BUS 352 Week 4 Discussion 2 (Security components)
... customers, while at the same time providing prospective buyers with access to marketing materials on its Web site. Assuming that the business is responsible for running all these network components, what types of security components (for example, firewalls, VPN, etc.) could be used to ensure that th ...
... customers, while at the same time providing prospective buyers with access to marketing materials on its Web site. Assuming that the business is responsible for running all these network components, what types of security components (for example, firewalls, VPN, etc.) could be used to ensure that th ...
TS/SCI cleared Network Administrator for AF JWICS
... - Categorize and resolve network issues by validating, isolating, and correcting faults and verifying service restoral with customers. - Perform installation, troubleshooting, maintenance, and repair of network switches and routers, power, and computer data circuits and related apparatus/peripherals ...
... - Categorize and resolve network issues by validating, isolating, and correcting faults and verifying service restoral with customers. - Perform installation, troubleshooting, maintenance, and repair of network switches and routers, power, and computer data circuits and related apparatus/peripherals ...
Remote Access Policy
... your machine is connected to the Internet. VNC is free (released under the GNU General Public License) and it's available on most platforms. Original VNC distribution can be obtained at this site. ...
... your machine is connected to the Internet. VNC is free (released under the GNU General Public License) and it's available on most platforms. Original VNC distribution can be obtained at this site. ...
module 2 network security unit 1
... • A network security system typically relies on layers of protection and consists of multiple components including networking monitoring and security software in addition to hardware and appliances. All components work together to increase the overall security of the computer network. ...
... • A network security system typically relies on layers of protection and consists of multiple components including networking monitoring and security software in addition to hardware and appliances. All components work together to increase the overall security of the computer network. ...
Mapping - Syslab
... host towards a single host on a destination network. This technique only records an outgoing packet path – the incoming path is often different. ...
... host towards a single host on a destination network. This technique only records an outgoing packet path – the incoming path is often different. ...
Document
... Identities / access to system or network data source: http://markn.ca/2011/whaling/ ...
... Identities / access to system or network data source: http://markn.ca/2011/whaling/ ...
Module F - Columbus State University
... adjacent memory area, overwriting what was already there, including data or instructions. Malicious hackers have become proficient at leveraging such overflows to introduce their own code into programs, effectively hijacking the computer. At the same time, overflows occur when programmers do not i ...
... adjacent memory area, overwriting what was already there, including data or instructions. Malicious hackers have become proficient at leveraging such overflows to introduce their own code into programs, effectively hijacking the computer. At the same time, overflows occur when programmers do not i ...
IEEE CONFERENCE ON COMMUNICATION TECHNOLOGIES
... Military College of Signals (MCS), a Campus of National University of Sciences and Technology (NUST), Pakistan, is dedicated to advancing knowledge and educating students in science and technology. As part of its continuing pursuit for excellence in the domains of Telecommunications, Information Sec ...
... Military College of Signals (MCS), a Campus of National University of Sciences and Technology (NUST), Pakistan, is dedicated to advancing knowledge and educating students in science and technology. As part of its continuing pursuit for excellence in the domains of Telecommunications, Information Sec ...
Jaden Terry CIS 280 Final Network Security From browsing the
... There are many techniques of keeping a computer safe from mentioned attacks, such as Mac address filtering, Firewall, and WPA/WPA2. First, a firewall is a system that controls the incoming and outgoing traffic and determines whether or not packets should be allowed through. In the network layer, a f ...
... There are many techniques of keeping a computer safe from mentioned attacks, such as Mac address filtering, Firewall, and WPA/WPA2. First, a firewall is a system that controls the incoming and outgoing traffic and determines whether or not packets should be allowed through. In the network layer, a f ...
Research Paper
... collect private electronic data belonging to users of major internet services. It used the legal authority gained from the Patriot Act as well as the Foreign Intelligence Surveillance Act (FISA). Under the program data was gathered from servers of major US based companies such as Microsoft, Yahoo!, ...
... collect private electronic data belonging to users of major internet services. It used the legal authority gained from the Patriot Act as well as the Foreign Intelligence Surveillance Act (FISA). Under the program data was gathered from servers of major US based companies such as Microsoft, Yahoo!, ...
This Article argues that intellectual property law stifles critical
... vulnerabilities. Researchers who discover flaws often face legal threats based on IP claims if they reveal findings to anyone other than the software’s vendor. Externalities and network effects cause vendors’ incentives to diverge from those that are socially optimal. Unlike previous scholarship, th ...
... vulnerabilities. Researchers who discover flaws often face legal threats based on IP claims if they reveal findings to anyone other than the software’s vendor. Externalities and network effects cause vendors’ incentives to diverge from those that are socially optimal. Unlike previous scholarship, th ...
Network Device Security Options
... SNMP were used to configure and monitor remote devices. The latest version, SNMP v3, offers enhancements to user authentication and data encryption that deliver greater security features to protect customer data and network assets. When activated, SNMP ...
... SNMP were used to configure and monitor remote devices. The latest version, SNMP v3, offers enhancements to user authentication and data encryption that deliver greater security features to protect customer data and network assets. When activated, SNMP ...
Neal Ziring Very Short Bio
... Mr. Neal Ziring is the Technical Director for the National Security Agency’s Capabilities Directorate, serving as a technical advisor to the Capabilities Director, Deputy Director, and other senior leadership. Mr. Ziring is responsible for setting the technical direction across many parts of the cap ...
