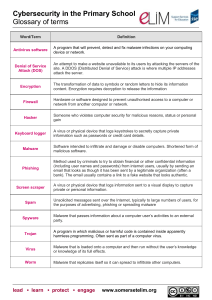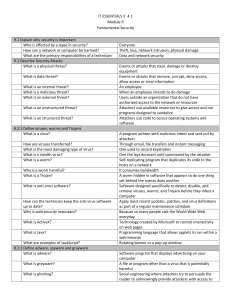
IT ESSENTIALS V. 4.1 Module 9 Fundamental Security 9.1 Explain
... When unsuccessful attempts have been made to access the system; user can no longer access the system Allows remote users to safely access resources as if their computer is physically attached to the local network encryption Data being transported on a network A program that runs on a computer to all ...
... When unsuccessful attempts have been made to access the system; user can no longer access the system Allows remote users to safely access resources as if their computer is physically attached to the local network encryption Data being transported on a network A program that runs on a computer to all ...
Computer Concepts And Applications CIS-107-TE
... 5.1 Computer security risks and types of cybercrime perpetrators; techniques to prevent unauthorized computer access and use; ways software manufacturersprotect against software piracy; options for backing up computer resources; issues surrounding information privacy (electronic profiles, cookie ...
... 5.1 Computer security risks and types of cybercrime perpetrators; techniques to prevent unauthorized computer access and use; ways software manufacturersprotect against software piracy; options for backing up computer resources; issues surrounding information privacy (electronic profiles, cookie ...
Types of Surveillance Technology Currently Used by Governments
... Aggregates numerous government watch-lists In 2005, TSDB had over 200,000 names, ranging from known terrorists to persons suspected of having some ties to terrorism Each name receives one of 28 codes, describing person’s connection to terrorism Names are categorized according to the actions users sh ...
... Aggregates numerous government watch-lists In 2005, TSDB had over 200,000 names, ranging from known terrorists to persons suspected of having some ties to terrorism Each name receives one of 28 codes, describing person’s connection to terrorism Names are categorized according to the actions users sh ...
Victims who were Hacked PowerPoint Presentation
... What Is An Anti-Virus Software? A software designed to be used on your computer to find, treat, remove and keep malwares away. It will keep all your computer data safe! ...
... What Is An Anti-Virus Software? A software designed to be used on your computer to find, treat, remove and keep malwares away. It will keep all your computer data safe! ...
Tool: Spector CNE Tool: Track4Win
... Track4Win monitors all computer activities and Internet use. With powerful network support, it can easily collect application running times (Figure 8-2), track Internet use information through the network, log this information in a database, analyze the information, and produce reports. The followin ...
... Track4Win monitors all computer activities and Internet use. With powerful network support, it can easily collect application running times (Figure 8-2), track Internet use information through the network, log this information in a database, analyze the information, and produce reports. The followin ...
business computer and network check list
... The internet connection is reliable and does not go down I have a second internet connection for 100% up time I have clean power. Power surges and sudden outages will not damage my servers and essential network equipment. I use a UPS on essential equipment When services on my server stop, they are d ...
... The internet connection is reliable and does not go down I have a second internet connection for 100% up time I have clean power. Power surges and sudden outages will not damage my servers and essential network equipment. I use a UPS on essential equipment When services on my server stop, they are d ...
CH 8 – Review - WordPress.com
... Botnet is short for robot network – True A person who runs a botnet is called a – botmaster Botnets are created using self-propagating software, which means that the software can – reproduce itself A good defense to prevent your computer from becoming a zombie is to – install and run antivirus softw ...
... Botnet is short for robot network – True A person who runs a botnet is called a – botmaster Botnets are created using self-propagating software, which means that the software can – reproduce itself A good defense to prevent your computer from becoming a zombie is to – install and run antivirus softw ...
Breaking Trust On The Internet
... code, or malware, which infected the computers of people who visited the website and required them to purchase antivirus software for $49.95 to regain control of their computers. If the users did not purchase the software, their computers immediately became flooded with pop-ups containing false "sec ...
... code, or malware, which infected the computers of people who visited the website and required them to purchase antivirus software for $49.95 to regain control of their computers. If the users did not purchase the software, their computers immediately became flooded with pop-ups containing false "sec ...
- Longwood Blogs
... Design, build , and test user interfaces using various JavaScript libraries Develop responsive and intuitive components to sort and analyze data Analyze and patch code vulnerabilities in web applications Follow agile practices to collaborate requirements and coordinate development Longwood U ...
... Design, build , and test user interfaces using various JavaScript libraries Develop responsive and intuitive components to sort and analyze data Analyze and patch code vulnerabilities in web applications Follow agile practices to collaborate requirements and coordinate development Longwood U ...
ITS_8_Security Vocab Answers
... length to preclude most hacking programs from cracking the password in a short period of time. Passwords should be changed periodically for these reasons. Keylogger A type of software that is capable of recording every keystroke you make on a keyboard and placing it into a log file, which is usually ...
... length to preclude most hacking programs from cracking the password in a short period of time. Passwords should be changed periodically for these reasons. Keylogger A type of software that is capable of recording every keystroke you make on a keyboard and placing it into a log file, which is usually ...
security_6
... an attack on a web site in which an attacker uses specialized software to send a flood of data packets to the target computer with the aim of overloading its resources. ...
... an attack on a web site in which an attacker uses specialized software to send a flood of data packets to the target computer with the aim of overloading its resources. ...
Open ended challenge rationale
... Hardware or software designed to prevent unauthorised access to a computer or network from another computer or network. ...
... Hardware or software designed to prevent unauthorised access to a computer or network from another computer or network. ...
Pan-Oston Company, a Houchens Industries Employee Owned
... Monitors hardware systems using operating systems and executes daily backups Performance duties associated with batch processing of jobs and distributes appropriate reports Solves commonly occurring operations problems and refers more complex problems to higher-level staff Monitors status of the net ...
... Monitors hardware systems using operating systems and executes daily backups Performance duties associated with batch processing of jobs and distributes appropriate reports Solves commonly occurring operations problems and refers more complex problems to higher-level staff Monitors status of the net ...
Document
... Promotion Ukrainian Web-masters and founders in Internet projects. Set up Ukraine to a new level in the provision of information services. receive the highest profit. ...
... Promotion Ukrainian Web-masters and founders in Internet projects. Set up Ukraine to a new level in the provision of information services. receive the highest profit. ...
Lec.4.Communication software and the internet
... • A set of computers connected together so that they can communicate is called a computer network. • This involves installing network cards in each computer. • Each computer is then connected through cabling to a central device called a hub. • The most commonly used protocol for establishing and ma ...
... • A set of computers connected together so that they can communicate is called a computer network. • This involves installing network cards in each computer. • Each computer is then connected through cabling to a central device called a hub. • The most commonly used protocol for establishing and ma ...
E-Surveillance and User Privacy
... • Sec. 403(c) of the USA-PATRIOT Act specifically requires the federal government to "develop and certify a technology standard that can be used to verify the identity of persons" applying for or seeking entry into the United States on a U.S. visa "for the purposes of conducting background checks, c ...
... • Sec. 403(c) of the USA-PATRIOT Act specifically requires the federal government to "develop and certify a technology standard that can be used to verify the identity of persons" applying for or seeking entry into the United States on a U.S. visa "for the purposes of conducting background checks, c ...