master of science in computer science
... The Master of Science in Computer Science program is designed to enhance theoretical, analytical and practical skills through a solid foundation in the areas of programming, web design, database management system, networking and project management. Students will also study the cutting-edge technolog ...
... The Master of Science in Computer Science program is designed to enhance theoretical, analytical and practical skills through a solid foundation in the areas of programming, web design, database management system, networking and project management. Students will also study the cutting-edge technolog ...
C.2. Vulnerabilities
... “In 2001, a reporter for The Wall Street Journal bought a used computer in Afghanistan. He found the hard drive contained what appeared to be files from a senior al Qaeda operative. Cullison reports that he turned the computer over to the FBI. In his story published in 2004 in The Atlantic, he caref ...
... “In 2001, a reporter for The Wall Street Journal bought a used computer in Afghanistan. He found the hard drive contained what appeared to be files from a senior al Qaeda operative. Cullison reports that he turned the computer over to the FBI. In his story published in 2004 in The Atlantic, he caref ...
Computer Science 9616a, Fall 2011 Project Description Your project
... It should involve a topic relating to access control to, privacy preservation of, or integrity preservation of data in a database. It should involve some scholarly research – a few scholarly references even if you do a practical project. If you do an implementation project, you may work in pairs. Bo ...
... It should involve a topic relating to access control to, privacy preservation of, or integrity preservation of data in a database. It should involve some scholarly research – a few scholarly references even if you do a practical project. If you do an implementation project, you may work in pairs. Bo ...
Network Security Management.pdf
... and taking actions to close it are high. Using a tool to help in these tasks will reduce errors, saves costs by eliminating redundant actions, streamlines actions by prioritizing between multiple bugs and actions. It also gives you a chance to plan ahead (“what if I find a problem with a web server? ...
... and taking actions to close it are high. Using a tool to help in these tasks will reduce errors, saves costs by eliminating redundant actions, streamlines actions by prioritizing between multiple bugs and actions. It also gives you a chance to plan ahead (“what if I find a problem with a web server? ...
Computer Hacking
... websites I used gave me plenty of information about different topics; The definition of hacking, who does it, the different types of hackers, how you know if you have been hacked, the top 10 hackers and how to protect yourself from hackers. I have made the websites URLs available for you to check th ...
... websites I used gave me plenty of information about different topics; The definition of hacking, who does it, the different types of hackers, how you know if you have been hacked, the top 10 hackers and how to protect yourself from hackers. I have made the websites URLs available for you to check th ...
The Need for Information Security
... large quantities of e-mail to target • Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network • Social engineering: using social skills to convince people to reveal access credentials or other valuab ...
... large quantities of e-mail to target • Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network • Social engineering: using social skills to convince people to reveal access credentials or other valuab ...
Document
... somewhere else on the Internet. Such attacks can also generate large quantities of traffic on your network… Prevention: use a line: no ip directed-broadcast ...
... somewhere else on the Internet. Such attacks can also generate large quantities of traffic on your network… Prevention: use a line: no ip directed-broadcast ...
Security Considerations for Health Care Organizations
... U.S.C.)], the credit card and ATM industry was forced to limit personal financial risk to users (usually $50 maximum if cards used fraudulently) Approach focused on reducing risk since technology was not yet ready Limiting risk compensates for a lack of trust Many consider this approach howeve ...
... U.S.C.)], the credit card and ATM industry was forced to limit personal financial risk to users (usually $50 maximum if cards used fraudulently) Approach focused on reducing risk since technology was not yet ready Limiting risk compensates for a lack of trust Many consider this approach howeve ...
A Common Language for Computer Security Incidents
... A distinct group of attacks involving specific attackers, attacks, objectives, sites, and timing Individual(s) who use one or more attacks to ...
... A distinct group of attacks involving specific attackers, attacks, objectives, sites, and timing Individual(s) who use one or more attacks to ...
Systems Administrator needed for DoD Griffin Cyberspace Defense
... filter sensor traffic and alerts reporting activity based on Crew CC’s instruction that traffic does not need to be reviewed in a “real-time” operation by 33 NWS analysts. Monitor the effectiveness of the IDS/IPS sensor’s ability to collect and report suspicious network activity on Air Force network ...
... filter sensor traffic and alerts reporting activity based on Crew CC’s instruction that traffic does not need to be reviewed in a “real-time” operation by 33 NWS analysts. Monitor the effectiveness of the IDS/IPS sensor’s ability to collect and report suspicious network activity on Air Force network ...
attacks
... ◦ Ability to deliver value to customers ◦ Enable creation and movement of goods and services. Data in motion (online transactions) Data at rest (not online transaction) ...
... ◦ Ability to deliver value to customers ◦ Enable creation and movement of goods and services. Data in motion (online transactions) Data at rest (not online transaction) ...