... Mr. Neal Ziring is the Technical Director for the National Security Agency’s Capabilities Directorate, serving as a technical advisor to the Capabilities Director, Deputy Director, and other senior leadership. Mr. Ziring is responsible for setting the technical direction across many parts of the cap ...
Chapter 1 THE INFORMATION AGE IN WHICH YOU LIVE Changing
... who use their knowledge to invade other people's computers o Computer virus (virus) – software that is written with malicious intent to cause annoyance or damage o Worm – type of virus that spreads itself from computer to computer usually via e-mail o Denial-of-service (DoS) attack – floods a Web si ...
... who use their knowledge to invade other people's computers o Computer virus (virus) – software that is written with malicious intent to cause annoyance or damage o Worm – type of virus that spreads itself from computer to computer usually via e-mail o Denial-of-service (DoS) attack – floods a Web si ...
The Basics of Web Threats
... A piece of software that delivers advertisements – such as pop-ups or Web links – to you without your permission. It is usually installed secretly through Trojans or as part of legitimate software that you choose to download and install. Adware can display highly-targeted ads based on data collected ...
... A piece of software that delivers advertisements – such as pop-ups or Web links – to you without your permission. It is usually installed secretly through Trojans or as part of legitimate software that you choose to download and install. Adware can display highly-targeted ads based on data collected ...
10 years APCERT - Conferences
... IT System Environment Risks/ Technology Evolves Intellectual Property ...
... IT System Environment Risks/ Technology Evolves Intellectual Property ...
Network Technology Foundations
... Firewalls can cause a bottleneck Firewalls may not allow homebased account access to the corporate e-mail server To troubleshoot firewall problems: • Verify that you are using the correct IP address and subnet mask • Check your default gateway and verify that the computer can communicate with system ...
... Firewalls can cause a bottleneck Firewalls may not allow homebased account access to the corporate e-mail server To troubleshoot firewall problems: • Verify that you are using the correct IP address and subnet mask • Check your default gateway and verify that the computer can communicate with system ...
Document
... on logical linguistic approach for automatically indexing multiple documents into single knowledge representation. A framework on IR for QA that uses this semantic matrix as its knowledge representation has been designed and implemented. ...
... on logical linguistic approach for automatically indexing multiple documents into single knowledge representation. A framework on IR for QA that uses this semantic matrix as its knowledge representation has been designed and implemented. ...
Policy Template
... Information Resources (IR): any and all computer printouts, online display devices, magnetic storage media, and all computer-related activities involving any device capable of receiving email, browsing Web sites, or otherwise capable of receiving, storing, managing, or transmitting electronic data i ...
... Information Resources (IR): any and all computer printouts, online display devices, magnetic storage media, and all computer-related activities involving any device capable of receiving email, browsing Web sites, or otherwise capable of receiving, storing, managing, or transmitting electronic data i ...
Computer Networking and Security
... Computer Networking & Security Program Pinckney Community High School The Computer Networking and Security curriculum provides a comprehensive overview of computer systems, networking, system administration and information assurance and security. This course emphasizes theoretical concepts and pract ...
... Computer Networking & Security Program Pinckney Community High School The Computer Networking and Security curriculum provides a comprehensive overview of computer systems, networking, system administration and information assurance and security. This course emphasizes theoretical concepts and pract ...
My PowerPoint for 6/24/2005 Presentation
... How robots use the network Without communication robots would ...
... How robots use the network Without communication robots would ...
Security Requirements
... that there was a hole in their security system. Allowing hackers to crack their password system and gain access to the internet free of charge. Entry into the server would give access to most of the nations emails ...
... that there was a hole in their security system. Allowing hackers to crack their password system and gain access to the internet free of charge. Entry into the server would give access to most of the nations emails ...
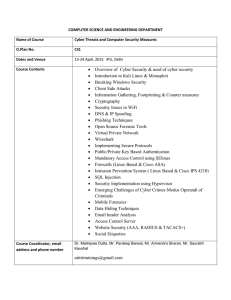
• Overview of Cyber Security & need of cyber security • Introduction
... 13-24 April, 2015 IPU, Delhi ...
... 13-24 April, 2015 IPU, Delhi ...
Chapter 2: Attackers and Their Attacks
... Certain types of local area networks (LANs), such as Ethernet, must also have another address, called the media access control (MAC) address, to move information around the network Computers on a network keep a table that links an IP address with the corresponding address In ARP spoofing, a hack ...
... Certain types of local area networks (LANs), such as Ethernet, must also have another address, called the media access control (MAC) address, to move information around the network Computers on a network keep a table that links an IP address with the corresponding address In ARP spoofing, a hack ...
here - Online Journal of Space Communication
... • Packet Radio nodes create resilient mesh • Ad hoc users gain local and long range connectivity beyond LOS • Command and control features may be remoted to field • Push/broadcast fills local cache with information that is likely to be required • Collaborative software allows multimedia interactivit ...
... • Packet Radio nodes create resilient mesh • Ad hoc users gain local and long range connectivity beyond LOS • Command and control features may be remoted to field • Push/broadcast fills local cache with information that is likely to be required • Collaborative software allows multimedia interactivit ...