaging across digital channels ▸Messaging in context for different lifecycle phases ...
Computer security - University of London International Programmes
... Units 2 to 5 contain the core computer security theory of this module In Unit 2 you are introduced to the fundamental design principles of computer security. These will be referred to throughout the rest of this module. Unit 3 investigates the important topic of access control. You will be introduce ...
... Units 2 to 5 contain the core computer security theory of this module In Unit 2 you are introduced to the fundamental design principles of computer security. These will be referred to throughout the rest of this module. Unit 3 investigates the important topic of access control. You will be introduce ...
Lecture 5 - The University of Texas at Dallas
... Internet Edition communicates in clear text. Neither employs an encrypted files system” ...
... Internet Edition communicates in clear text. Neither employs an encrypted files system” ...
Operating System Security
... fewest objects needed for successful work – The system backup program may be allowed to bypass read restrictions on files, but it would not have the ability to modify files. – Need to Know” ...
... fewest objects needed for successful work – The system backup program may be allowed to bypass read restrictions on files, but it would not have the ability to modify files. – Need to Know” ...
Springfield Data Center Program Alignment
... Security Incident and Event Management system *Log Management: Collects, stores, and mines all network, security, and application information from IT infrastructures. * Threat Management: Correlates and detects threats across heterogeneous network and security technologies. * Compliance Management: ...
... Security Incident and Event Management system *Log Management: Collects, stores, and mines all network, security, and application information from IT infrastructures. * Threat Management: Correlates and detects threats across heterogeneous network and security technologies. * Compliance Management: ...
Computer Security: Principles and Practice, 1/e
... it sends an alert to the manager component that contains information about the unusual activity that was detected, as well as the specifics of the occurrence. The manager component issues a notification to the human operator. A response can be initiated automatically by the manager component or by t ...
... it sends an alert to the manager component that contains information about the unusual activity that was detected, as well as the specifics of the occurrence. The manager component issues a notification to the human operator. A response can be initiated automatically by the manager component or by t ...
Network Security - School of Computing and Engineering
... Activity prior to exfiltration • Information Security (IS) detected low levels of intrusive activity prior to exfiltration. – Seemed to be folcused on maintenance of their presence within the network – When detected IS would block the link. – Apparently intruders were able to open up other links un ...
... Activity prior to exfiltration • Information Security (IS) detected low levels of intrusive activity prior to exfiltration. – Seemed to be folcused on maintenance of their presence within the network – When detected IS would block the link. – Apparently intruders were able to open up other links un ...