Computer Ethics
... other types of malware, adware, and spyware programs that do not have the reproductive ability. ...
... other types of malware, adware, and spyware programs that do not have the reproductive ability. ...
Artificial Intelligence Engineer
... analytics, and applications. Must have a working knowledge of advanced cybersecurity methods, and experience in applying those methods to a variety of applications. Must be flexible, able to move in new directions, and collaborate with our external partners to solve advanced problems. ...
... analytics, and applications. Must have a working knowledge of advanced cybersecurity methods, and experience in applying those methods to a variety of applications. Must be flexible, able to move in new directions, and collaborate with our external partners to solve advanced problems. ...
Are you looking for an easier way to initiate and
... two hosts and guaranteeing the delivery of data and packets in the correct order. ...
... two hosts and guaranteeing the delivery of data and packets in the correct order. ...
Security strategy
... All organisations suffer from breaches of security. These can range from innocent attempts to access restricted resources to deliberate and prolonged attempts on computer systems and networks. ...
... All organisations suffer from breaches of security. These can range from innocent attempts to access restricted resources to deliberate and prolonged attempts on computer systems and networks. ...
Social Studies
... Identify safe and responsible ways to use technology systems, the Internet including but not limited to social/professional networking, communication tools, and applications. Identify safe and responsible practices of social networking and electronic communication. Understand the meaning of legal ve ...
... Identify safe and responsible ways to use technology systems, the Internet including but not limited to social/professional networking, communication tools, and applications. Identify safe and responsible practices of social networking and electronic communication. Understand the meaning of legal ve ...
The Role of Security in an Introductory Course
... • Depends • 2 or 4 year school • Course of study ...
... • Depends • 2 or 4 year school • Course of study ...
Computer GEEK - Ideas
... Outlook “AutoComplete” email addresses are stored in the “Outlook.NK2” file which is normally hidden. Many people really appreciated that I could transfer these frequently used email addresses from their old computer. ...
... Outlook “AutoComplete” email addresses are stored in the “Outlook.NK2” file which is normally hidden. Many people really appreciated that I could transfer these frequently used email addresses from their old computer. ...
University of Arizona
... identify known viruses when they attempt to strike – Can prompt users to periodically collect new data ...
... identify known viruses when they attempt to strike – Can prompt users to periodically collect new data ...
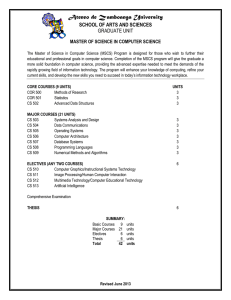
Master of Science in Computer Science
... The Master of Science in Computer Science (MSCS) Program is designed for those who wish to further their educational and professional goals in computer science. Completion of the MSCS program will give the graduate a more solid foundation in computer science, providing the advanced expertise needed ...
... The Master of Science in Computer Science (MSCS) Program is designed for those who wish to further their educational and professional goals in computer science. Completion of the MSCS program will give the graduate a more solid foundation in computer science, providing the advanced expertise needed ...
Computer Components
... to others without the owner’s permission. Virus is a program which instructs your computer to perform destructive activities. Spyware tracks a computer user’s Internet usage and send this data back to the company or person that create it. It is contained in other software. ...
... to others without the owner’s permission. Virus is a program which instructs your computer to perform destructive activities. Spyware tracks a computer user’s Internet usage and send this data back to the company or person that create it. It is contained in other software. ...
Chapter 5 Protecting Information Resources
... virus, worm, or other destructive code Triggered at a certain time or by an event ...
... virus, worm, or other destructive code Triggered at a certain time or by an event ...
Seminar Announcement - CS/NVC Home
... Department of Information and Software Engineering George Mason University Abstract: Continuous queries are those that produce continuous results on data streams. Such queries are useful in many application domains, including Network Management and Intrusion Detection, Web Monitoring, Sensor Network ...
... Department of Information and Software Engineering George Mason University Abstract: Continuous queries are those that produce continuous results on data streams. Such queries are useful in many application domains, including Network Management and Intrusion Detection, Web Monitoring, Sensor Network ...
Guide to Security - Cal Poly Pomona Foundation, Inc.
... identify known viruses when they attempt to strike – Can prompt users to periodically collect new data ...
... identify known viruses when they attempt to strike – Can prompt users to periodically collect new data ...
here - Penndel Mental Health Center
... This policy applies to all PMHC employees, contractors, vendors and agents with a Penndel Mental Health Center-owned or personally-owned computer or workstation connected to the Penndel Mental Health Center network. This policy applies to all end user initiated communications between Penndel Mental ...
... This policy applies to all PMHC employees, contractors, vendors and agents with a Penndel Mental Health Center-owned or personally-owned computer or workstation connected to the Penndel Mental Health Center network. This policy applies to all end user initiated communications between Penndel Mental ...
Online dating Virtual gaming Twitter LinkedIn Facebook Google +
... THE RAPID EVOLUTION OF INFORMATION TECHNOLOGY • “The sharing of information, using technology as an enabler, is a culture change that has been fully embraced by political, military, and the business communities.” • “If we do not develop robust capabilities to detect, expose, and hold accountable ...
... THE RAPID EVOLUTION OF INFORMATION TECHNOLOGY • “The sharing of information, using technology as an enabler, is a culture change that has been fully embraced by political, military, and the business communities.” • “If we do not develop robust capabilities to detect, expose, and hold accountable ...
Position: Senior IA/Security Specialist, (Computer Network Defense
... Job Description: The Senior IA/Security Specialist (CND) will perform System Administration lifecycle management of Computer Network Defense tools needed to sustain a robust cyber security management program and associated network defenses for NAVAIR networks. Responsibilities: • Conduct system admi ...
... Job Description: The Senior IA/Security Specialist (CND) will perform System Administration lifecycle management of Computer Network Defense tools needed to sustain a robust cyber security management program and associated network defenses for NAVAIR networks. Responsibilities: • Conduct system admi ...
Mullvad Barnprogram
... Mullvad Barnprogram - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while bene ...
... Mullvad Barnprogram - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while bene ...
Networking and System Administration (NaSA) Bachelor of Science in
... The Networking and System Administration major is a timely program aimed at preparing graduates for careers and research opportunities in all fields related to reliable and distributed network computing. Career Paths Include: ...
... The Networking and System Administration major is a timely program aimed at preparing graduates for careers and research opportunities in all fields related to reliable and distributed network computing. Career Paths Include: ...
Cisco Discovery 1 Module 08 Quiz Picture Descriptions
... by telephone by voice over IP phone through a person they know in common 3. A file is downloaded from the internet. After the user opens the downloaded file, the user’s hard drive crashes and all information on the computer is lost. What type of attack occurred? Worm, virus Trojan horse ...
... by telephone by voice over IP phone through a person they know in common 3. A file is downloaded from the internet. After the user opens the downloaded file, the user’s hard drive crashes and all information on the computer is lost. What type of attack occurred? Worm, virus Trojan horse ...
View Report - PDF
... Information Technology in writing or by email. Information Technology will unblock that site or category for that associate only. Information Technology will track approved exceptions and report on them upon request. 4.0 Enforcement The IT Security Officer will periodically review Internet use monit ...
... Information Technology in writing or by email. Information Technology will unblock that site or category for that associate only. Information Technology will track approved exceptions and report on them upon request. 4.0 Enforcement The IT Security Officer will periodically review Internet use monit ...