INTERNET PRIVACY
... It is an international organization dedicated to protecting and serving the users of the Internet community. It has 61 agencies world wide. It provides services such as: investigation, tracking, recording, prosecution, termination of the criminal activities on the Internet. The organization has a da ...
... It is an international organization dedicated to protecting and serving the users of the Internet community. It has 61 agencies world wide. It provides services such as: investigation, tracking, recording, prosecution, termination of the criminal activities on the Internet. The organization has a da ...
OnLinePrivacy - Cal State LA
... Designed to replicate themselves and potentially cause harmful actions. Often hidden inside innocuous programs. Viruses in e-mails often masquerade as games or pictures and use beguiling subject lines (e.g., "My girlfriend nude") to encourage users to open and run them. Try to replicate themselves b ...
... Designed to replicate themselves and potentially cause harmful actions. Often hidden inside innocuous programs. Viruses in e-mails often masquerade as games or pictures and use beguiling subject lines (e.g., "My girlfriend nude") to encourage users to open and run them. Try to replicate themselves b ...
Networks - ZSIS-ITGS
... details as well as how it is being protected. A good example would be banking. There are probably no banks in existence that keep their customer’s data on paper anymore. This used to happen in the past but it has all since then been transferred to an electronic storage device. Such devices are all p ...
... details as well as how it is being protected. A good example would be banking. There are probably no banks in existence that keep their customer’s data on paper anymore. This used to happen in the past but it has all since then been transferred to an electronic storage device. Such devices are all p ...
Visualization
... to collect and analyze vast amounts of security alert data. More specifically, SIM solutions collect, analyze and correlate – in real-time – all security device information across an entire enterprise. Correlated results are then displayed on a centralized real-time console that is part of an intuit ...
... to collect and analyze vast amounts of security alert data. More specifically, SIM solutions collect, analyze and correlate – in real-time – all security device information across an entire enterprise. Correlated results are then displayed on a centralized real-time console that is part of an intuit ...
Confidentiality Undertaking - College of Pharmacists of British
... agree that my access to the PharmaNet clinical and patient database through my clinic computer system shall be on the following terms and conditions: 1. I will not access or use any clinical or patient information in the PharmaNet database or the in-pharmacy computer database for any purpose other t ...
... agree that my access to the PharmaNet clinical and patient database through my clinic computer system shall be on the following terms and conditions: 1. I will not access or use any clinical or patient information in the PharmaNet database or the in-pharmacy computer database for any purpose other t ...
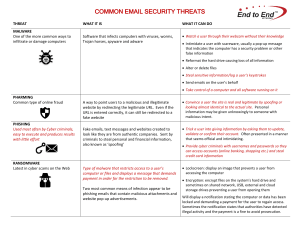
COMMON EMAIL SECURITY THREATS
... Intimidate a user with scareware, usually a pop-up message that indicates the computer has a security problem or other false information Reformat the hard drive causing loss of all information Alter or delete files Steal sensitive information/log a user’s keystrokes Send emails on the user ...
... Intimidate a user with scareware, usually a pop-up message that indicates the computer has a security problem or other false information Reformat the hard drive causing loss of all information Alter or delete files Steal sensitive information/log a user’s keystrokes Send emails on the user ...
Bandwidth Management
... Robust community features that allow students with similar music, video and programming interests to connect, share and explore on their campus ...
... Robust community features that allow students with similar music, video and programming interests to connect, share and explore on their campus ...
PowerPoint Slides
... that helps determine whether computer action is ethical Employers can distribute to employees ...
... that helps determine whether computer action is ethical Employers can distribute to employees ...
Information Privacy What is information privacy?
... Right of individuals and companies to restrict collection and use of information about them Difficult to maintain today because data is stored online Employee monitoring is using computers to observe employee computer use Legal for employers to use monitoring software programs ...
... Right of individuals and companies to restrict collection and use of information about them Difficult to maintain today because data is stored online Employee monitoring is using computers to observe employee computer use Legal for employers to use monitoring software programs ...
Introduction - Personal Web Pages
... – In CA, there is a webpage listing all people that donate to Proposition 8 ballot measure ...
... – In CA, there is a webpage listing all people that donate to Proposition 8 ballot measure ...
Slides - TAMU Computer Science Faculty Pages
... These potential actions are threats Threats that are carried out are attacks Intentional attacks are carried out by an attacker Objects of attacks are assets ...
... These potential actions are threats Threats that are carried out are attacks Intentional attacks are carried out by an attacker Objects of attacks are assets ...
Study Material for MCA (SEM-V) Subject: Cyber Security and
... Today corporations like government often spy on the enemy. ...
... Today corporations like government often spy on the enemy. ...
Security+ Guide to Network Security Fundamentals
... Controls access to network by analyzing incoming/outgoing packets and letting them pass or not based on IP addresses of source and destination ...
... Controls access to network by analyzing incoming/outgoing packets and letting them pass or not based on IP addresses of source and destination ...